SonicWALL SSL-VPN 4000 Getting Started Guide Page 19
Scenario A: Configuring a DMZ or OPT Port in SonicOS Standard
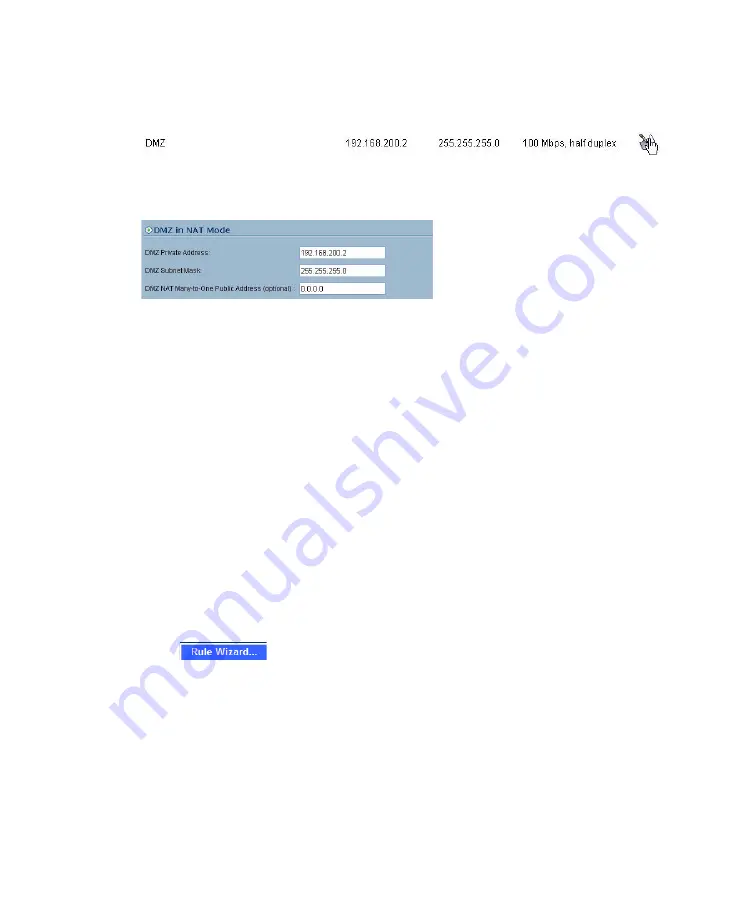
1. Select the
Network > Settings
page.
2. Click Configure button for the DMZ or OPT interface.
Select the
DMZ in NAT Mode
radio button.
3. Enter
192.168.200.2
in the DMZ Private Address field.
4. Enter
255.255.255.0
in the DMZ Subnet Mask field.
5. Click the
OK
button.
Scenario A: Allowing WAN -> DMZ Connection in SonicOS Standard
Follow this procedure if you are connecting the SonicWALL SSL-VPN 4000 to a
SonicWALL UTM appliance running
SonicOS Standard
. If your SonicWALL UTM
appliance is running
SonicOS Enhanced
, skip to “Scenario A: Allowing WAN -> SSL-
VPN Connection in SonicOS Enhanced” on page 26
9
Tip:
Leave the default rule to deny any access from WAN to DMZ in place, and use the
Public Server Rule Wizard to create an access rule to allow HTTP and HTTPS
specifically to the SonicWALL SSL-VPN appliance. As you add different servers to the
DMZ, you can use the wizard to create access to the new servers while still restricting all
other traffic.
Note:
If you are allowing HTTP access to your SonicWALL SSL-VPN appliance as well
as HTTPS access, you need to run the wizard twice to create public server access rules
for both HTTP and HTTPS.
Create a public server access rule for HTTPS traffic:
1. Select the
Firewall > Access Rules
page.
2. Click .
3. In the
Welcome to the SonicWALL Network Access Rules Wizard
page,
click
Next
.
Содержание SSL-VPN 4000
Страница 60: ...SonicWALL SSL VPN 4000 Getting Started Guide Page 59 Notes...
Страница 61: ...Page 60 Notes...
















































