149
Configuring service management
1.
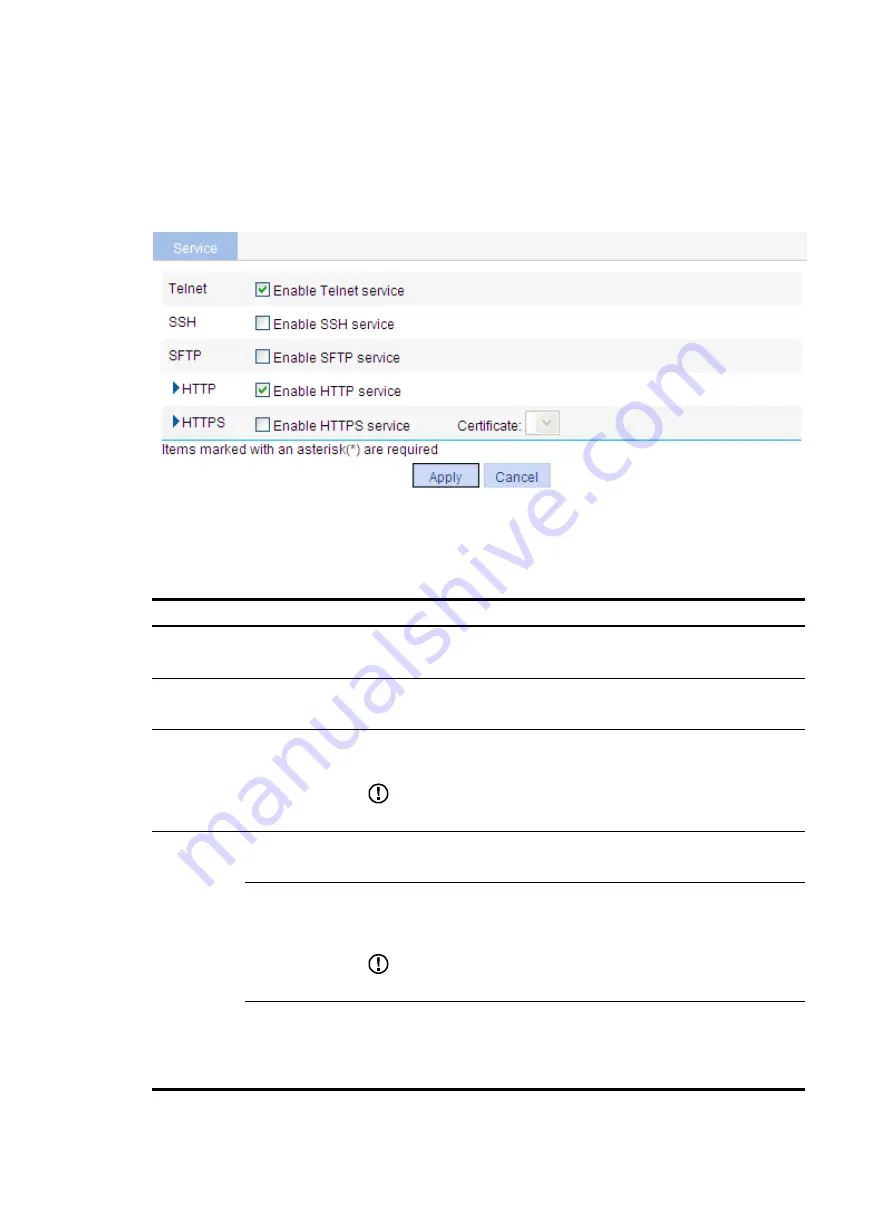
Select
Network
>
Service
from the navigation tree to enter the service management configuration
page, as shown in
.
Figure 155
Service management
2.
Enable or disable various services on the page as described in
3.
Click
Apply
.
Table 64
Configuration items
Item Description
Telnet
Enable Telnet
service.
Specifies whether to enable the Telnet service.
The Telnet service is enabled by default.
SSH
Enable SSH
service.
Specifies whether to enable the SSH service.
The SSH service is disabled by default.
SFTP
Enable SFTP
service.
Specifies whether to enable the SFTP service.
The SFTP service is disabled by default.
IMPORTANT:
When you enable the SFTP service, the SSH service must be enabled.
HTTP
Enable HTTP
service.
Specifies whether to enable the HTTP service.
The HTTP service is disabled by default.
Port Number.
Sets the port number for HTTP service.
You can view this configuration item by clicking the expanding button in
front of
HTTP
.
IMPORTANT:
When you modify a port, make sure that the port is not used by other service.
ACL.
Associates the HTTP service with an ACL. Only the clients that pass the ACL
filtering are permitted to use the HTTP service.
You can view this configuration item by clicking the expanding button in
front of
HTTP
.
Summary of Contents for WA2612-AGN
Page 106: ...93 Figure 90 Create a static MAC address entry ...
Page 126: ...113 Figure 116 Information about an IGMP snooping multicast entry ...
Page 187: ...174 Figure 174 Firefox web browser setting ...
Page 219: ...206 Figure 202 Common configuration area 6 Configure the advanced parameters ...
Page 243: ...230 Number of users Real time accounting interval in minutes 500 to 999 12 1000 15 ...
Page 278: ...265 Figure 266 Network diagram LAN Segment ...
Page 339: ...326 Figure 348 Configure the wireless card I ...
Page 340: ...327 Figure 349 Configure the wireless card II ...
Page 346: ...333 Figure 357 Configure the wireless card II ...
















































