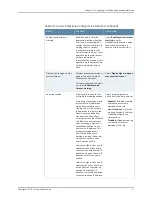
Table 7: User Role Configuration Details
(continued)
Your Action
Function
Option
Select
General
>
Terminal
Services
to enable this access
feature.
Enables terminal emulation
sessions on a Windows
terminal server, Citrix NFuse
server, or Citrix Metaframe
server.
Terminal Services
Select
General
>
Meeting
to
enable this access feature.
Allows users to securely
schedule and hold online
meetings between both
Secure Access devices and
non-Secure Access devices.
Meeting
Select
General
>
to
enable this access feature.
Enables users to use
standards-based e-mail
clients to access corporate
e-mail securely from remote
locations without the need for
any additional software, such
as a VPN client.
Select
General
>
Network
Connect
to enable this access
feature.
The Network Connect option
provides secure, SSL-based
network-level remote access
to all enterprise application
resources using the Secure
Access device over port 443.
Network Connect
Table 8: Global User Role Configuration Details
Your Action
Function
Option
Global Role Options > Global Terminal Services Role Options tab
Select the
plus
button to
specify the name, color,
comment and file name for
the object.
Allows you to specify a shared binary
data object.
Citrix Client CAB File
Enter the name.
Specifies the name of the object.
NOTE: The name, color, comment, file
name fields are displayed only when you
click the
plus
button in the right side of
the
Citrix Client CAB File
list.
Name
Select a color from
Color
drop
down list.
Specifies the color of the object.
Color
Enter the comment.
Allows you to specify a comment.
Comment`
Click
Browse
and select the
file.
Allows you to upload the shared binary
data object.
File Name
37
Copyright © 2010, Juniper Networks, Inc.
Chapter 6: Configuring User Roles and Administrator Roles
Содержание NETWORK AND SECURITY MANAGER
Страница 6: ...Copyright 2010 Juniper Networks Inc vi...
Страница 12: ...Copyright 2010 Juniper Networks Inc xii Configuring Secure Access Devices Guide...
Страница 18: ...Copyright 2010 Juniper Networks Inc xviii Configuring Secure Access Devices Guide...
Страница 20: ...Copyright 2010 Juniper Networks Inc 2 Configuring Secure Access Devices Guide...
Страница 28: ...Copyright 2010 Juniper Networks Inc 10 Configuring Secure Access Devices Guide...
Страница 40: ...Copyright 2010 Juniper Networks Inc 22 Configuring Secure Access Devices Guide...
Страница 46: ...Copyright 2010 Juniper Networks Inc 28 Configuring Secure Access Devices Guide...
Страница 50: ...Copyright 2010 Juniper Networks Inc 32 Configuring Secure Access Devices Guide...
Страница 52: ...Copyright 2010 Juniper Networks Inc 34 Configuring Secure Access Devices Guide...
Страница 82: ...Copyright 2010 Juniper Networks Inc 64 Configuring Secure Access Devices Guide...
Страница 110: ...Copyright 2010 Juniper Networks Inc 92 Configuring Secure Access Devices Guide...
Страница 154: ...Copyright 2010 Juniper Networks Inc 136 Configuring Secure Access Devices Guide...
Страница 224: ...Copyright 2010 Juniper Networks Inc 206 Configuring Secure Access Devices Guide...
Страница 234: ...Copyright 2010 Juniper Networks Inc 216 Configuring Secure Access Devices Guide...
Страница 288: ...Copyright 2010 Juniper Networks Inc 270 Configuring Secure Access Devices Guide...
Страница 300: ...Copyright 2010 Juniper Networks Inc 282 Configuring Secure Access Devices Guide...
Страница 310: ...Copyright 2010 Juniper Networks Inc 292 Configuring Secure Access Devices Guide...
Страница 312: ...Copyright 2010 Juniper Networks Inc 294 Configuring Secure Access Devices Guide...
Страница 320: ...Copyright 2010 Juniper Networks Inc 302 Configuring Secure Access Devices Guide...
Страница 322: ...Copyright 2010 Juniper Networks Inc 304 Configuring Secure Access Devices Guide...
Страница 337: ...PART 6 Index Index on page 321 319 Copyright 2010 Juniper Networks Inc...
Страница 338: ...Copyright 2010 Juniper Networks Inc 320 Configuring Secure Access Devices Guide...
Страница 340: ...Copyright 2010 Juniper Networks Inc 322 Configuring Secure Access Devices Guide...