12
Table of Contents
5.2 connecting Locks
With TOSIBOX
®
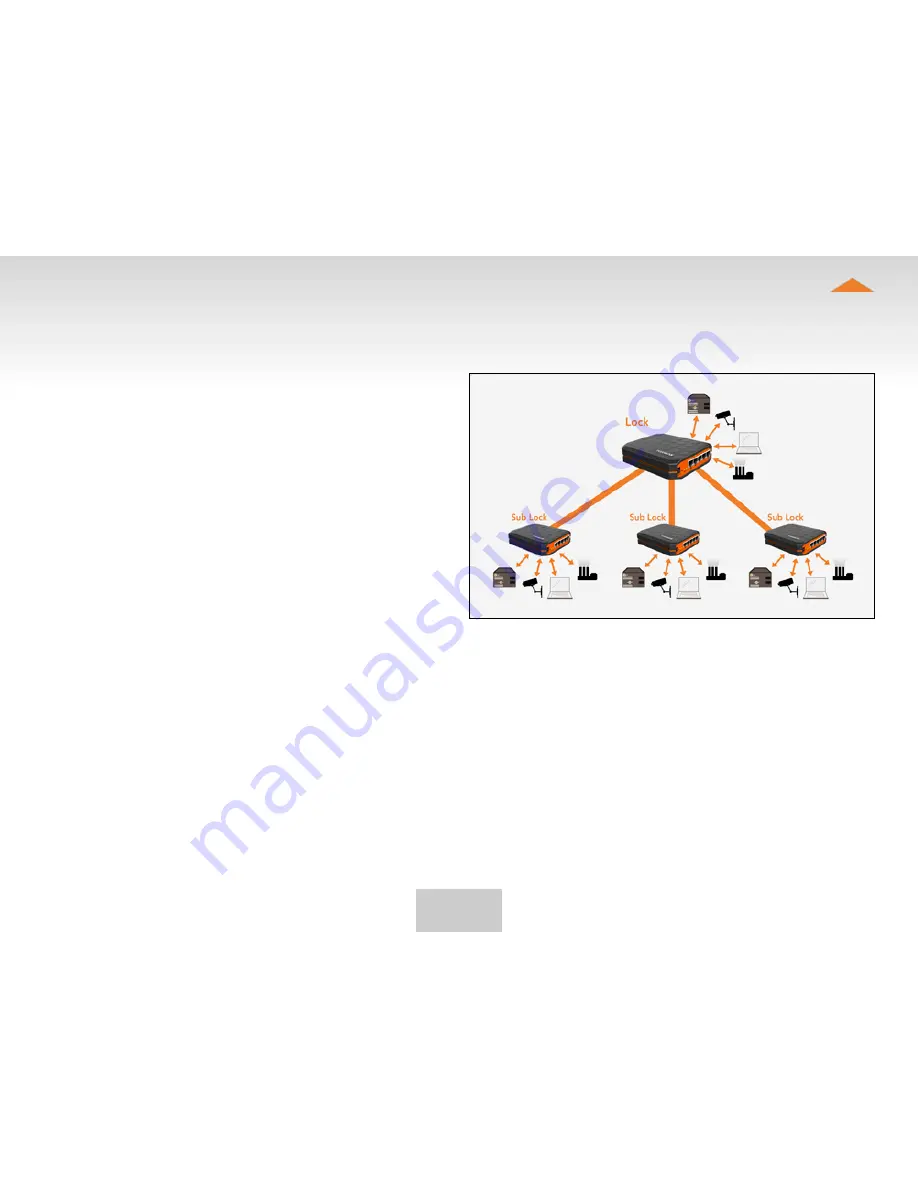
Locks one can connect machines in
separate places so that the connection between them is
permanently and automatically on. One example is a real-
time protected connection between home and office. This
is made with a Lock/Sub Lock solution (see accompanying
image Connecting Locks). Up to 10 Sub Locks can be
connected to one Lock.
First serialize the Key to all the Locks to be connected
as described in section “TOSIBOX
®
Lock and Key
serialization”.
connecting Locks
Insert a serialized Key to the USB port of the computer.
1.
Choose ”Devices” from the Key user menu and ”Connect Locks”
2.
from the drop down menu.
Choose the Locks that you want to connect together and choose
3.
”Next”.
Choose the Lock that you want to attach the Sub Locks. The other
4.
Locks will be changed to Sub Lock operating mode.
Confirm the selection > Save > serializing is ready.
5.
note:
The connections will come into effect when the
Locks have access to the Internet.
The Sub Lock ends of the connection in the picture do not
have their own DHCP service. If the connection between
the Lock and the Sub Lock is interrupted, the network
devices connected with the Sub Lock can no longer
connect to the Internet and each other.



























