Set Up User Access
Setup
•
13
for the username and password. If found, the E2 will log
the user in at the access level chosen for the user in the
user records.
The access level determines how many of the E2’s fea-
tures the user may use. The E2 uses four access levels, one
being the lowest, and four being the highest.
gives a description of each level and the capabilities they
have access to.
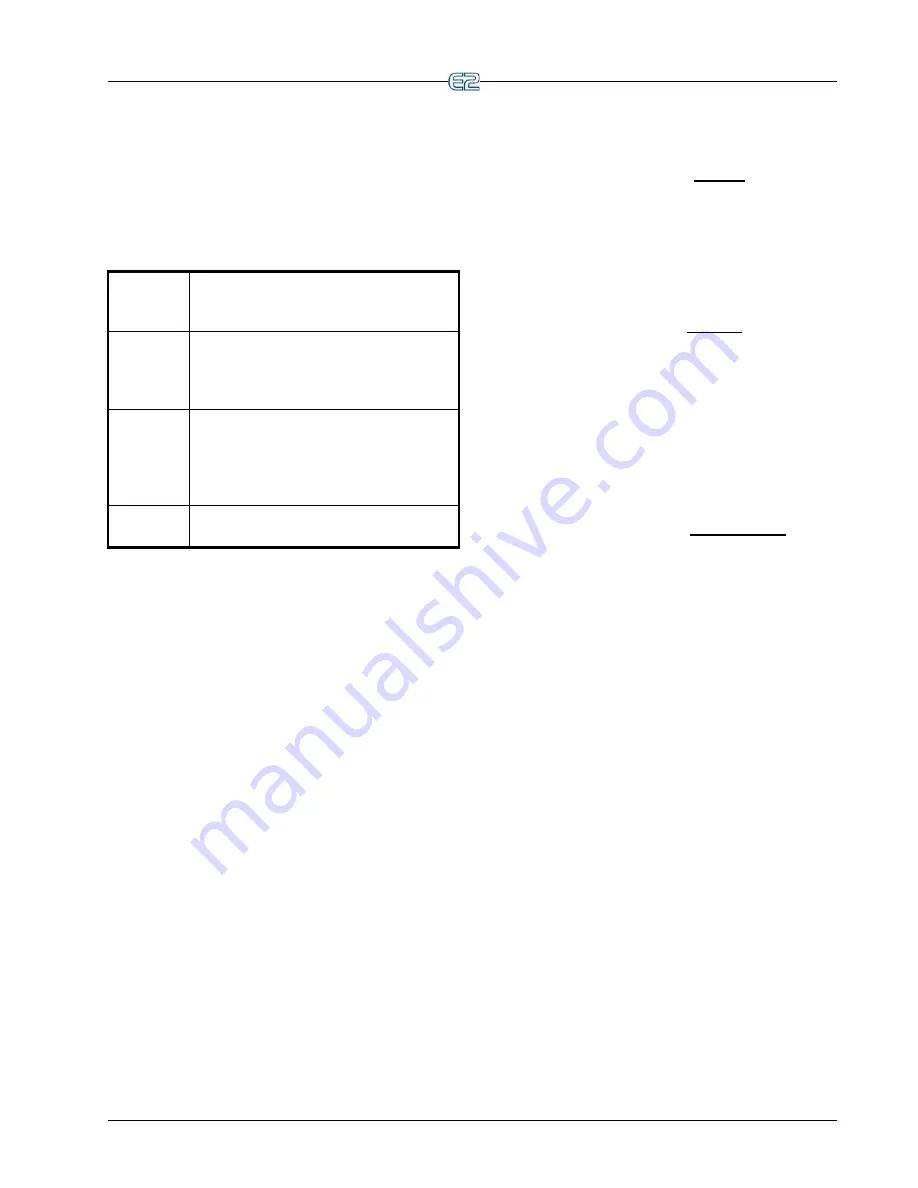
Table 3-2
- User Access Levels
Level 1
Read-only access. Users may generally only
view status screens, setpoints, and some
system settings.
Level 2
Setpoint and bypass access. Users may per-
form all the tasks a level 1 user may, plus
they may change control setpoints and
bypass some devices.
Level 3
Configuration and override access. Users
may perform all the tasks a level 2 user
may, plus they may override system set-
tings, create new cells, and program new
applications.
Level 4
System Administrator access. All E2 func-
tions are accessible by a level 4 user.
3.5.1
Changing Required User
Access Levels
The
Level Required For
table in this screen is used to
customize what access level is required to perform certain
actions within the E2 unit. There are four rows in this
table, each of which corresponds to a different type of E2
function or application.
•
Refrigeration Control -
This category includes
changes or actions involving refrigeration applica-
tions specific to RX controllers (Suction Groups,
Condensers, Circuits, CC-100s, etc.).
•
Building Control -
This category includes changes
or actions involving building control applications
specific to BX controllers (AHUs, Zones, Lighting
Control, Time Schedule, Demand Control, etc.).
•
Common Control -
This category includes control
applications common to both RX and BX control-
lers (Sensor Control, Time Schedules, Conversion
Cells, Analog or Digital Combiners, Global Data,
etc.).
•
Advanced Control -
This category includes applica-
tions common to both boxes that are only used by
advanced users, such as Loop/Sequence Control-
lers, Refrigeration or HVAC Simulations, etc.
Each row has five columns, each of which corresponds
to a different category of user actions.
•
Setpoint -
This includes all actions that change
application setpoints. Also,
clearing
one or more
alarms out of the Alarm Advisory Log is considered
a “setpoint” action (refer to the
Operator’s Guide to
Using the E2
section of the E2 manual (
P/N 026-
1614
) for the definition of “clearing alarms”).
•
Bypass -
This includes all actions that bypass a
device to a certain state, such as initiating a manual
defrost, or configuring an application input desig-
nated as a “bypass.” Also,
resetting
one or more
alarms in the Alarm Advisory Log is considered a
“bypass” operation (refer to the
Operator’s Guide
to Using the E2
section of the E2 manual (
P/N 026-
1614
) for the definition of “resetting alarms”).
•
Override -
This includes any user-ordered override
of a setpoint, input, or output.
•
Config -
This includes all actions that change an
application setting. This includes configuring inputs
and outputs.
•
Alarm Ack -
This includes
acknowledging
one or
more alarms in the Alarm Log. If this field is set to
1, alarms can be acknowledged on the Alarm Advi-
sory Log without a user logging into the controller
first. If set to 2, 3, or 4, login is required before a
user can acknowledge alarms. The default is set to 3
(controller login required for acknowledging
alarms). Refer to the
Operator’s Guide to Using the
E2
section of the E2 manual (
P/N 026-1614
) for the
definition of “acknowledging alarms.”
For each row and column of the Level Required For
table, enter the desired minimum priority level that will be
required for users to perform actions on each type of appli-
cation. E2 will check this table when a user attempts an
action to verify the user has the appropriate access level to
make the change. If the user’s access level is equal to or
above the priority setting in the table, access will be
allowed. If not, access will be denied.
3.5.2
Creating a New User
Account
After entering the User Access Setup screen by press-
ing
Passwords/User Access
from the System Infor-
mation menu:
1.
Move the cursor so that it is somewhere in the
Users
box at the bottom of the screen.
2.
Press
(ADD USER) to put a blank record at
the bottom of the list.






























