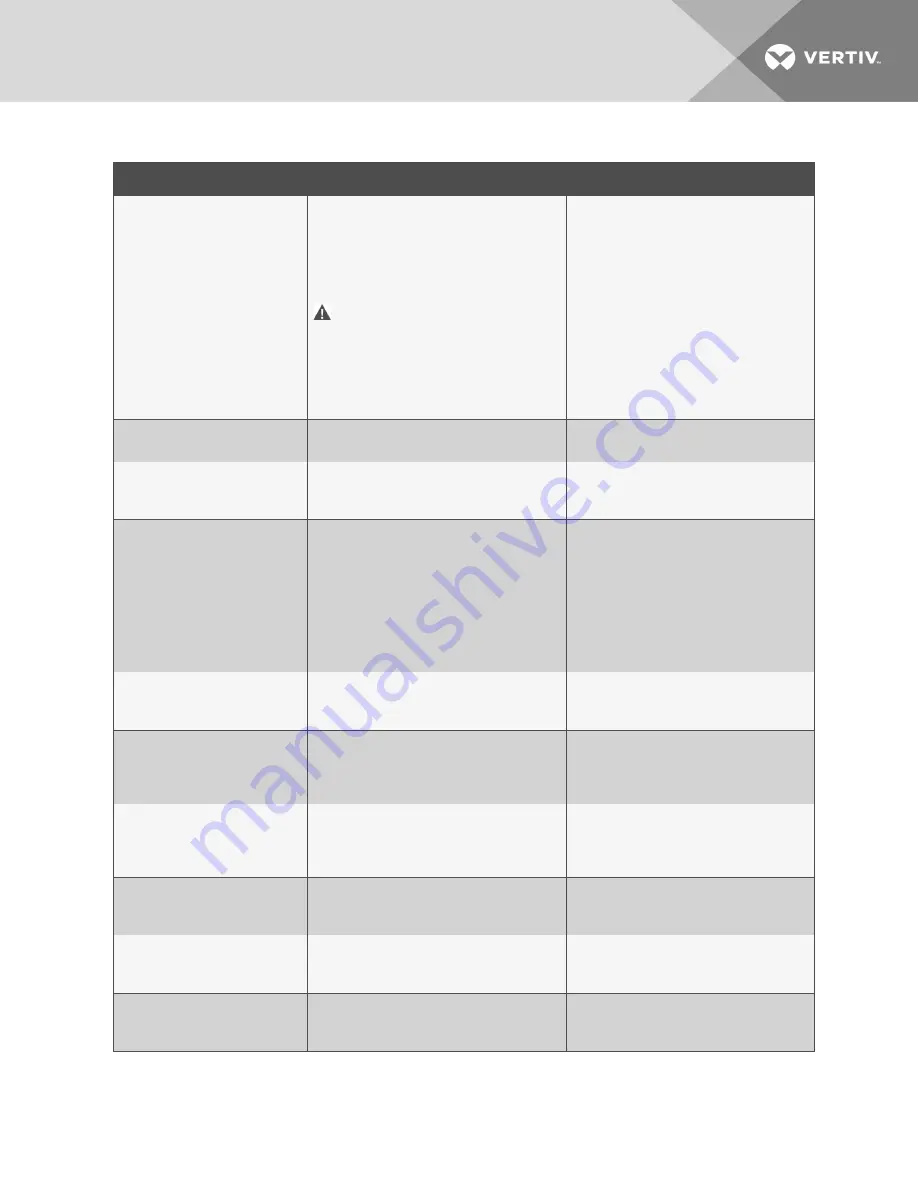
ITEM
DESCRIPTION
REFERENCE
Remote Write Web Access
Disable to require all updates to the device and
card be made through a local interface, via an
Autoconfiguration connection with a PC
directly connected to the Unity card or
through the device's local user interface display
(if available).
WARNING! Only disable this if you
are absolutely sure that you do not
need to administer the managed
device or the Unity card through a
remote web browser session.
Communication Protocols
Enable/disable BACnet, Modbus, SNMP, and
YDN23 protocols - disable any that are unused.
Enable Communication Protocols
BACnet Settings
Set Managed Device Write Access to Read-
Only to prevent changes to the device through
the BACnet interface.
Modbus Settings
Set Managed Device Write Access to Read-
Only to prevent changes to the device through
the Modbus interface; Select the appropriate
option for Limit Network Access Type to
restrict which systems may request Modbus
data from the device - access may be open to
any system, limited to those on the same
subnet as the device, or limited to only those
from systems on a Trusted IP Address List.
SNMP Version Settings
Enable/disable the desired SNMP version(s);
Consider using SNMPv3 with user
authentication and encryption.
SNMP Access Table Settings
For each SNMPv1/v2c Access table entry, set
the SNMP Access Type to Read-Only to
prevent changes to the device from the hosts
identified in the table entry.
Configure SNMPv1/v2c Access Settings
SNMP Community Strings
Change the SNMP v1/v2c Trap and Access
Community Strings from their default values.
Configure SNMPv1 Trap Settings
and
Configure SNMPv1/v2c Access Settings
SNMPv3 Settings
Use the SNMPv3 Authentication and Privacy
settings to make SNMPv3 communications
more secure.
Configure SNMPv3 User Settings
YDN23 Settings
Set Managed Device Write Access to Read-
Only to prevent changes to the device through
the YDN23 interface.
Velocity Protocol Settings
Enable/disable the Velocity Protocol which is
used by Vertiv™ management applications to
access device data.
Table 2.1 Settings to review and verify to reduce the risk of unauthorized access (continued)
2 Installation
9














































