EN
UVIX suite User Manual
15
Before describing how to manage the user registry effectively, it is
necessary to understand how to correctly configure users to ensure that
they can only access the required features.
In order to limit/control access to certain features, the UVIX system uses
two different concepts: Profiles and Authorisations.
PROFILES
Users can have two profiles:
1.
User
: profile for users intending to only monitor devices or perform
limited functions.
2.
Installer
: profile to be assigned to the system managers who must make
adjustments and device configurations.
AUTHORISATIONS
The authorisations instead allow you to specify which of the available
features are assigned to a specific user. The authorisations available are:
•
Manage registries
: permission to manage registries of users, devices
and device groups
•
Manage command
: authorisation to send commands
•
Manage setup parameter
: authorisation to configure device and slave
setup parameters
The following explains how some basic features of the web app are
influenced by profiles and authorisations.
Variables
Each variable can only be viewed by users with a specific profile. Therefore,
some variables can be seen by both users belonging to the User and the
Installer profiles, while other variables can only be viewed by users
belonging to the Installer profile.
3.3 User registry management
Registries of Machines and Device groups:
A user can create or edit these registries if they have authorisation to Manage
registries. The profile to which a user belongs is insignificant.
User registries
A user can create or edit users if they have authorisation to Manage registries.
Furthermore, a user will only be able to manage users with a profile lower
than or equal to their own: a user belonging to the User profile can create
or edit users with a User profile. A user belonging to the Installer profile can
create or edit users with both a User and Installer profile.
Device registries
For complete access to device registry management, you must have
authorisation to Manage registries, but instead, in order to add a device
via notifications on the top bar, you do not need to have any particular
authorisation.
Commands
A user must have Manage command authorisation in order to send commands.
The commands, unlike the variables, do not have a level and, therefore, the
profile to which the user belongs is irrelevant.
Configuration
In order to view/edit the configuration of a device or a slave, a user must have
Manage setup parameter authorisation. The setup parameters, similarly to
the variables, are associated with a level. A parameter can only be viewed
and/or edited by users with a profile greater than or equal to the level of
the parameter itself. Therefore, a level 1 parameter can be viewed and/or
edited by users belonging to the User and Installer profile, whereas a level
2 parameter can only be viewed and/or edited by users belonging to the
Installer profile.
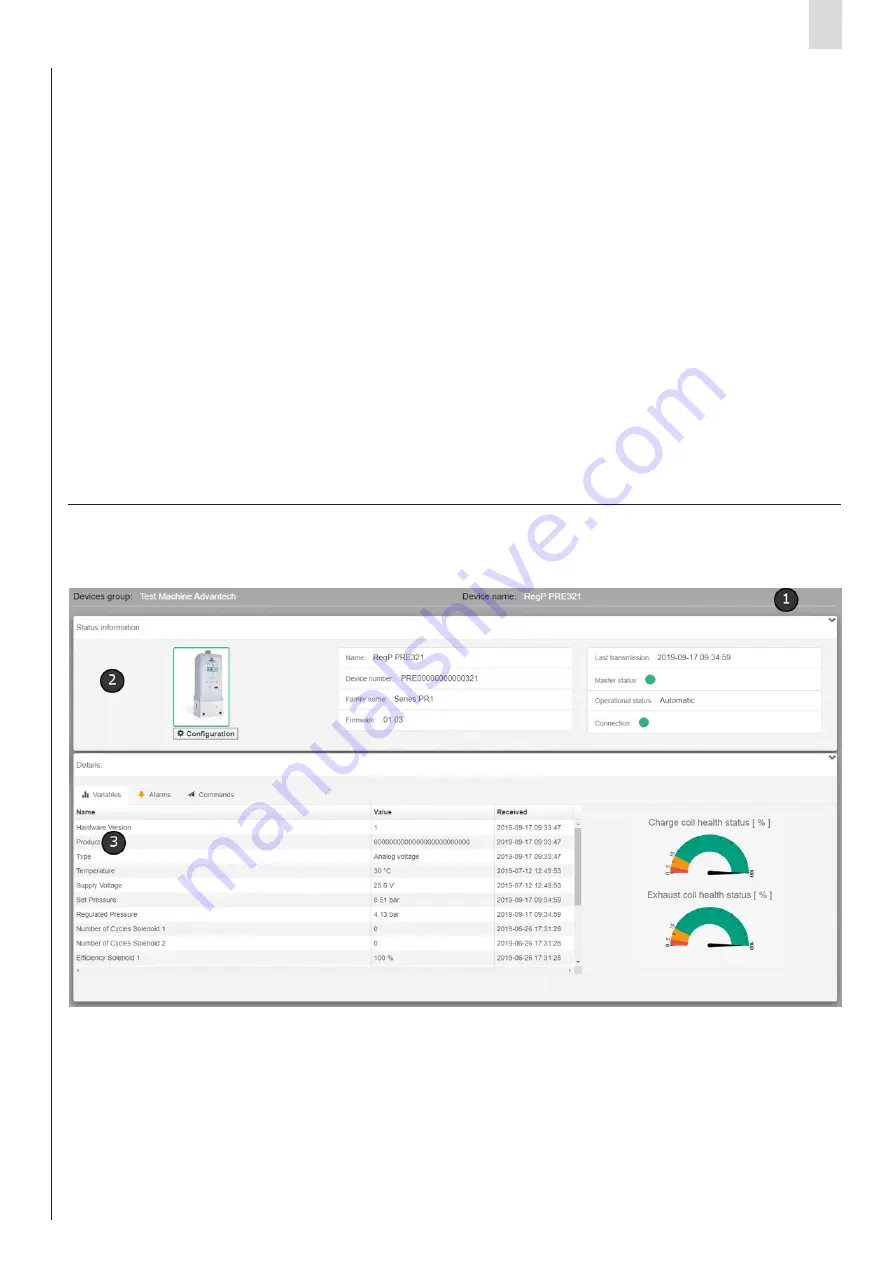
In order to access device management, you have to select it from the
treeView in the left bar.
The device management page is divided into 3 macro-areas:
• Header
[1]
: the name assigned by the user to the selected device and the
name of the device group to which it belongs are displayed.
• Status information
[2]
: the following fields related to the selected device
are displayed.
- An image which represents it with a coloured border based on its
overall status.
-
Name
: name assigned by the user.
-
Family name
: description of the type.
-
Firmware
: firmware version.
-
Last trasmission
: date and time of the last data received.
-
Master status
: overall status.
-
Slaves status
: status of the slaves (only if the device has slaves).
-
Operational status
: operational status.
-
Connection
: indicates whether the device is transmitting or more precisely
whether the FEP is receiving data from it. The indication is shown by the
colour of the dot which turns green if the device is connected or red if not.
- Under the image of the device, there may be a “Configuration” button,
if required, which allows the user to open the configuration window of the
selected device.
• Details
[3]
: it is divided in turn into three tabs:
-
Variables
: consisting of a table showing the variables sent by the device
accompanied by their value and the date of receipt. For more information,
see the paragraph "Variables".
-
Alarm
: consisting of a table showing all possible alarms that the device
may trigger. For more information, see the paragraph "Alarms".
-
Commands
: allows the user to send commands and see the command
history. For more information, see the paragraph "Commands".
3.4
Device management






















