Preface
viii
Getting Technical Support
Introduction
ISS provides technical support through its Web site and by email or telephone.
The ISS Web site
The Internet Security Systems (ISS) Resource Center Web site (
http://www.iss.net/
support/
) provides direct access to much of the information you need. You can find
frequently asked questions (FAQs), white papers, online documentation, current versions
listings, detailed product literature, and the Technical Support Knowledgebase (
http://
www.iss.net/support/knowledgebase/
).
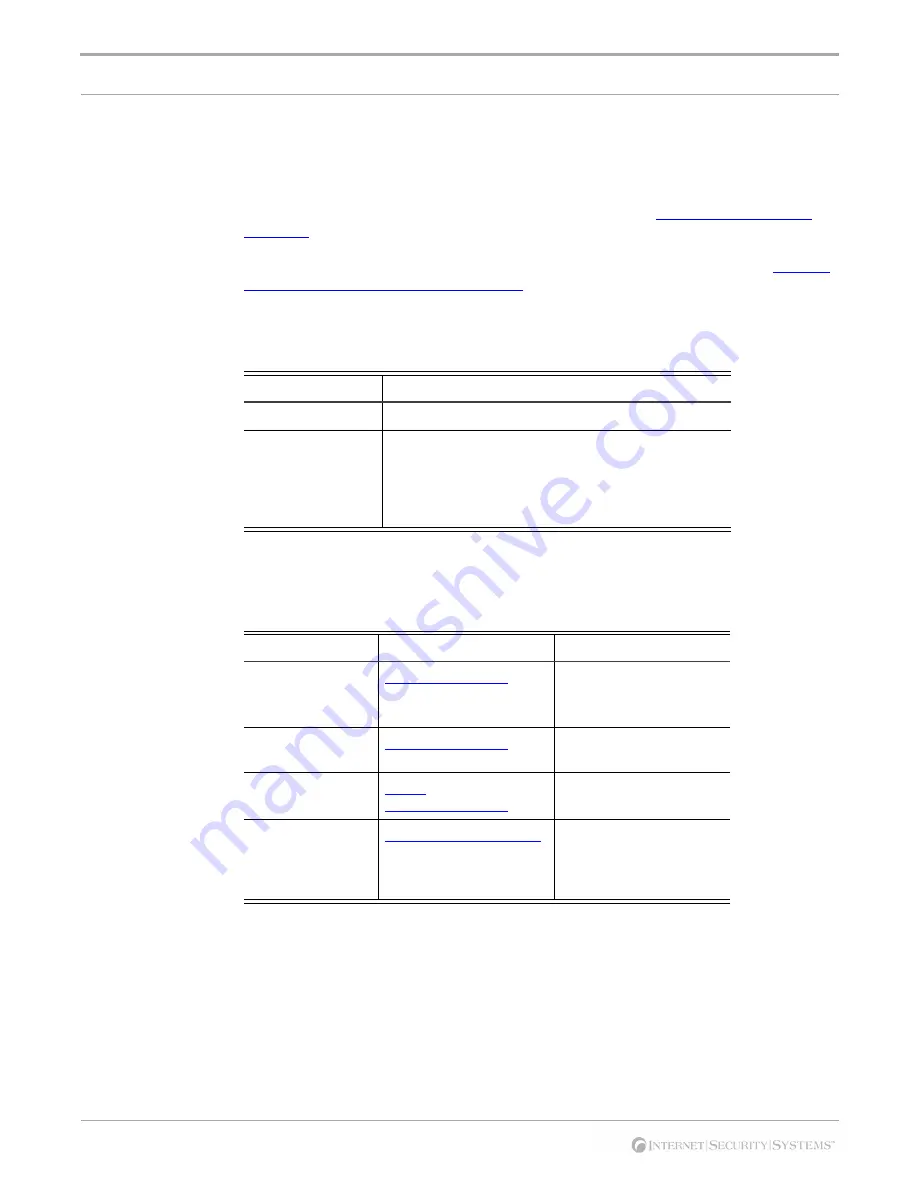
Hours of support
The following table provides hours for Technical Support at the Americas and other
locations:
Contact information
The following table provides email addresses and telephone numbers for technical
support requests:
Location
Hours
Americas
24 hours a day
All other locations
Monday through Friday, 9:00 A.M. to 6:00 P.M. during
their local time, excluding ISS published holidays
Note:
If your local support office is located outside the
Americas, you may call or email the Americas office for
help during off-hours.
Table 3:
Hours for technical support
Regional Office
Email Address
Telephone Number
North America and
Latin America
(1) (888) 447-4861 (toll
free)
(1) (404) 236-2700
Europe, Middle
East, and Africa
(44) (118) 959-3900
Asia-Pacific and
Philippines
asia-
(63) (2) 886-6014
Japan
Domestic: (81) (3) 5740-
4065
Overseas (APAC): (81) (3)
5740-4066
Table 4:
Contact information for technical support
Содержание RealSecure
Страница 1: ...TM Desktop Protector User Guide Version 3 5 ...
Страница 28: ...Chapter 2 Using RealSecure Desktop Protector with ICEcap Manager 20 ...
Страница 38: ...Chapter 3 Setting Up RealSecure Desktop Protector 30 ...
Страница 49: ...Ignoring Events 41 For more information see The Prompts Tab on page 83 ...
Страница 66: ...Chapter 4 Configuring RealSecure Desktop Protector 58 ...
Страница 67: ...TM Appendixes ...
Страница 68: ......
Страница 96: ...Appendix B Configuration Tabs 88 ...
Страница 106: ...Appendix C Advanced Firewall Settings 98 ...
Страница 112: ...Appendix D Advanced Application Protection Settings 104 ...
Страница 120: ...Appendix E The Main Menu 112 ...
Страница 124: ...Index 116 ...









































