8-6
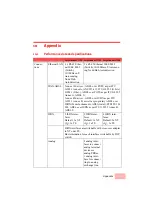
The security checklist
Is your saved SwyxConnect configuration stored in a safe
place?
Protect the saved configurations against unauthorized access in a
safe place. A saved configuration could otherwise be loaded in
another device by an unauthorized person, enabling, for
example, the use of your Internet connections at your expense
.
Have you activated the mechanism that protects your WAN
lines if the device is stolen?
After being stolen, the device can theoretically be operated at
another location by unauthorized persons. Password-protected
device configurations offer no protection from the operation of
the RAS access, LAN coupling or VPN connections that are set
up in the device; a thief could gain access to a protected net-
work.
The device's operation can be protected by various means; for
example, it will cease to function if there is an interruption to the
power supply, or if the device is switched on in another location.
With the ISDN site verification, the device can only be operated
at one particular ISDN connection. After being switched on, the
device calls itself at the corresponding telephone number to
check that it is still connected to the "proper" ISDN connection.
The scripting function can store the entire configuration in RAM
only so that restarting the device will cause the configuration to
be deleted. The configuration is not written to the non-volatile
flash memory. A loss of power because the device has been relo-
cated will cause the entire configuration to be deleted. Further
information can be found in the reference manual.
Содержание SwyxConnect 1722
Страница 112: ...I 5 ...