Configure
Except on the first page, right running head:
Heading1 or Heading1NewPage text (automatic)
147
Alcatel-Lucent
Beta
Beta
OmniAccess 5740 Unified Services Gateway Web GUI Users Guide
Step 5:
Click
Next
.
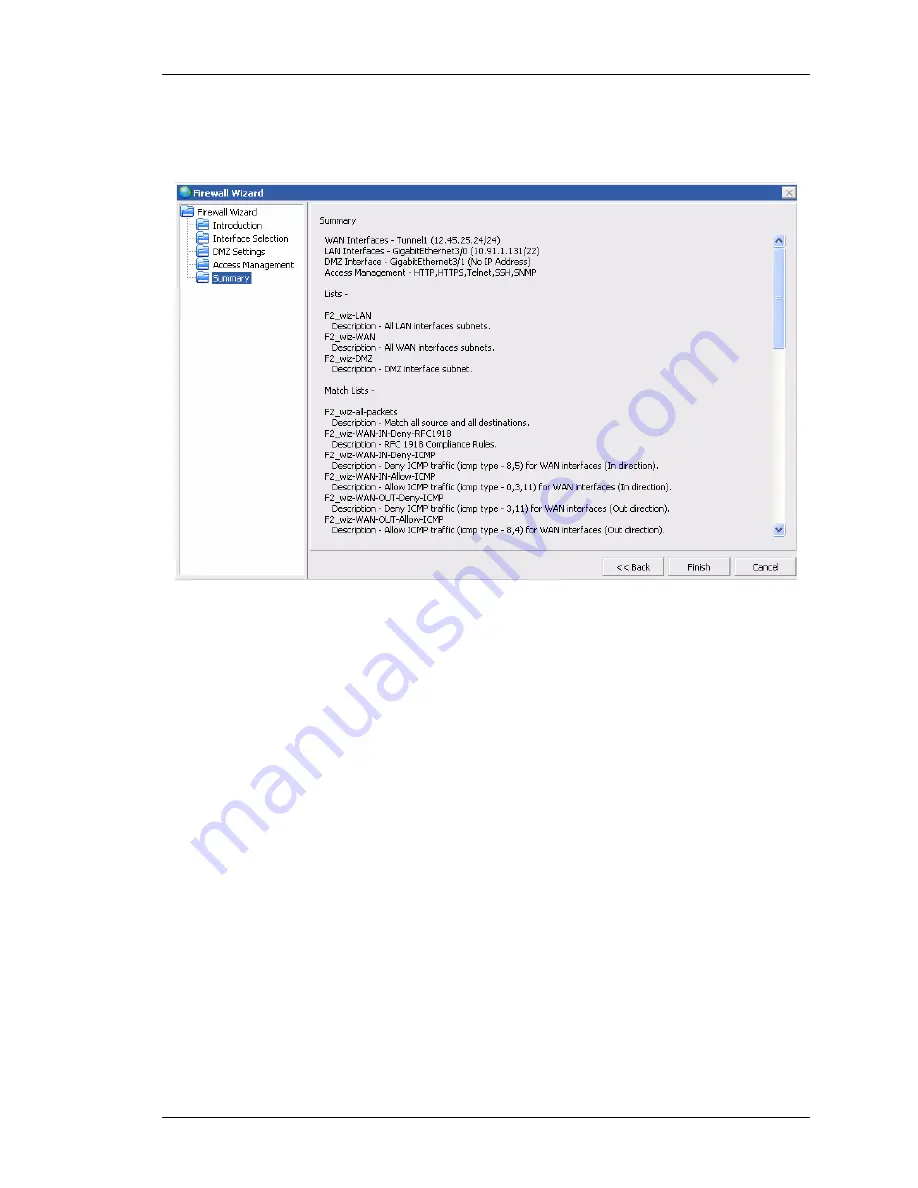
Summary
window displays the summary of the firewall policy
configuration.
Figure 81: Firewall: Firewall Wizard - Summary
The Summary window displays the details of the firewall Policy being configured:
The LAN and the WAN interfaces, DMZ interface (if any), the management
protocols being configured for the firewall policy. It also displays the filters and the
rules (lists and the match-lists) associated with the filter, and the DoS attack that
are auto generated by the wizard.
Step 6:
Click
Finish
to save the configuration and generate the firewall policy.
Step 7:
A status bar is displayed showing the firewall policy creation. Once the
firewall policy is configured successfully, a successful message is displayed.
The filters, DOS attack, and the firewall policy auto configured by the wizard is
displayed in the
Filters
,
DoS Attack
and
Firewall Policy
tabs as shown below.
















































