Windows XP client and PPTP server
Settings for the Windows XP client
1.
Open the control panel (Start button -> Control panel).
2.
If you are using the Category view, click on the
Network and Internet Connections
icon. Then click
Create a connection to
the network on your workplace
and
continue to step 6.
If you are using the Classic view, click on the
Network Connections
icon.
3.
Under Network task, click
Create a new
connection
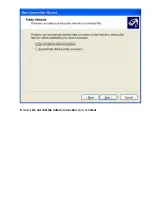
4.
The
New connection wizard
window opens up. Click
next
.
Содержание DFL-200 - Security Appliance
Страница 1: ...D Link DFL 200 Network Security Firewall Manual Building Networks for People Ver 1 02 20050419 ...
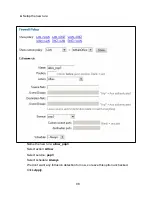
Страница 102: ...102 5 Select Connect to the network at my workplace and click Next ...
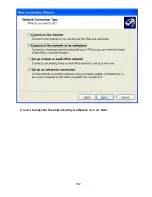
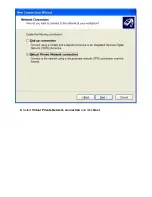
Страница 103: ...6 Select Virtual Private Network connection and click Next ...
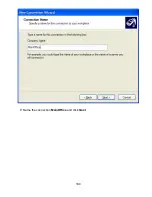
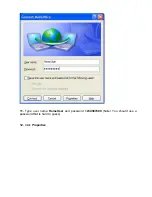
Страница 104: ...104 7 Name the connection MainOffice and click Next ...
Страница 105: ...8 Select Do not dial the initial connection and click Next ...
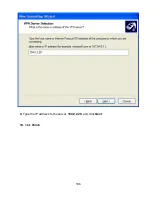
Страница 106: ...106 9 Type the IP address to the server 194 0 2 20 and click Next 10 Click Finish ...
Страница 129: ...VCCI Warning ...
Страница 132: ...132 ...
Страница 133: ......