Copyright (c) Fire4 Systems Inc, 2019. All rights reserved
6
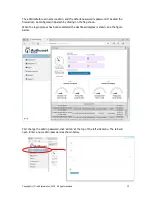
When the firewall had been installed there is no connection from network computers to the
Internet, and any attempt to access network computers from the Internet is blocked. Blocking
access from the Internet to the network computers will thwart a hacker who attempts to access
the network from the Internet. It is possible to add rules to permit certain types of access from
the Internet to the network computers, however this should be avoided as each access rule is a
potential point of access for a hacker.
At first the inability of network computers to have Internet access is seen as a problem, however
this is of great benefit by blocking the hacker who tries to install a trojan on a users computer. A
rule can be added to give all computers access to the whole Internet, however it is much safer to
permit access only to those websites that the users will need to access for their day to day tasks.
This approach has the benefit that if a trojan is accidentally installed on a users computer then it
cannot call the hacker because the firewall will block the outbound call, as computers can only
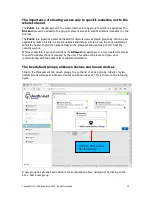
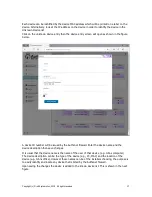
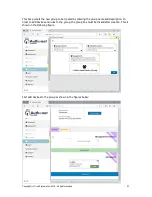
communicate with permitted websites. The diagram below illustrates a trojan virus installed on a
users computer, which is blocked by the firewall when trying to contact the hacker.
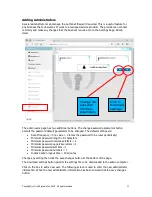
Most business and government departments will have difficulty with a one-rule-fits-all regarding
the websites that computers are allowed to access. For this reason the Authonet firewall permits
the creation of multiple groups where each group can have access to named websites. Groups
can be created for business departments, like management, production, financial and sales. Each
group can have a different list of websites that the computers (and users) in that group are
permitted to access.
An added bonus of permitting access only to specific website is that access is blocked to websites
that may distract employees, such as social media. This can improve productivity for some
businesses.
Internet
Firewall
User desktop
Servers and devices
Attempted
attack on
servers by
tojjan
Direct attack to server
blocked by firewall
Firewall
blocks
the
trojans
remote
access
to the
desktop
Internet
Internet
Firewall
User desktop
Servers and devices
Attempted
attack on
servers by
tojjan
Direct attack to server
blocked by firewall
Firewall
blocks
the
trojans
remote
access
to the
desktop