Chapter 2. Installing Red Hat Enterprise Linux
29
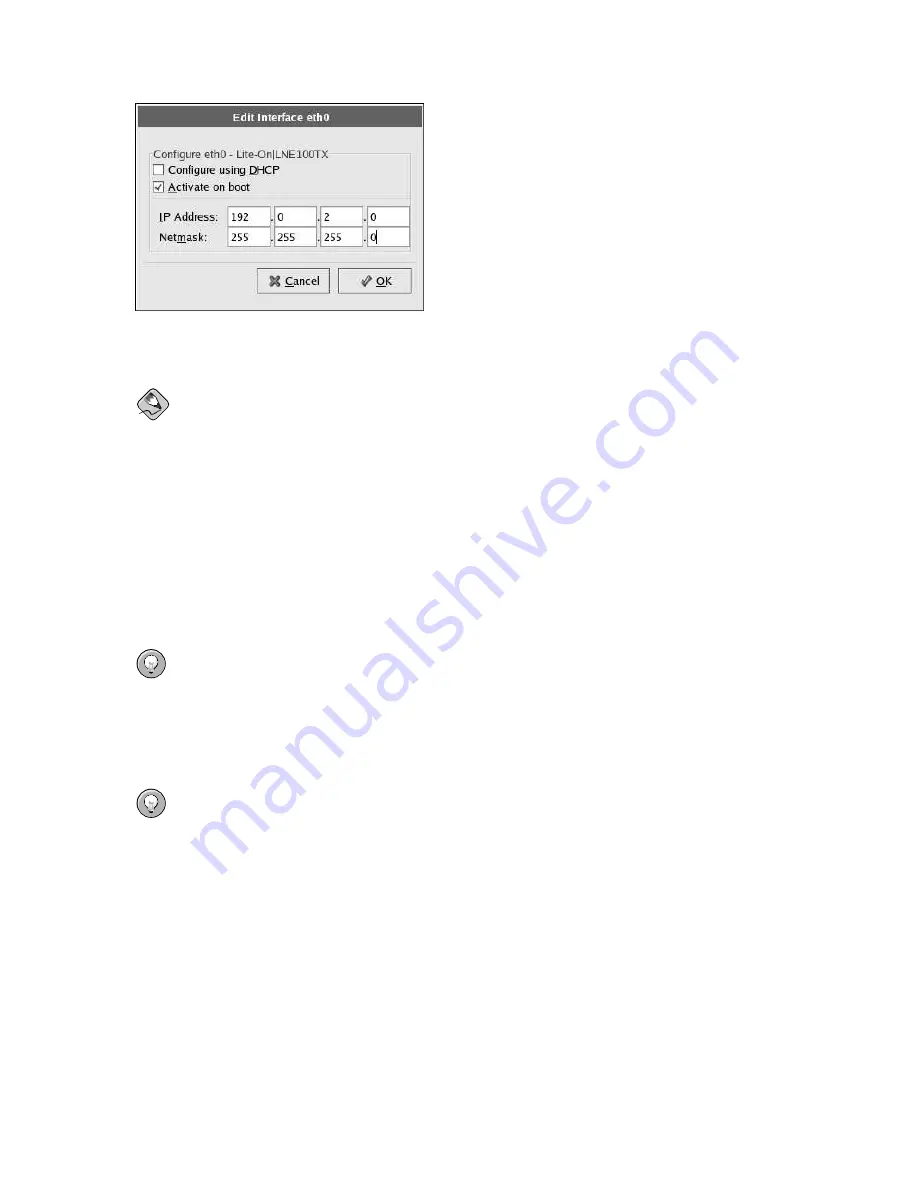
Figure 2-17. Editing a Network Device
Note
Do not use the numbers as seen in this sample configuration. These values will not work for your own
network configuration. If you are not sure what values to enter, contact your network administrator for
assistance.
If you have a hostname (fully qualified domain name) for the network device, you can choose to have
DHCP (Dynamic Host Configuration Protocol) automatically detect it or you can manually enter the
hostname in the field provided.
Finally, if you entered the IP and Netmask information manually, you may also enter the Gateway
address and the Primary, Secondary, and Tertiary DNS addresses.
Tip
Even if your computer is not part of a network, you can enter a hostname for your system. If you do
not take this opportunity to enter a name, your system will be known as
localhost
.
Tip
To change your network configuration after you have completed the installation, use the
Network
Administration Tool
.
Type the
redhat-config-network
command in a shell prompt to launch the
Network Administra-
tion Tool
. If you are not root, it prompts you for the root password to continue.
2.17. Firewall Configuration
Red Hat Enterprise Linux offers firewall protection for enhanced system security. A firewall exists
between your computer and the network, and determines which resources on your computer remote
users on the network can access. A properly configured firewall can greatly increase the security of
your system.
Содержание ENTERPRISE LINUX 3 - FOR IBM ESERVER ISERIES AND IBM ESERVER PSERIES
Страница 14: ...6 Chapter 1 Steps to Get You Started ...
Страница 52: ...44 Chapter 2 Installing Red Hat Enterprise Linux ...
Страница 54: ...46 Appendix A Red Hat Linux to Red Hat Enterprise Linux Migration Solution ...
Страница 74: ...66 Appendix E Additional Boot Options ...
Страница 78: ......
Страница 80: ...72 ...
















































