Selecting Simple (Limitation)
If you select [Simple (Limitation)], you can specify clients for which printer job authentication is not required.
Specify [Parallel Interface (Sim.)], [USB (Sim.)] and the clients' IPv4 address range in which printer job
authentication is not required. Specify this setting if you want to print using unauthenticated printer drivers
or without any printer driver. Authentication is required for printing with non-specified devices.
If you select [Simple (Limitation)], you can print even with unauthenticated printer drivers or devices. Specify
this setting if you want to print with a printer driver or device that cannot be identified by the machine or if
you do not require authentication for printing. However, note that, because the machine does not require
authentication in this case, it may be used by unauthorized users.
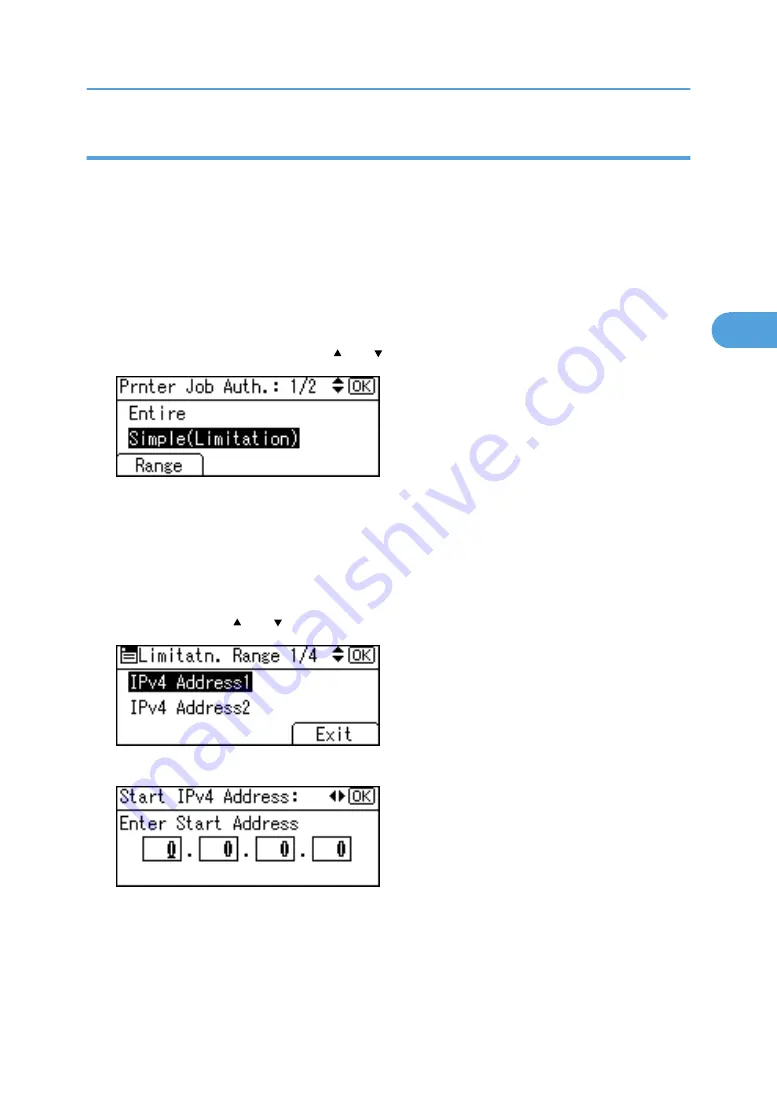
1.
Select [Simple (Limitation)] using [ ] or [ ], and then press the [Range] key.
Specify the range in which [Simple (Limitation)] is applied to Printer Job Authentication.
If you specify IPv4 address range, proceed to step 2.
If you specify [Parallel Interface (Sim.)], proceed to step 5.
If you specify [USB (Sim.)], proceed to step 7.
2.
Select [IPv4 Address 1], [IPv4 Address 2], [IPv4 Address 3], [IPv4 Address 4] or [IPv4
Address 5] using [ ] or [ ], and then press the [OK] key.
3.
Enter the Start IPv4 Address, and then press the [OK] key.
You can specify the IPv4 address range to which this setting is applied.
User Code Authentication
43
3
Содержание Aficio MP C2030
Страница 2: ......
Страница 10: ...INDEX 245 8 ...
Страница 47: ...9 Press Exit 10 Press the OK key 11 Press the User Tools Counter key User Code Authentication 45 3 ...
Страница 118: ...6 Press the User Tools Counter key 5 Managing Access to the Machine 116 5 ...
Страница 128: ...5 Managing Access to the Machine 126 5 ...
Страница 153: ... p 26 Registering the Administrator Protection Using Encryption 151 6 ...
Страница 194: ...8 Troubleshooting 192 8 ...
Страница 249: ...MEMO 247 ...
Страница 250: ...MEMO 248 GB GB EN USA AE AE D040 ...
Страница 251: ...Copyright 2008 ...






























