52
4. Select
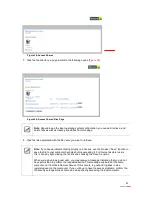
Applications, Pinholes and DMZ
; a page opens showing hosted applications.
Note:
If the computer you want to select is unlisted because it is powered off and the “hide
inactive devices” option is enabled; you still can select it as long as it is on the same
network and you know its IP address. Replace “Enter IP address” with the intended IP
address, then click
Choose
.
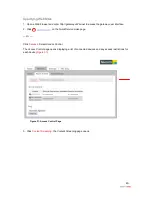
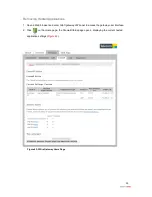
5. Select the hosting computer if you do not see the pinhole you want to remove in the list.
6. Scroll to the
Edit firewall settings for this computer
pane (
Figure 41
).
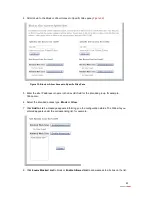
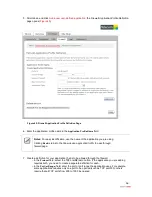
7. Select from the
Application List
panel the application(s) you want to host.
Note:
To select multiple applications, hold down the [Shift] or [Ctrl] keys while making your
selections. Using the [Shift] key lets you make your selections in a contiguous order while
the [Ctrl] key selects the groups in a random order.
8. Click
Add
; the application(s) you selected appears in the
Hosted Applications
panel.
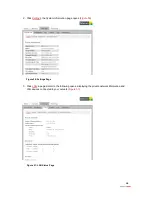
9. Click
Save
.