Copyright (c) Fire4 Systems Inc, 2019. All rights reserved
19
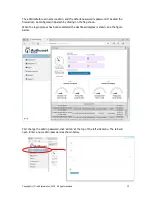
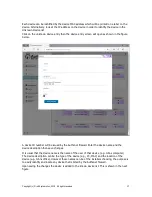
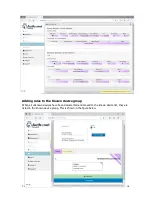
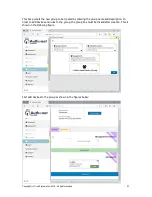
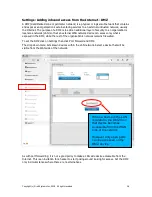
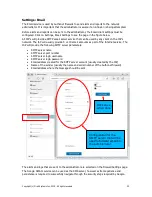
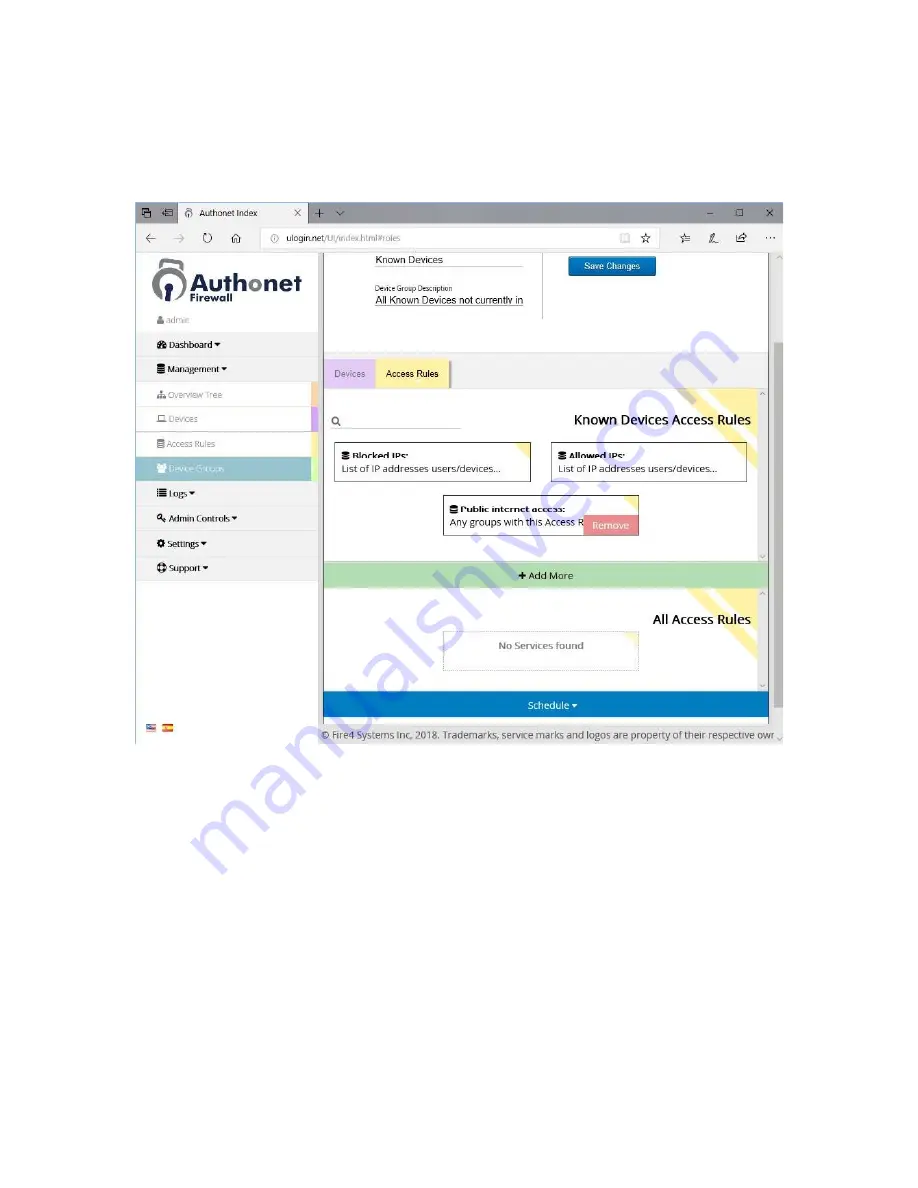
Rules can now be added to the known device group. There is one rule which is ready to use, this
is the Internet access rule. This is shown in the figure below.
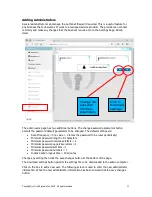
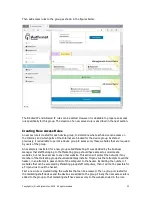
Even though the Public Internet Access rule gives full Internet access, access to specific websites
can be blocked by creating a blocked IP rule. The Blocked IP rule overrides the access rule.
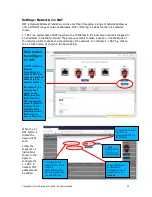
However as stated previously it is never desirable to give a user full Internet access because if
that user clicks on an email link which installs a trojan virus, then there is nothing to stop the
trojan calling the hacker, and giving the hacker full access to the users computer.
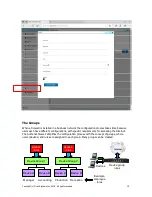
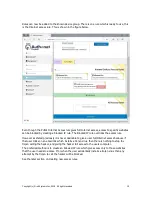
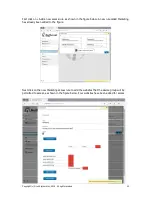
The preferred method is to create an Allowed IP rule which give access only to those websites
that the user needs to access. If or when the user accidentally installs a trojan virus then any
attempt by the trojan to call the hacker will be blocked.
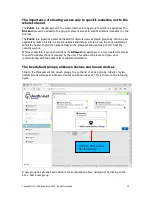
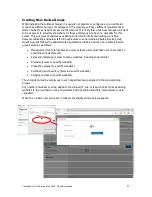
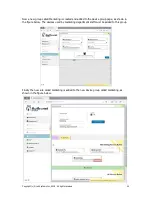
See the later section on creating new access rules.