xStack DES-3500 Series Layer 2 Stackable Fast Ethernet Managed Switch User Manual
88
Priority (0-7)
This parameter is specified if you want to re-write the 802.1p default priority previously set in
the Switch, which is used to determine the CoS queue to which packets are forwarded to.
Once this field is specified, packets accepted by the Switch that match this priority are
forwarded to the CoS queue specified previously by the user.
Replace Priority with
−
Click the corresponding box if you want to re-write the 802.1p default
priority of a packet to the value entered in the Priority (0-7) field, which meets the criteria
specified previously in this command, before forwarding it on to the specified CoS queue.
Otherwise, a packet will have its incoming 802.1p user priority re-written to its original value
before being forwarded by the Switch.
For more information on priority queues, CoS queues and mapping for 802.1p, see the QoS
section of this manual.
VLAN Name
Allows the entry of a name for a previously configured VLAN.
Source MAC
Source MAC Address - Enter a MAC Address for the source MAC address.
Destination MAC
Destination MAC Address - Enter a MAC Address mask for the destination MAC address.
802.1p (0-7)
Enter a value from
0
to
7
to specify that the access profile will apply only to packets with this
802.1p priority value.
Ethernet Type
Specifies that the access profile will apply only to packets with this hexadecimal 802.1Q
Ethernet type value (hex 0x0-0xffff) in the packet header. The Ethernet type value may be
set in the form: hex 0x0-0xffff, which means the user may choose any combination of letters
and numbers ranging from a-f and from 0-9999.
Port Number
Enter the switch port number(s) to which you wish this rule to apply.
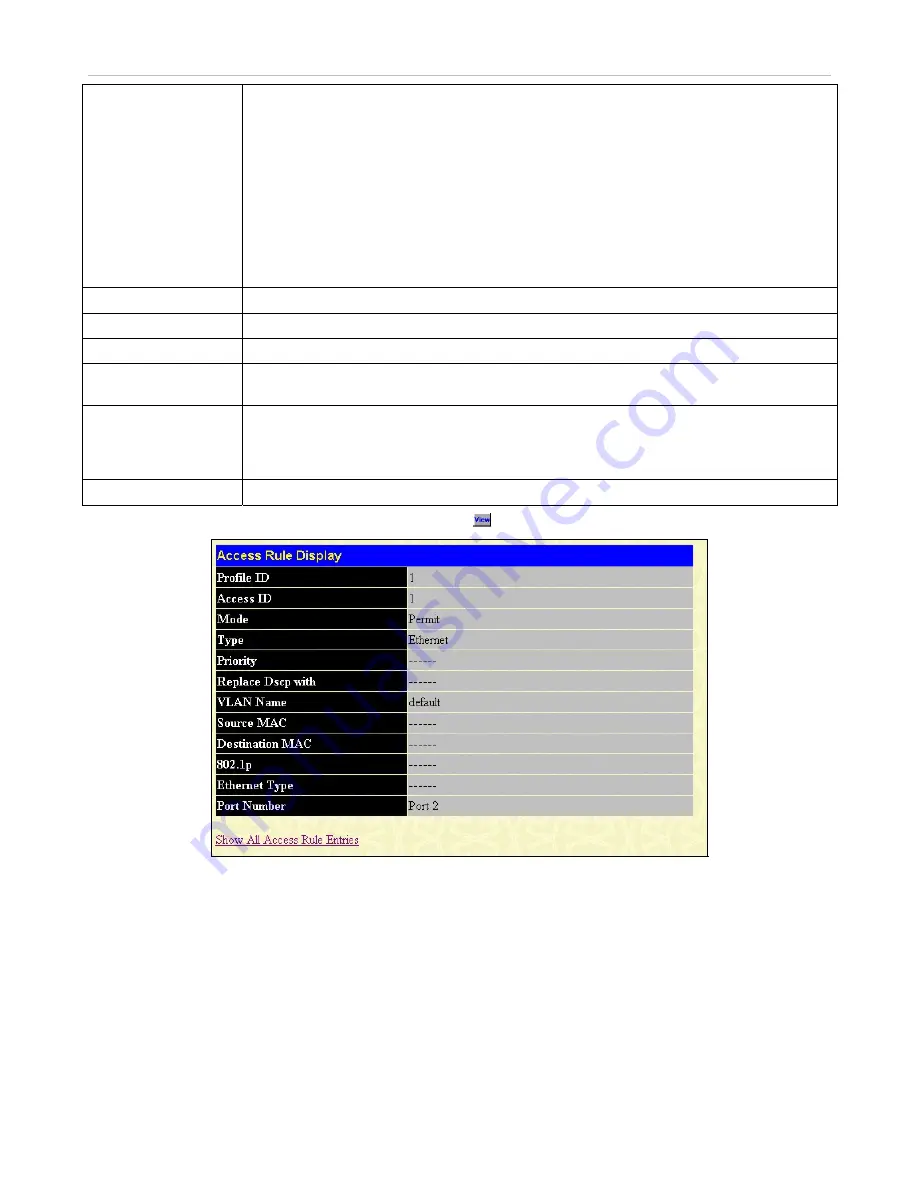
To view the settings of a previously correctly configured rule, click
in the
Access Rule Table
to view the following window:
Figure 6- 66. Access Rule Display window (Ethernet)
To configure the Access Rule for Packet Content Mask, open the Access Profile Table and click
Modify
for a Packet Content
Mask entry. This will display the Access Rule Table.






























