ZyWALL 5 User’s Guide
622
Appendix L Firewall Commands
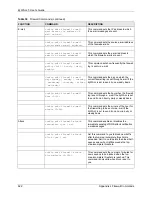
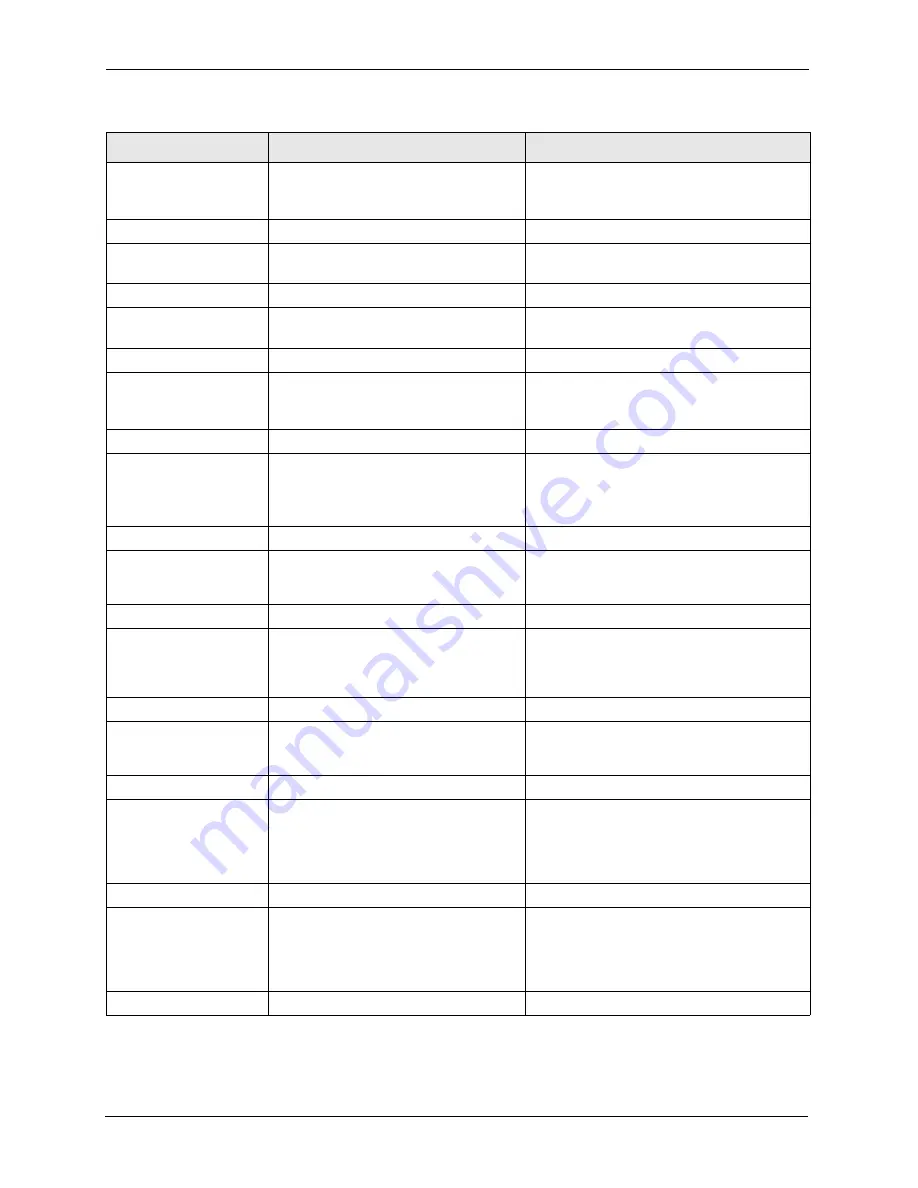
config edit firewall e-mail
mail-server <ip address of
mail server>
This command sets the IP address to which
the e-mail messages are sent.
config edit firewall e-mail
return-addr <e-mail address>
This command sets the source e-mail address
of the firewall e-mails.
config edit firewall e-mail
email-to <e-mail address>
This command sets the e-mail address to
which the firewall e-mails are sent.
config edit firewall e-mail
policy <full | hourly | daily |
weekly>
This command sets how frequently the firewall
log is sent via e-mail.
config edit firewall e-mail
day <sunday | monday | tuesday
| wednesday | thursday | friday
| saturday>
This command sets the day on which the
current firewall log is sent through e-mail if the
ZyWALL is set to send it on a weekly basis.
config edit firewall e-mail
hour <0-23>
This command sets the hour when the firewall
log is sent through e- mail if the ZyWALL is set
to send it on an hourly, daily or weekly basis.
config edit firewall e-mail
minute <0-59>
This command sets the minute of the hour for
the firewall log to be sent via e- mail if the
ZyWALL is set to send it on a hourly, daily or
weekly basis.
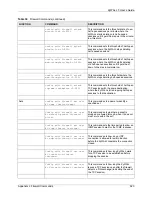
Attack
config edit firewall attack
send-alert <yes | no>
This command enables or disables the
immediate sending of DOS attack notification
e-mail messages.
config edit firewall attack
block <yes | no>
Set this command to yes to block new traffic
after the tcp-max-incomplete threshold is
exceeded. Set it to no to delete the oldest half-
open session when traffic exceeds the tcp-
max-incomplete threshold.
config edit firewall attack
block-minute <0-255>
This command sets the number of minutes for
new sessions to be blocked when the tcp-
max-incomplete threshold is reached. This
command is only valid when block is set to
yes.
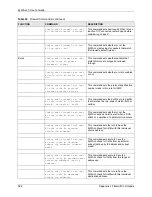
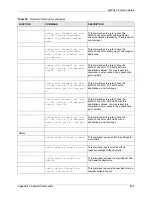
Table 30
Firewall Commands (continued)
FUNCTION
COMMAND
DESCRIPTION
Summary of Contents for ZyXEL ZyWALL 5
Page 1: ...ZyWALL 5 Internet Security Appliance User s Guide Version 3 64 3 2005 ...
Page 2: ......
Page 26: ...ZyWALL 5 User s Guide 24 ...
Page 44: ...ZyWALL 5 User s Guide 42 ...
Page 86: ...ZyWALL 5 User s Guide 84 Chapter 3 Wizard Setup ...
Page 96: ...ZyWALL 5 User s Guide 94 Chapter 4 LAN Screens ...
Page 102: ...ZyWALL 5 User s Guide 100 Chapter 5 Bridge Screens ...
Page 130: ...ZyWALL 5 User s Guide 128 Chapter 7 WAN Screens Figure 45 WAN PPPoE Encapsulation ...
Page 138: ...ZyWALL 5 User s Guide 136 Chapter 7 WAN Screens Figure 50 Dial Backup Setup ...
Page 144: ...ZyWALL 5 User s Guide 142 Chapter 7 WAN Screens ...
Page 152: ...ZyWALL 5 User s Guide 150 Chapter 8 DMZ Screens ...
Page 179: ...ZyWALL 5 User s Guide Chapter 10 Firewall Screens 177 Figure 73 My Service Rule Configuration ...
Page 220: ...ZyWALL 5 User s Guide 218 Chapter 13 Introduction to IPSec ...
Page 238: ...ZyWALL 5 User s Guide 236 Chapter 14 VPN Screens Figure 110 VPN Rules IKE Network Policy Edit ...
Page 261: ...ZyWALL 5 User s Guide Chapter 15 Certificates 259 Figure 122 My Certificate Details ...
Page 280: ...ZyWALL 5 User s Guide 278 Chapter 16 Authentication Server Figure 133 Local User Database ...
Page 317: ...ZyWALL 5 User s Guide Chapter 19 Bandwidth Management 315 ...
Page 318: ...ZyWALL 5 User s Guide 316 Chapter 19 Bandwidth Management ...
Page 352: ...ZyWALL 5 User s Guide 350 Chapter 21 Remote Management ...
Page 366: ...ZyWALL 5 User s Guide 364 Chapter 23 Logs Screens Figure 188 Log Settings ...
Page 389: ...ZyWALL 5 User s Guide Chapter 24 Maintenance 387 Figure 210 Restart Screen ...
Page 390: ...ZyWALL 5 User s Guide 388 Chapter 24 Maintenance ...
Page 416: ...ZyWALL 5 User s Guide 414 Chapter 27 WAN and Dial Backup Setup ...
Page 432: ...ZyWALL 5 User s Guide 430 Chapter 30 DMZ Setup ...
Page 492: ...ZyWALL 5 User s Guide 490 Chapter 37 System Information Diagnosis ...
Page 508: ...ZyWALL 5 User s Guide 506 Chapter 38 Firmware and Configuration File Maintenance ...
Page 520: ...ZyWALL 5 User s Guide 518 Chapter 40 Remote Management ...
Page 536: ...ZyWALL 5 User s Guide 534 Chapter 42 Troubleshooting Figure 343 Java Sun ...
Page 564: ...ZyWALL 5 User s Guide 562 Appendix C IP Subnetting ...
Page 570: ...ZyWALL 5 User s Guide 568 Appendix E PPTP ...
Page 571: ...ZyWALL 5 User s Guide 569 ...
Page 572: ...ZyWALL 5 User s Guide 570 ...
Page 590: ...ZyWALL 5 User s Guide 588 Appendix G Triangle Route ...
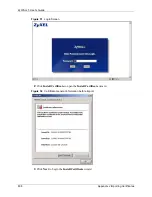
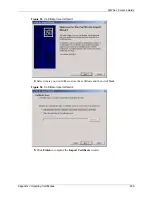
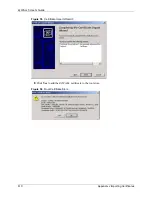
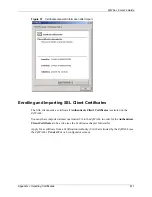
Page 620: ...ZyWALL 5 User s Guide 618 Appendix J Importing Certificates ...
Page 622: ...ZyWALL 5 User s Guide 620 Appendix K Command Interpreter ...
Page 628: ...ZyWALL 5 User s Guide 626 Appendix L Firewall Commands ...
Page 632: ...ZyWALL 5 User s Guide 630 Appendix M NetBIOS Filter Commands ...
Page 638: ...ZyWALL 5 User s Guide 636 Appendix O Brute Force Password Guessing Protection ...
Page 660: ...ZyWALL 5 User s Guide 658 Appendix Q Log Descriptions ...