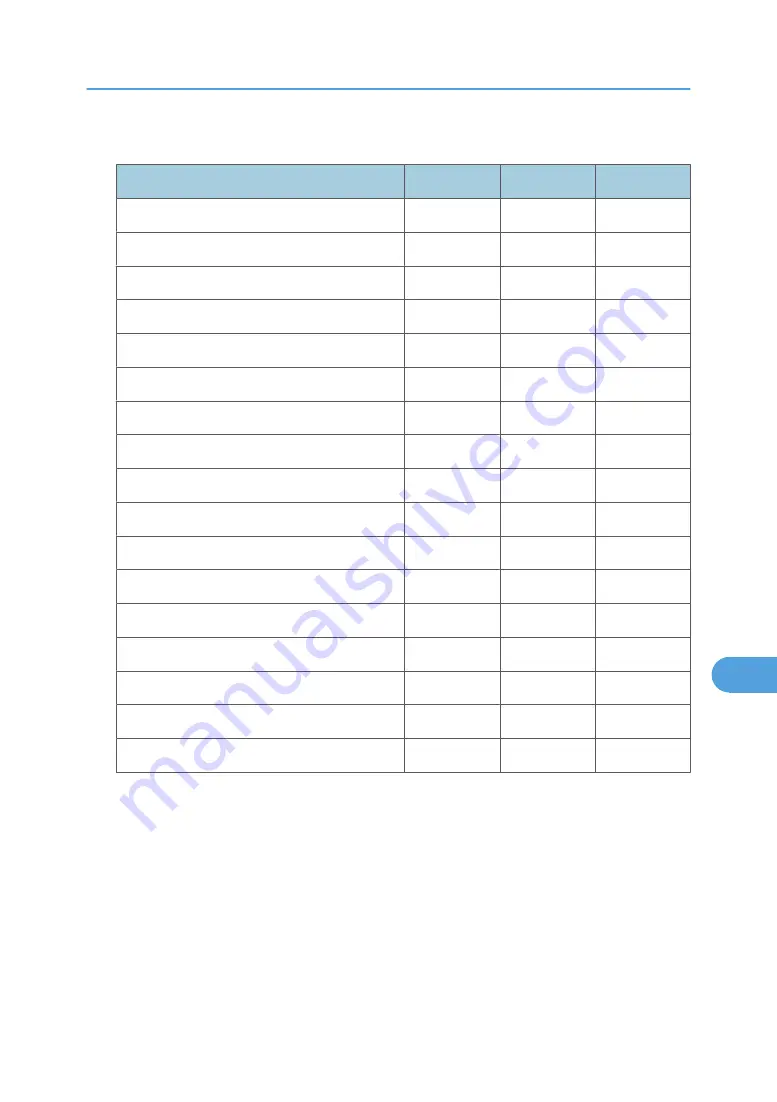
Administrator Tools
Settings
A
B
C
Address Book Management
R/W
R/W
N/A
Prgrm. /Change/Delete Group
R/W
R/W
N/A
Address Book:Print List
R/W
R/W
N/A
Display / Print Counter
R/W
R/W
N/A
Disp./Print User Counter
R/W
N/A
N/A
User Auth. Management
R/W
R
N/A
Admin.Auth.Management
R/W
N/A
N/A
Key Counter Management
R/W
R
N/A
Extended Security
R/W
R
N/A
Prog/Chnge/Del LDAP Server *6
R/W
R
N/A
LDAP Search
R/W
R
N/A
Prog./Change/Delete Realm
R/W
R
N/A
AOF(Always On)
R/W
R
N/A
Energy Saver Level
R/W
R
N/A
Service Mode Lock
R/W
R
N/A
Delete All Logs
R/W
R
N/A
Transfer log Setting
R/W
N/A
N/A
*6 Only the password can be specified.
System Settings
225
9
Содержание Aficio MP C2030
Страница 2: ......
Страница 10: ...INDEX 245 8 ...
Страница 47: ...9 Press Exit 10 Press the OK key 11 Press the User Tools Counter key User Code Authentication 45 3 ...
Страница 118: ...6 Press the User Tools Counter key 5 Managing Access to the Machine 116 5 ...
Страница 128: ...5 Managing Access to the Machine 126 5 ...
Страница 153: ... p 26 Registering the Administrator Protection Using Encryption 151 6 ...
Страница 194: ...8 Troubleshooting 192 8 ...
Страница 249: ...MEMO 247 ...
Страница 250: ...MEMO 248 GB GB EN USA AE AE D040 ...
Страница 251: ...Copyright 2008 ...






























