78
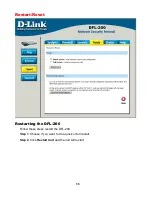
Step by step guides
In the following guides example IPs, users, sites and passwords are used. You will have to
exchange the IP addresses and sites to your own. Passwords used in these examples are not
recommended for real life use. Passwords and keys should be chosen so that they are
impossible to guess or find out by eg a dictionary attack.
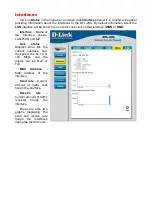
In these guides for example
Firewall->Users
will mean that
Firewall
first should be
selected from the menu at the top of the screen,
and than the
Users
button to the left of the screen.
Содержание DFL-200 - Security Appliance
Страница 1: ...D Link DFL 200 Network Security Firewall Manual Building Networks for People Ver 1 02 20050419 ...
Страница 102: ...102 5 Select Connect to the network at my workplace and click Next ...
Страница 103: ...6 Select Virtual Private Network connection and click Next ...
Страница 104: ...104 7 Name the connection MainOffice and click Next ...
Страница 105: ...8 Select Do not dial the initial connection and click Next ...
Страница 106: ...106 9 Type the IP address to the server 194 0 2 20 and click Next 10 Click Finish ...
Страница 129: ...VCCI Warning ...
Страница 132: ...132 ...
Страница 133: ......