31
Table of Contents
Congratulations! You’re done! Now your mobile client is serialized and can
connect to the selected Locks and devices connected to them.
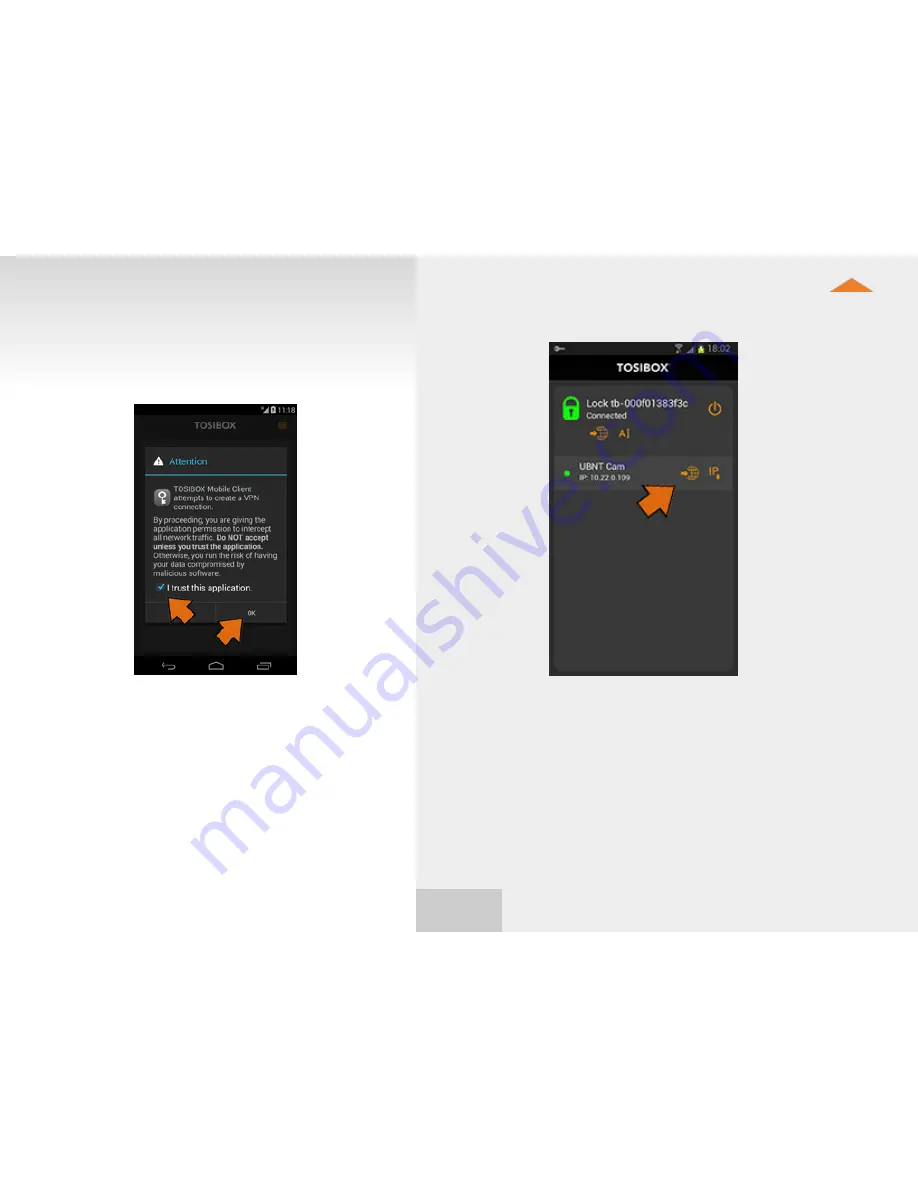
You can open network devices through your web browser (if available)
by clicking the the appropriate globe icon. Note: If your network device
does not have a web interface (HTTP / HTTPS), you can use a third party
application to make the connection. You can find third party applications
from the Google Play store or App Store. You can copy the network device
IP address to the device’s clipboard by clicking the IP button. Doing so will
allow you to paste the IP address to a third party application.
Table of Contents
31
13. Check the I trust this
application dialogue
box and click OK.



































