CHAPTER 19
Synchronizing User Records
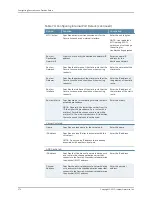
User record synchronization relies on client/server pairings. The client is the Secure Access
appliance that users log in to start their remote access. Each client is associated with
one primary server and one backup server to store user record data. Clients can be
individual appliances or a node within a cluster.
A server in this instance is the Secure Access appliance that stores the user record data.
Each server can be configured to replicate its user record data to one or more peer servers.
Servers are identified by a user-defined logical name. The same logical name can be
assigned to more than one authentication server to let you associate authentication
servers of different types to the same user. For example, SA1 is an ACE authentication
server with user1 who creates a bookmark to
www.juniper.net
. SA2 is an Active Directory
authentication server with the same user1. For the
www.juniper.net
bookmark to be
transferred from SA1/ACE/user1 to SA2/AD/user1 you would assign the logical name
“Logical1” to both the ACE server on SA1 and the Active Directory server on SA2.
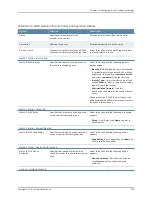
As long as the logical name is the same, the authentication servers can be different types
and can have different server names and still be associated with a common user. The
username must be the same for user record data to be synchronized across the servers.
The logical authentication server (LAS) and username combination is what uniquely
identifies a user record.
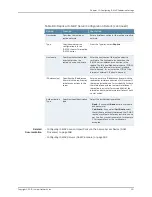
The following user records are synchronized between the client and server:
•
Bookmarks
•
Web
•
File
•
Terminal Services
•
JSAM
•
Preferences
•
Persistent cookies
277
Copyright © 2010, Juniper Networks, Inc.
Содержание NETWORK AND SECURITY MANAGER
Страница 6: ...Copyright 2010 Juniper Networks Inc vi...
Страница 12: ...Copyright 2010 Juniper Networks Inc xii Configuring Secure Access Devices Guide...
Страница 18: ...Copyright 2010 Juniper Networks Inc xviii Configuring Secure Access Devices Guide...
Страница 20: ...Copyright 2010 Juniper Networks Inc 2 Configuring Secure Access Devices Guide...
Страница 28: ...Copyright 2010 Juniper Networks Inc 10 Configuring Secure Access Devices Guide...
Страница 40: ...Copyright 2010 Juniper Networks Inc 22 Configuring Secure Access Devices Guide...
Страница 46: ...Copyright 2010 Juniper Networks Inc 28 Configuring Secure Access Devices Guide...
Страница 50: ...Copyright 2010 Juniper Networks Inc 32 Configuring Secure Access Devices Guide...
Страница 52: ...Copyright 2010 Juniper Networks Inc 34 Configuring Secure Access Devices Guide...
Страница 82: ...Copyright 2010 Juniper Networks Inc 64 Configuring Secure Access Devices Guide...
Страница 110: ...Copyright 2010 Juniper Networks Inc 92 Configuring Secure Access Devices Guide...
Страница 154: ...Copyright 2010 Juniper Networks Inc 136 Configuring Secure Access Devices Guide...
Страница 224: ...Copyright 2010 Juniper Networks Inc 206 Configuring Secure Access Devices Guide...
Страница 234: ...Copyright 2010 Juniper Networks Inc 216 Configuring Secure Access Devices Guide...
Страница 288: ...Copyright 2010 Juniper Networks Inc 270 Configuring Secure Access Devices Guide...
Страница 300: ...Copyright 2010 Juniper Networks Inc 282 Configuring Secure Access Devices Guide...
Страница 310: ...Copyright 2010 Juniper Networks Inc 292 Configuring Secure Access Devices Guide...
Страница 312: ...Copyright 2010 Juniper Networks Inc 294 Configuring Secure Access Devices Guide...
Страница 320: ...Copyright 2010 Juniper Networks Inc 302 Configuring Secure Access Devices Guide...
Страница 322: ...Copyright 2010 Juniper Networks Inc 304 Configuring Secure Access Devices Guide...
Страница 337: ...PART 6 Index Index on page 321 319 Copyright 2010 Juniper Networks Inc...
Страница 338: ...Copyright 2010 Juniper Networks Inc 320 Configuring Secure Access Devices Guide...
Страница 340: ...Copyright 2010 Juniper Networks Inc 322 Configuring Secure Access Devices Guide...