SIEMENS 5881 Broadband Internet Router
User’s Guide
Chapter 4 User Setup
User Management
SIEMENS
22
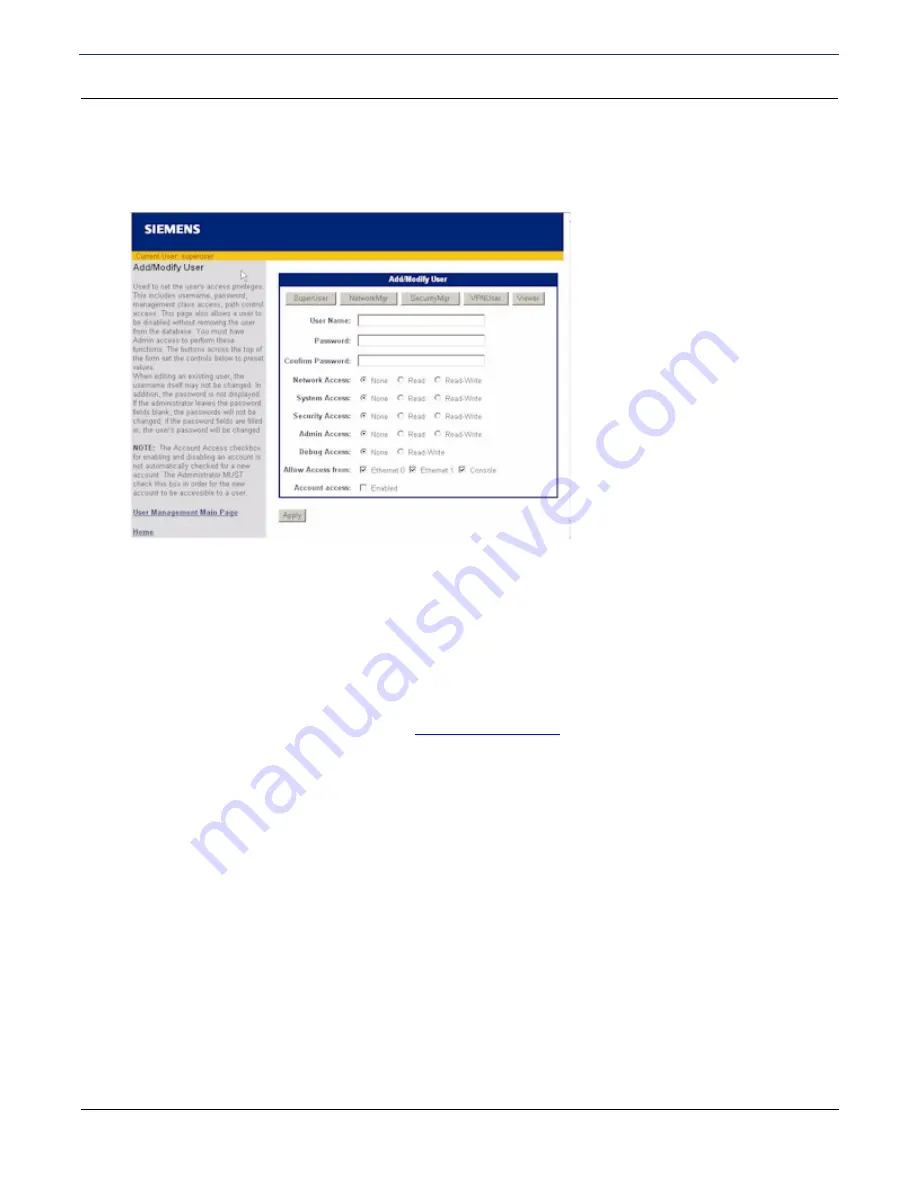
Adding/Modifying A User Account
User accounts are used to control access to the router and the Internet. To add a user account:
1. Click
New User
on the User Management page. This displays the Add/Modify User page.
(To modify a user, select the desired name in the
Select User
list and click
Edit User
to display the Add/
Modify User page. Note that changing the password or privileges of an existing user account may
terminate a user’s current activity or connection.)
2. Enter
User Name
,
Password
, and
Confirm Password
in the appropriate boxes. (The User Name cannot
be modified for an existing account. When editing an existing account, the Password and Confirm
Password values are not displayed. If you leave them blank, the password is not changed.)
3. Do one of the following to assign privileges to this user account:
•
Select one of the buttons at the top of this page to automatically assign pre-set privileges to the user
based on common user roles. (Refer to
Management Classes
for details on the privileges automatically
assigned to each role.)
•
Manually select the management activity you want to assign to this user account. For each management
activity class, click to select
Read
,
Read-Write
privileges for the user, or select
None
for no privilege.
4. In
Allow Access From
, specify one or more of the following:
•
Ethernet 0
: Can access from the LAN side.
•
Ethernet 1
: Can access from the WAN side.
•
Console
: Can access from a console.
User access verification is performed if the user account is verified during user authentication. User access
verifies that the user account can access the router through the connectivity method being used, such as
over the LAN or through a console.
5. Click
Enabled
for
Account Access
to enable this account. By default, accounts are disabled when added.
This must be manually selected before the account is accessible to the user.
6. Click
Apply
to add/modify the user account.
















































