computers to encrypt data. The certificate holder also has a private key, which alone can
decrypt the data, guaranteeing data privacy between the machines. A certificate may be
authoritatively
signed
: a trusted firm or organization can apply a digital signature to a
certificate, giving you confidence that the computer with that certificate is what it claims to be.
A new Bandura Cyber TIG has a single
self-signed
certificate
used to encrypt communications
between the Bandura Cyber TIG and your web browser, but this does not provide
authentication. You can install an authoritatively signed certificate in your Bandura Cyber TIG,
and you can install public key certificates in your web browsers, authenticating the
administrative computers.
By default, the Bandura Cyber TIG will communicate with any computer, since the Bandura
Cyber TIG does not require them to have public key certificates. In this case, security is based
on administrator account passwords and optional network restrictions. This basic security may
be adequate for many users, and be aware that enhancing this security requires considerable
effort, coordination, follow-up activity, and possibly expense.
Your Bandura Cyber TIG administration account must be assigned the Crypto Admin Role to
make any changes in this section.
You can perform the following tasks from this menu:
●
Generate
New
Self-Signed
Certificate
:
Replace the Bandura Cyber TIG's existing
Public Key Certificate.
●
View
Existing
Certificate
:
Shows your current Public Key Certificate.
●
Generate
CSR
:
Make a Certificate Signing Request, used to begin the process of
getting an authoritatively signed Public Key Certificate from a Certificate Authority.
●
Import
Certificate
:
Install a public key certificate in your Bandura Cyber TIG. Use this if
you created the Bandura Cyber TIG's Certificate on another computer.
●
Export
Certificate
:
Save a copy of the Bandura Cyber TIG's public key certificate on
your computer.
●
Upload
CA
Certificate:
Upload a Certificate Authority Root Certificate for use in
verifying client certificates. This needs to be the same CA which signed your clients'
certificates.
●
Upload
Certificate
Revocation
List
:
Upload a list of invalid client Public Key
Certificates. This is generated by the same CA referenced by Upload CA Certificate.
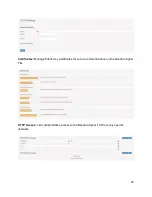
3.7.8.2.1 View Existing Certificate
Some information to note on this certificate:
● Issuer and Subject are the same. This indicates a self-signed certificate.
● Public Key Algorithm is 2048 bit RSA encryption, which is strong.
64