Wireless Notebook Adapter
21
To use WEP encryption, select 64-bit or 128-bit WEP from the drop-down
menu (recommended).
If you select 64-bit or 128-bit WEP, you have two choices. Enter the
passphrase of your wireless network in the Passphrase field, or enter the
WEP key of your wireless network in the Key 1 field. Click the Next but-
ton to continue or the Back button to return to the previous screen.
Passphrase - This passphrase must match the passphrase of your wireless
network. This is the code used when logging a wireless device onto the
wireless network. The passphrase is case-sensitive and should not be longer
than 16 alphanumeric characters. Based upon the passphrase created by
you, WEP key settings are automatically generated. This passphrase is
compatible only with other Linksys wireless products.
Key 1 - This WEP key must match the WEP key of your wireless network.
If you are using 64-bit WEP encryption, then the key must consist of exact-
ly 10 hexadecimal characters in length. If you are using 128-bit WEP
encryption, then the key must consist of exactly 26 hexadecimal characters
in length. Valid hexadecimal characters are “0” to “9” and “A” to “F”.
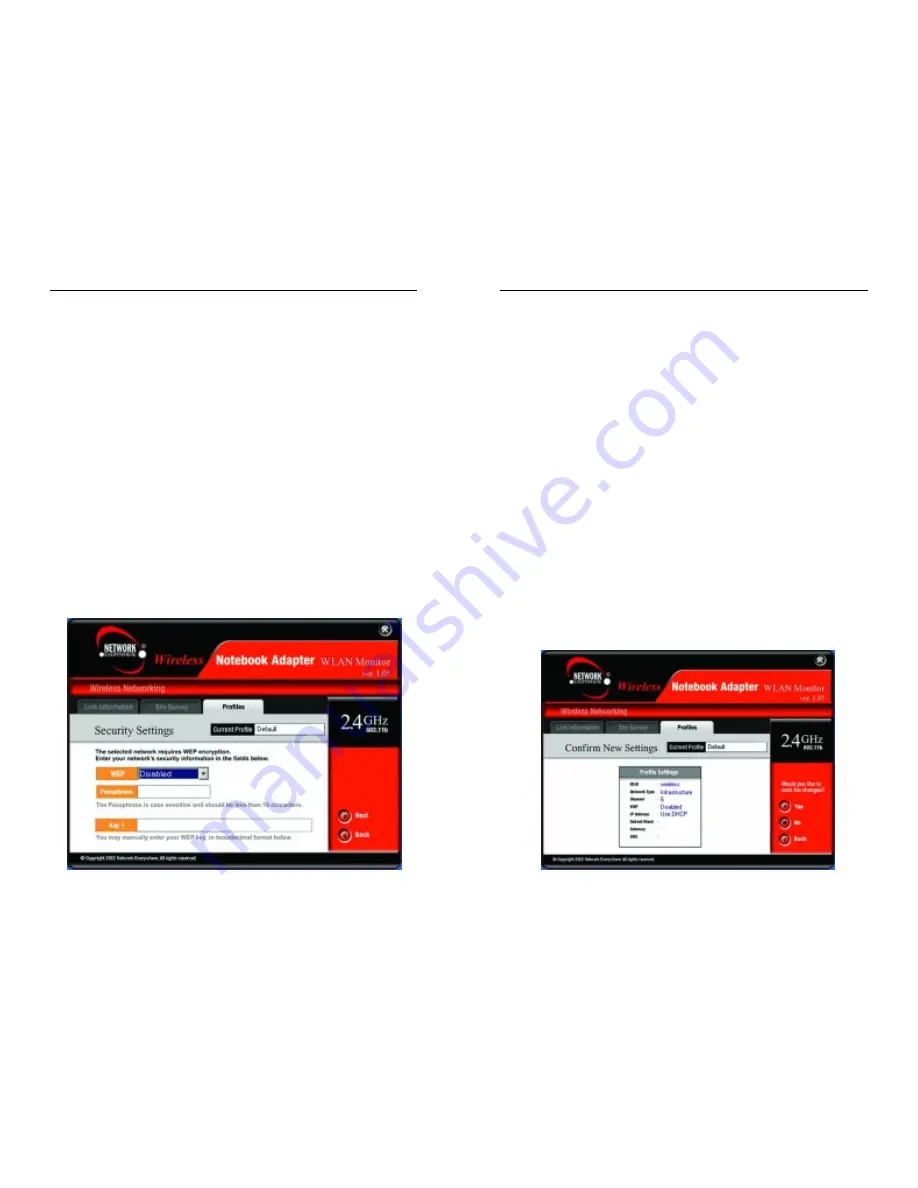
6. The Confirm New Settings screen, shown in Figure 5-14, will appear next.
To save the new settings, click the Yes button. To cancel the settings and
return to the Profiles screen, click the No button. To edit the new settings,
click the Back button.
Figure 5-14
20
Network Everywhere
™
Series
Subnet Mask - The Adapter’s Subnet Mask must be the same as your wired
network’s Subnet Mask. Enter the Subnet Mask in this format:
xxx.xxx.xxx.xxx (the x’s represent your actual Subnet Mask).
Default Gateway - Enter the IP address of your network’s Gateway here.
Enter the Default Gateway in this format: xxx.xxx.xxx.xxx (the x’s repre-
sent your actual Default Gateway).
DNS - Enter the DNS address of your Ethernet (wired) network here. Enter
the DNS address in this format: xxx.xxx.xxx.xxx (the x’s represent your
actual DNS address).
Click the Next button to continue or the Back button to return to the previ-
ous screen.
5. The Security Settings screen, shown in Figure 5-13, will appear next. Set
the Wired Equivalent Privacy (WEP) encryption for your wireless network
by selecting a WEP configuration method.
WEP (Disabled/64-bit WEP/128-bit WEP) - If you do not want to use
WEP encryption, choose Disabled. Then click the Next button to continue
or the Back button to return to the previous screen.
Figure 5-13
Содержание NWP11B
Страница 1: ......
Страница 22: ...Copyright 2002 Network Everywhere All rights reserved http www NetworkEverywhere com...






















