Create and install a device certificate from the control panel or Web Image Monitor.
2. Enabling SSL/TLS:
Enable the SSL/TLS setting using Web Image Monitor.
Configuration flow when using an authority issued certificate
1. Creating a device certificate and applying to the authority:
After creating a device certificate on Web Image Monitor, apply to the certificate authority.
The application procedure after creating the certificate depends on the certificate authority.
Follow the procedure specified by the certificate authority.
2. Installing the device certificate:
Install the device certificate using Web Image Monitor.
3. Enabling SSL/TLS:
Enable the SSL/TLS setting using Web Image Monitor.
• To check whether SSL/TLS configuration is enabled, enter "https://(the machine's IP address or
host name)/" in your Web browser's address bar to access this machine. If the "The page cannot
be displayed" message appears, check the configuration because the current SSL/TLS
configuration is invalid.
Enabling SSL/TLS
After installing the device certificate in the machine, enable the SSL/TLS setting.
This procedure is used for a self-signed certificate or a certificate issued by a certificate authority.
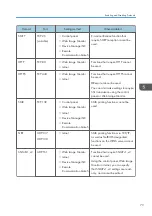
1.
Log in as the network administrator from Web Image Monitor.
2.
Point to [Device Management], and then click [Configuration].
3.
Click [SSL/TLS] under "Security".
4.
For IPv4 and IPv6, select "Active" if you want to enable SSL/TLS.
5.
Select the encryption communication mode for "Permit SSL/TLS Communication".
6.
If you want to disable a protocol, click [Inactive] next to "TLS1.2", "TLS1.1", "TLS1.0", or
"SSL3.0".
At least one of these protocols must be enabled.
7.
Under "Encryption Strength Setting", specify the strength of encryption to be applied for
"AES", "3DES", and/or "RC4". You must select at least one check box.
Note that the availability of encryption strengths will vary depending on the settings you have
specified for "TLS1.2", "TLS1.1", "TLS1.0", or "SSL3.0".
8.
Click [OK].
Configuring SSL/TLS Settings
87
Summary of Contents for PRO C9100
Page 2: ......
Page 8: ...List of Operation Privileges for Address Books 229 INDEX 231 6...
Page 24: ...1 Getting Started 22...
Page 72: ...4 Preventing Leakage of Information from Machines 70...
Page 116: ...5 Enhanced Network Security 114...
Page 176: ...6 Managing the Machine 174...
Page 188: ...7 Troubleshooting 186...
Page 235: ......
Page 236: ...EN GB EN US EN AU M238 1022 2014...