10.
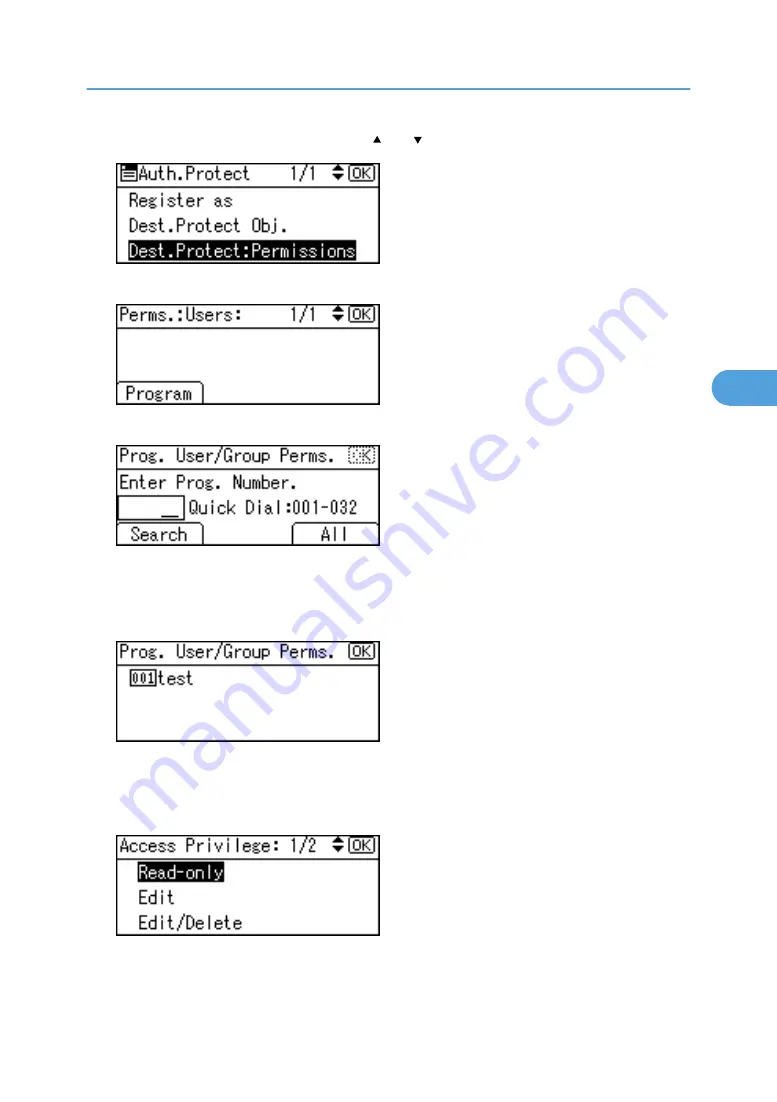
Select [Dest.Protect: Permissions] using [ ] or [ ], and then press the [OK] key.
11.
Press [Program].
12.
Select the users or groups to register.
You can select more than one user.
By pressing [All], you can select all the users.
13.
Press the [OK] key.
14.
Select the permission, and then press the [OK] key.
Select the permission, from [Read-only], [Edit], [Edit/Delete], or [Full Control].
To register multiple users, repeat steps 12 to 14.
15.
Press the [User Tools/Counter] key.
Protecting the Address Book
107
4
Содержание Aficio MP C2030
Страница 2: ......
Страница 10: ...INDEX 245 8 ...
Страница 47: ...9 Press Exit 10 Press the OK key 11 Press the User Tools Counter key User Code Authentication 45 3 ...
Страница 118: ...6 Press the User Tools Counter key 5 Managing Access to the Machine 116 5 ...
Страница 128: ...5 Managing Access to the Machine 126 5 ...
Страница 153: ... p 26 Registering the Administrator Protection Using Encryption 151 6 ...
Страница 194: ...8 Troubleshooting 192 8 ...
Страница 249: ...MEMO 247 ...
Страница 250: ...MEMO 248 GB GB EN USA AE AE D040 ...
Страница 251: ...Copyright 2008 ...






























