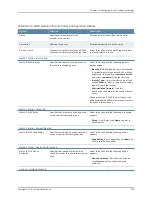
Table 85: IF–MAP Session-Import Policy Configuration Details
(continued)
Your Action
Function
Option
Select Secure Access devices roles from the
Non-members area and move it to the Members
area.
Assigns roles from the available list.
Use these roles
Actions > Copy IF-MAP Roles tab
Select
Copy IF-MAP roles
and select
All roles
,
Specified roles
, or
All roles other than those
specified below
, and then list the IF-MAP roles.
Copies the specified roles.
Copy IF-MAP Roles
Actions > Copy IF-MAP Capabilities tab
Select
Copy IF-MAP capabilities
and select
All
capabilities
,
Specified capabilities
or
All
capabilities other than those specified below
,
and then list the IF-MAP capabilities.
Copies the IF-MAP capabilities.
Copy IF-MAP Capabilities
Related
Documentation
Configuring IF-MAP Session Export Policy on the Secure Access Device (NSM Procedure)
on page 285
•
•
Configuring IF-MAP Server Replicas (NSM Procedure) on page 290
Configuring IF-MAP Server Replicas (NSM Procedure)
You can configure an IF-MAP server to replicate all of its IF-MAP data to other IF-MAP
servers. For example, if you have a network in Boston and a network in London, you can
run IF-MAP servers in both places and configure the IF-MAP servers in both locations to
replicate data to one another. These connected IF-MAP servers are known as replicas.
To configure IF-MAP server replicas to communicate with each other:
1.
In the NSM navigation tree, select
Device Manager
>
Devices
. Click the
Device Tree
tab, and then double-click the Secure Access device for which you want to configure
IF-MAP server replicas.
2.
Click the
Configuration
tab. In the configuration tree, select
System > IF–MAP
Federation > This Server
.
3.
Add or modify settings as specified in Table 86 on page 290.
4.
Click one:
•
OK
—Saves the changes.
•
Cancel
—Cancels the modifications.
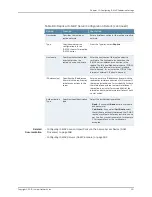
Table 86: Replica IF–MAP Server Configuration Details
Your Action
Function
Option
Enter a name for the replica IF-MAP server.
Specifies a unique name for
the replica IF-MAP server.
Name
Copyright © 2010, Juniper Networks, Inc.
290
Configuring Secure Access Devices Guide
Содержание NETWORK AND SECURITY MANAGER
Страница 6: ...Copyright 2010 Juniper Networks Inc vi...
Страница 12: ...Copyright 2010 Juniper Networks Inc xii Configuring Secure Access Devices Guide...
Страница 18: ...Copyright 2010 Juniper Networks Inc xviii Configuring Secure Access Devices Guide...
Страница 20: ...Copyright 2010 Juniper Networks Inc 2 Configuring Secure Access Devices Guide...
Страница 28: ...Copyright 2010 Juniper Networks Inc 10 Configuring Secure Access Devices Guide...
Страница 40: ...Copyright 2010 Juniper Networks Inc 22 Configuring Secure Access Devices Guide...
Страница 46: ...Copyright 2010 Juniper Networks Inc 28 Configuring Secure Access Devices Guide...
Страница 50: ...Copyright 2010 Juniper Networks Inc 32 Configuring Secure Access Devices Guide...
Страница 52: ...Copyright 2010 Juniper Networks Inc 34 Configuring Secure Access Devices Guide...
Страница 82: ...Copyright 2010 Juniper Networks Inc 64 Configuring Secure Access Devices Guide...
Страница 110: ...Copyright 2010 Juniper Networks Inc 92 Configuring Secure Access Devices Guide...
Страница 154: ...Copyright 2010 Juniper Networks Inc 136 Configuring Secure Access Devices Guide...
Страница 224: ...Copyright 2010 Juniper Networks Inc 206 Configuring Secure Access Devices Guide...
Страница 234: ...Copyright 2010 Juniper Networks Inc 216 Configuring Secure Access Devices Guide...
Страница 288: ...Copyright 2010 Juniper Networks Inc 270 Configuring Secure Access Devices Guide...
Страница 300: ...Copyright 2010 Juniper Networks Inc 282 Configuring Secure Access Devices Guide...
Страница 310: ...Copyright 2010 Juniper Networks Inc 292 Configuring Secure Access Devices Guide...
Страница 312: ...Copyright 2010 Juniper Networks Inc 294 Configuring Secure Access Devices Guide...
Страница 320: ...Copyright 2010 Juniper Networks Inc 302 Configuring Secure Access Devices Guide...
Страница 322: ...Copyright 2010 Juniper Networks Inc 304 Configuring Secure Access Devices Guide...
Страница 337: ...PART 6 Index Index on page 321 319 Copyright 2010 Juniper Networks Inc...
Страница 338: ...Copyright 2010 Juniper Networks Inc 320 Configuring Secure Access Devices Guide...
Страница 340: ...Copyright 2010 Juniper Networks Inc 322 Configuring Secure Access Devices Guide...