C
HAPTER
3:
CONFIGURING INTRUSION DETECTION
47
4.
Choose the appliance that you wish to configure by clicking
Configure
next to it.
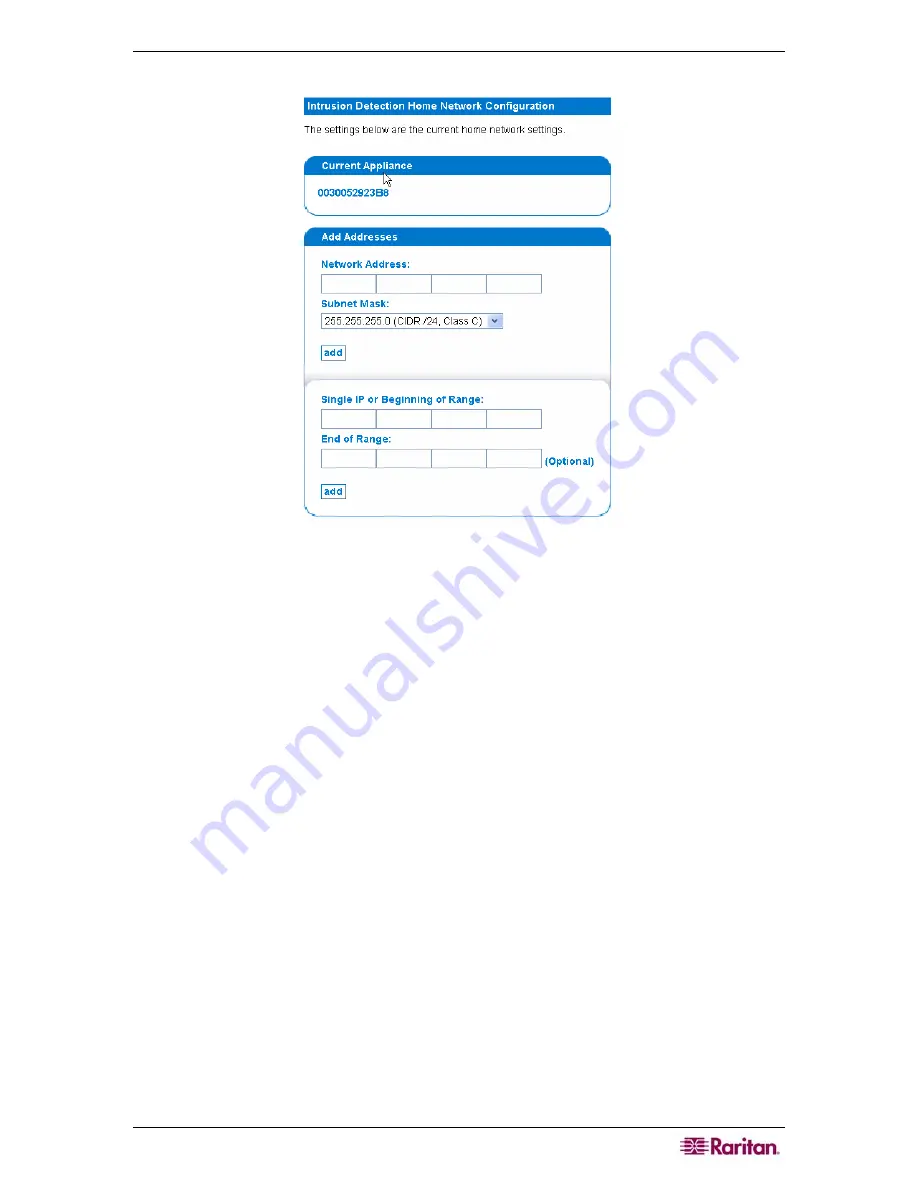
Figure 60 Configuring Home Network for Intrusion Detection Appliance
5.
To include an entire subnet in your home network, use the
Add Addresses
box. Type in the
network address and select the subnet mask from the list that is provided.
6.
To include single hosts or ranges of host IP addresses, use the input boxes in the bottom half
of the panel. Please note that you can only add a maximum of 50 "stray" IP addresses that are
not a part of a subnet. This includes individual addresses and all addresses within your ranges
.
7.
Click
finish configuration.
Configure Port Scan Detection
Intrusion Detection appliances can perform stateful inspection of packets to detect port scanning
activity, that is, the probing for openings and availabilities in a network on your network.
However, some legitimate services that open multiple connections to hosts, like DNS, NFS, and
SMB, may produce false-positive port scan events. Use this page to exclude servers that generate
false-positive port scan events from port scan detection.
1.
Click on the
Admin
tab in the top navigation bar.
2.
Click
Intrusion Detection Configuration
.
3.
Click
Configure Portscan Detection
.
Содержание COMMANDCENTER NOC
Страница 2: ...This page intentionally left blank...
Страница 12: ...xii FIGURES...
Страница 20: ...8 COMMANDCENTER NOC ADMINISTRATOR GUIDE...
Страница 114: ...102 COMMANDCENTER NOC ADMINISTRATOR GUIDE...
Страница 132: ...120 COMMANDCENTER NOC ADMINISTRATOR GUIDE...
Страница 144: ...132 COMMANDCENTER NOC ADMINISTRATOR GUIDE...
Страница 148: ...136 COMMANDCENTER NOC ADMINISTRATOR GUIDE...
Страница 155: ...APPENDIX G NETWORK TRAFFIC OVERHEAD NETWORK MANAGEMENT S NECESSARY EVIL 143 255 80 5301 00...






























