System Overview
18
NAS 1500s and 500s Administration Guide
User interfaces
There are several user interfaces that administrators can use to access and manage the NAS
server. Two of these interfaces are:
■
NAS server WebUI
■
NAS server desktop
Each interface contains the same or similar capabilities, but presents them in a different
manner. Each of these interfaces are illustrated in the following sections.
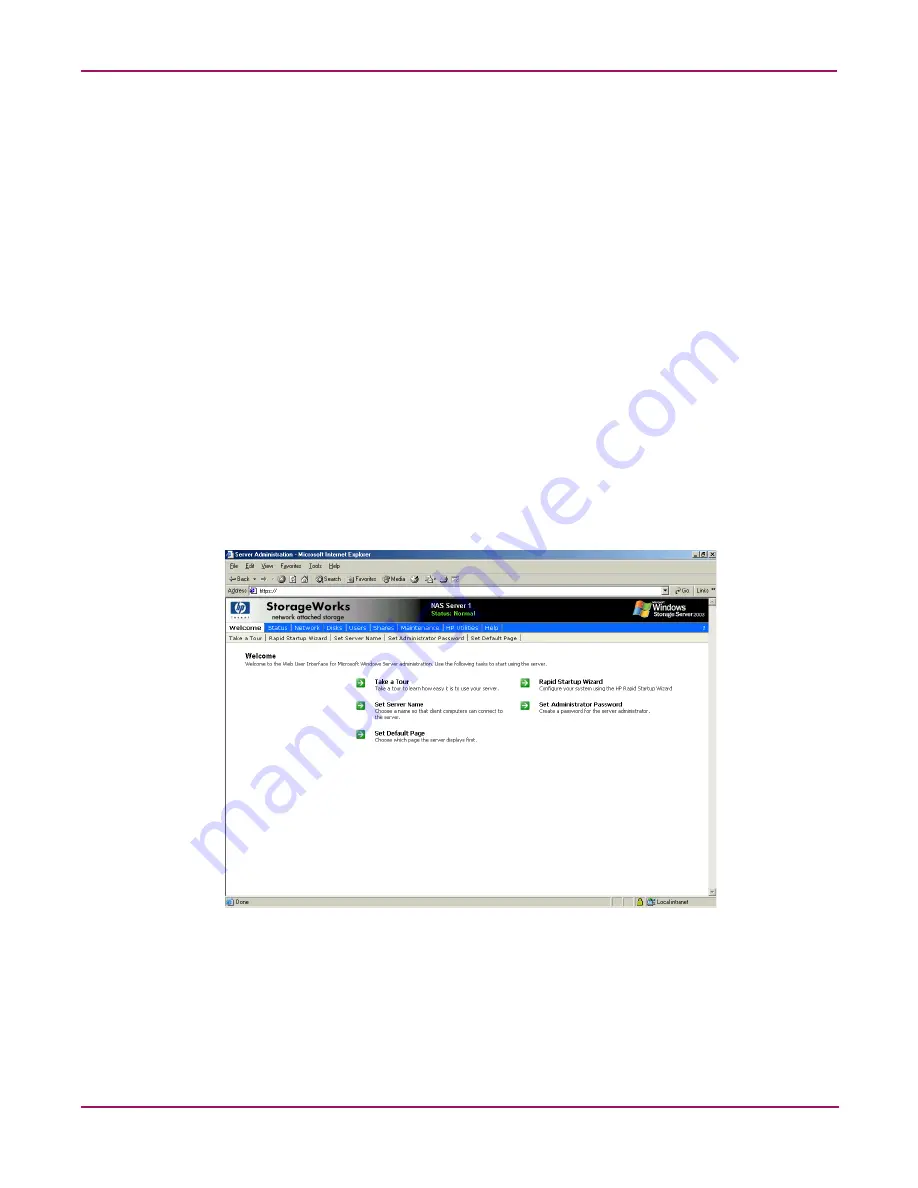
NAS server web-based user interface
The WebUI provides for system administration, including user and group management, share
management, and local storage management.
Refer to the HP StorageWorks NAS server installation guide for detailed information on using
the Rapid Startup Wizard for initial setup.
To access the WebUI, launch a Web browser and enter the following in the address field:
https://<your NAS machine name or IP Address>:3202/
The default user name is
Administrator
. The default password is
hpinvent
. Online
help for the WebUI is available by clicking the Help tab on the primary WebUI screen.
The primary screen of the WebUI is shown in
Figure 2
.
Figure 2: Primary WebUI screen
As shown in
Figure 2
, the following areas are administered through this interface:
Menu tabs
Status
The Status option displays alerts generated by the WebUI.