320
Device Information Confirmation
|
6.1.10.
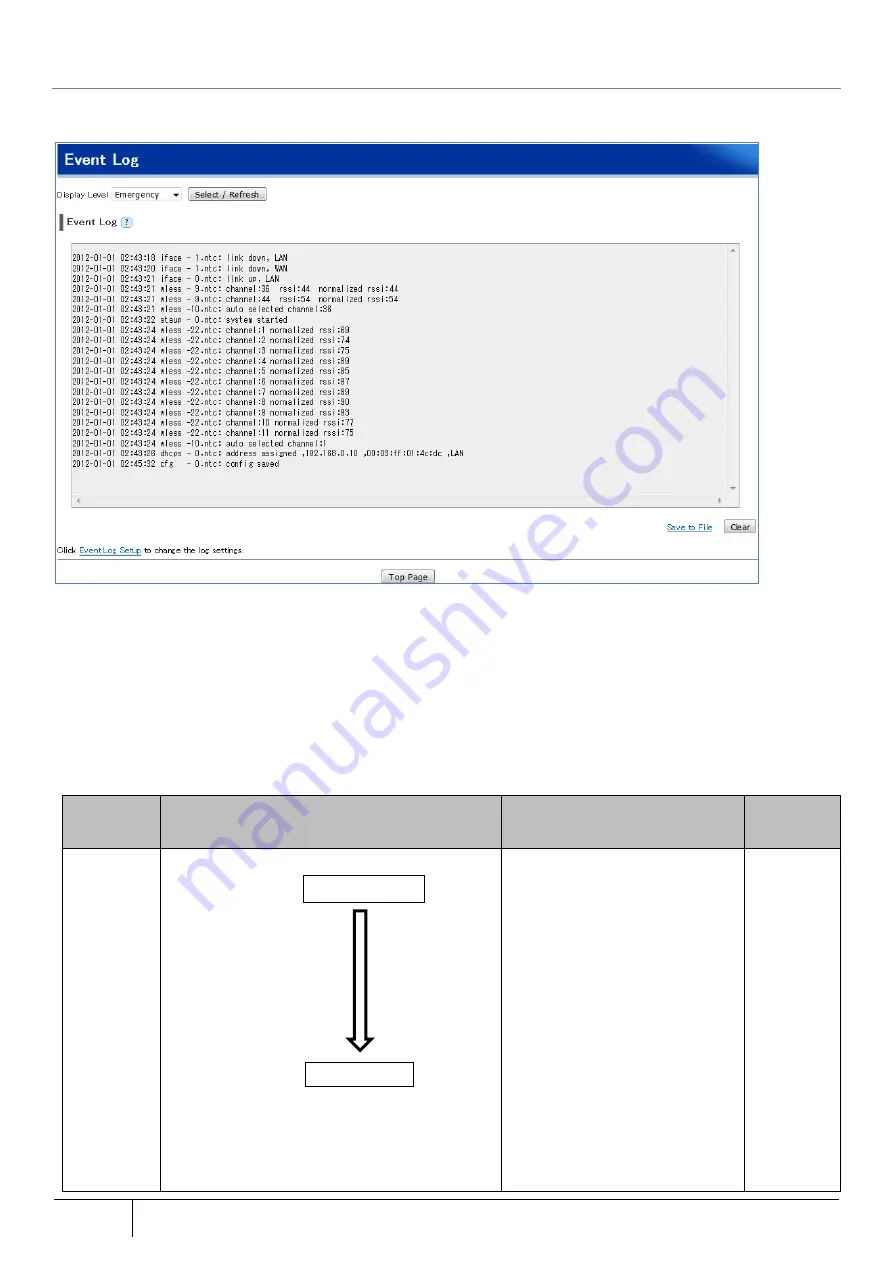
Event Log
Event logs can be checked on the Web setting.
1. Open the [Event Log] screen from [TOP]-[Maintenance]-[Information].
2. Select the level to display the event log from [Display Level].
3. Click the [Select/Refresh] button.
[Save Event Log to PC]
By clicking "Save to File", the event log can be saved to a PC or similar device.
Setting
Item
Value
Remarks
Initial Value
Select Log
Emergency E
vent volume: small
Alert
Critical
Error
Warning
Notice
Informational
Debug
Event volume: big
Select the level to display the
event log. Levels that can be
changed by log level is shown on
the left. The event log level can
be changed according to the
severity and urgency of the event.
For example, when set to
Emergency level, only events
corresponding to Emergency level
are displayed.
When set to the Informational
level, all the top events can be
displayed.
Emergency
















































