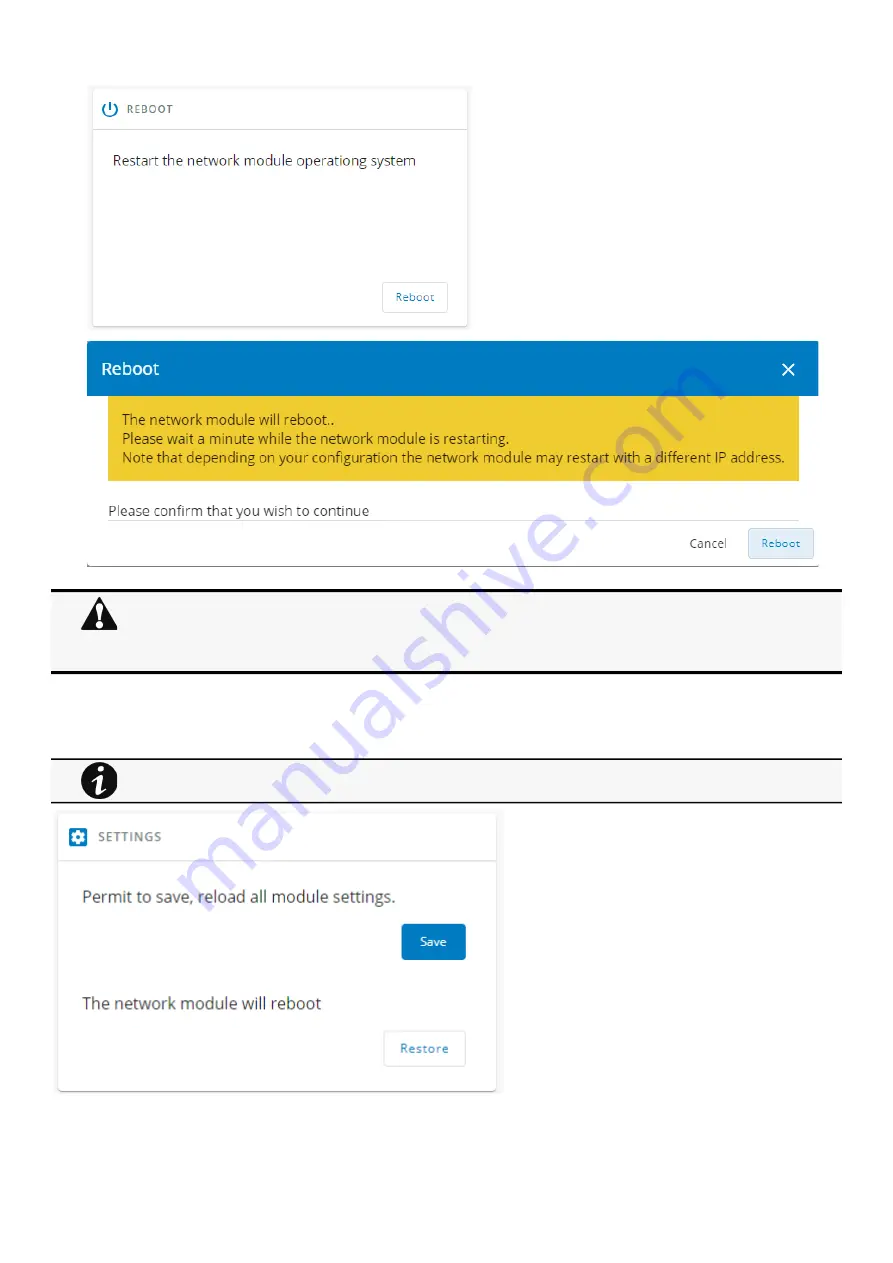
Maintenance
Contextual help of the web interface – 147
3.8.3.1.3
Settings
Allow to save and restore the Network module settings.
Depending on your network configuration, the Network Module may restart with a different IP address.
Refresh the browser after the Network module reboot time to get access to the login page.
Communication Lost and Communication recovered may appear in the Alarm section.
For more details, navigate to
Servicing the Network Management Module>>>Saving/Restoring/Duplicating
section.
Содержание INDGW-X2
Страница 1: ...UPS Industrial Gateway Card INDGW X2 User s Guide English 10 18 2021 2 2 3 ...
Страница 23: ...Configuring Modbus Installing the Network Management Module 25 ...
Страница 24: ...Configuring Modbus Installing the Network Management Module 26 ...
Страница 25: ...Configuring Modbus Installing the Network Management Module 27 ...
Страница 26: ...Configuring Modbus Installing the Network Management Module 28 ...
Страница 35: ...Home Contextual help of the web interface 37 3 2 7 1 3 Battery mode 3 2 7 1 4 Off mode ...
Страница 37: ...Home Contextual help of the web interface 39 3 2 7 2 2 Bypass mode 3 2 7 2 3 Battery mode ...
Страница 61: ...Protection Contextual help of the web interface 63 Example 4 Custom ...
Страница 62: ...Protection Contextual help of the web interface 64 Settings 1 Settings 2 ...
Страница 218: ...Default settings and possible parameters Information 220 ...
Страница 266: ...Acronyms and abbreviations Information 268 ...
Страница 273: ......






























