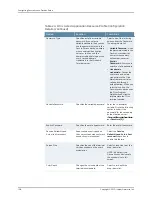
Table 23: Citrix Terminal Services (Default ICA) Configuration
Details
(continued)
Your Action
Function
Option
Select the role, and then click
Add
.
Specifies the roles to which the
resource profile applies.
NOTE: The Role Selections tab
is enabled only when you select
the
Subset of Terminal Service
Profile roles
check box from the
Applies to roles drop–down list.
Roles Selections
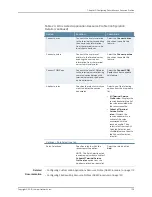
Related
Documentation
Configuring a Citrix Listed Application Resource Profile (NSM Procedure) on page 104
•
•
Configuring Custom Web Applications Resource Profile (NSM Procedure) on page 112
•
Configuring a Citrix Terminal Services (Custom ICA) Resource Profile (NSM Procedure)
on page 95
Configuring a Citrix Listed Application Resource Profile (NSM Procedure)
Citrix created
published applications
to satisfy the need for security. It is dangerous to
allow any executable to be run on the server. With published applications, only
applications that are allowed to be run are published.
With the Secure Access device, these published applications are displayed on the Secure
Access device index page as terminal services bookmarks.
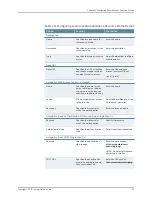
To configure a Citrix listed application resource profile:
1.
In the NSM navigation tree, select
Device Manager
>
Devices
. Click the
Device Tree
tab, and then double-click the Secure Access device for which you want to configure
a Citrix listed application resource profile.
2.
Click the
Configuration
tab, and select
Users
>
Resource Profiles
>
Terminal Services
.
The corresponding workspace appears.
3.
Click the
New
button and the New dialog box appears.
4.
Add or modify settings as specified in Table 24 on page 104.
5.
Click one:
•
OK
—Saves the changes.
•
Cancel
—Cancels the modifications.
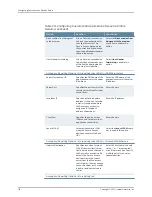
Table 24: Citrix Listed Application Resource Profile Configuration Details
Your Action
Function
Option
Settings tab
Enter the name.
Specifies a unique name for the
resource profile.
Name
Copyright © 2010, Juniper Networks, Inc.
104
Configuring Secure Access Devices Guide
Содержание NETWORK AND SECURITY MANAGER
Страница 6: ...Copyright 2010 Juniper Networks Inc vi...
Страница 12: ...Copyright 2010 Juniper Networks Inc xii Configuring Secure Access Devices Guide...
Страница 18: ...Copyright 2010 Juniper Networks Inc xviii Configuring Secure Access Devices Guide...
Страница 20: ...Copyright 2010 Juniper Networks Inc 2 Configuring Secure Access Devices Guide...
Страница 28: ...Copyright 2010 Juniper Networks Inc 10 Configuring Secure Access Devices Guide...
Страница 40: ...Copyright 2010 Juniper Networks Inc 22 Configuring Secure Access Devices Guide...
Страница 46: ...Copyright 2010 Juniper Networks Inc 28 Configuring Secure Access Devices Guide...
Страница 50: ...Copyright 2010 Juniper Networks Inc 32 Configuring Secure Access Devices Guide...
Страница 52: ...Copyright 2010 Juniper Networks Inc 34 Configuring Secure Access Devices Guide...
Страница 82: ...Copyright 2010 Juniper Networks Inc 64 Configuring Secure Access Devices Guide...
Страница 110: ...Copyright 2010 Juniper Networks Inc 92 Configuring Secure Access Devices Guide...
Страница 154: ...Copyright 2010 Juniper Networks Inc 136 Configuring Secure Access Devices Guide...
Страница 224: ...Copyright 2010 Juniper Networks Inc 206 Configuring Secure Access Devices Guide...
Страница 234: ...Copyright 2010 Juniper Networks Inc 216 Configuring Secure Access Devices Guide...
Страница 288: ...Copyright 2010 Juniper Networks Inc 270 Configuring Secure Access Devices Guide...
Страница 300: ...Copyright 2010 Juniper Networks Inc 282 Configuring Secure Access Devices Guide...
Страница 310: ...Copyright 2010 Juniper Networks Inc 292 Configuring Secure Access Devices Guide...
Страница 312: ...Copyright 2010 Juniper Networks Inc 294 Configuring Secure Access Devices Guide...
Страница 320: ...Copyright 2010 Juniper Networks Inc 302 Configuring Secure Access Devices Guide...
Страница 322: ...Copyright 2010 Juniper Networks Inc 304 Configuring Secure Access Devices Guide...
Страница 337: ...PART 6 Index Index on page 321 319 Copyright 2010 Juniper Networks Inc...
Страница 338: ...Copyright 2010 Juniper Networks Inc 320 Configuring Secure Access Devices Guide...
Страница 340: ...Copyright 2010 Juniper Networks Inc 322 Configuring Secure Access Devices Guide...