Access Log Item
Log Type Attribute
Content
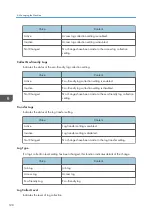
Access Violation
Access Violation
Details of failed access attempts.
Lockout
Lockout
Details of lockout activation.
Firmware: Update
Firmware: Update
Details of firmware updates.
Firmware: Structure
Change
Firmware: Structure
Change
Details of structure changes that occurred
when an SD card was inserted or removed, or
when an unsupported SD card was inserted.
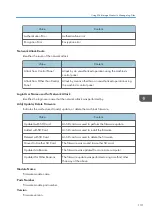
Firmware: Structure
Firmware: Structure
Details of checks for changes to firmware
module structure made at times such as when
the machine was switched on.
Machine Data
Encryption Key
Change
Machine Data
Encryption Key
Change
Details of changes made to encryption keys
using "Machine Data Encryption Key
Change" setting.
Firmware: Invalid
Firmware: Invalid
Details of checks for firmware validity made at
times such as when the machine was switched
on.
Date/Time Change
Date/Time Change
Details of changes made to date and time
settings.
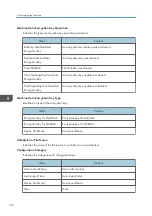
Password Change
Password Change
Details of changes made to the login
password.
Administrator Change
Administrator Change
Details of changes of administrators.
Address Book Change Address Book Change Details of changes made to address book
entries.
Machine
Configuration
Machine
Configuration
Log of changes to the machine's settings.
Back Up Address
Book
Back Up Address
Book
Log of when data in the Address Book is
backed up.
Restore Address Book
Restore Address Book
Log of when data in the Address Book is
restored.
Counter Clear Result:
Selected User(s)
Counter Clear Result:
Selected User(s)
Log of when the counter for an individual user
is cleared.
Using Web Image Monitor to Manage Log Files
117
Summary of Contents for PRO C9100
Page 2: ......
Page 8: ...List of Operation Privileges for Address Books 229 INDEX 231 6...
Page 24: ...1 Getting Started 22...
Page 72: ...4 Preventing Leakage of Information from Machines 70...
Page 116: ...5 Enhanced Network Security 114...
Page 176: ...6 Managing the Machine 174...
Page 188: ...7 Troubleshooting 186...
Page 235: ......
Page 236: ...EN GB EN US EN AU M238 1022 2014...