Chapter 24 IP Source Guard
XS3900-48F User’s Guide
203
3
Configure trusted and untrusted ports, and specify the maximum number of DHCP packets that
each port can receive per second.
4
Configure static bindings.
24.1.3 ARP Inspection Overview
Use ARP inspection to filter unauthorized ARP packets on the network. This can prevent many kinds
of man-in-the-middle attacks, such as the one in the following example.
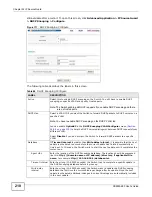
Figure 107
Example: Man-in-the-middle Attack
In this example, computer B tries to establish a connection with computer A. Computer X is in the
same broadcast domain as computer A and intercepts the ARP request for computer A. Then,
computer X does the following things:
• It pretends to be computer A and responds to computer B.
• It pretends to be computer B and sends a message to computer A.
As a result, all the communication between computer A and computer B passes through computer
X. Computer X can read and alter the information passed between them.
24.1.3.1 ARP Inspection and MAC Address Filters
When the Switch identifies an unauthorized ARP packet, it automatically creates a MAC address
filter to block traffic from the source MAC address and source VLAN ID of the unauthorized ARP
packet. You can configure how long the MAC address filter remains in the Switch.
These MAC address filters are different than regular MAC address filters (
).
• They are stored only in volatile memory.
• They do not use the same space in memory that regular MAC address filters use.
• They appear only in the ARP Inspection screens and commands, not in the MAC Address
Filter screens and commands.
24.1.3.2 Trusted vs. Untrusted Ports
Every port is either a trusted port or an untrusted port for ARP inspection. This setting is
independent of the trusted/untrusted setting for DHCP snooping. You can also specify the maximum
rate at which the Switch receives ARP packets on untrusted ports.
The Switch does not discard ARP packets on trusted ports for any reason.
A
X
B
Содержание XS-3900-48F
Страница 15: ...15 PART I User s Guide ...
Страница 16: ...16 ...
Страница 48: ...Chapter 2 Tutorials XS3900 48F User s Guide 48 ...
Страница 62: ...Chapter 4 The Web Configurator XS3900 48F User s Guide 62 ...
Страница 63: ...63 PART II Technical Reference ...
Страница 64: ...64 ...
Страница 227: ...Chapter 26 VLAN Mapping XS3900 48F User s Guide 227 ...
Страница 320: ...Appendix A Common Services XS3900 48F User s Guide 320 ...
Страница 332: ...Index XS3900 48F User s Guide 332 ...