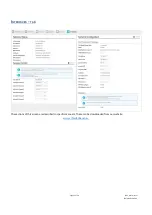
Configure SSL certificates
For increased security the communication can be encrypted using SSL certificates.
Key Generation
Certificates with a public and private key can be uploaded with the web interface. The certificates are used for the
authentication phase of the handshake. These certificates can be generated in 3 steps:
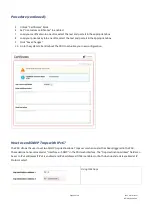
1. Generate a private key
2. Generate a CSR (Certificate Signing Request) with the private key.
3. Create a self-signed certificate with the CSR.
The following private keys will be supported:
1. RSA (1024 bit)
2. Elliptic Curve (secp256r1/ prime256v1 and secp384r1)
TLS Cipher Suites Supported:
The TLS cipher suites are listed in the following format (example):
TLS_DHE_RSA_WITH_AES_256_GCM_SHA384
1. TLS prefix
2. Key Exchange algorithm (DHE) (Excluded for static keys)
3. Authentication algorithm (RSA)
4. Encryption algorithm (AES)
5. Encryption strength (256)
6. Encryption mode (GCM)
7. MAC (SHA284)
The certificate uploaded is used for the "Authentication algorithm" (RSA or Elliptic Curve). Other options (Key Exchange,
Encryption etc) are selected from what the client lists as supported in the "Client Hello". The following cipher suites are
supported:
Static Key with RSA:
●
MBEDTLS_TLS_RSA_WITH_AES_128_GCM_SHA256
●
MBEDTLS_TLS_RSA_WITH_AES_128_CBC_SHA256
●
MBEDTLS_TLS_RSA_WITH_AES_256_CBC_SHA256
●
MBEDTLS_TLS_RSA_WITH_AES_128_CBC_SHA
●
MBEDTLS_TLS_RSA_WITH_AES_256_CBC_SHA
Page 47 of 58
V262_User manual
Schleifenbauer PDU
Содержание V2.62
Страница 1: ...V2 62 Schleifenbauer PDU User manual...