105
Use ESP for greater security so that data will be encrypted and the data origin be authenticated but
using AH data origin will only be authenticated but not encrypted.
Encryption Algorithm:
Select the encryption algorithm from the drop-down menu. There are several
options: DES and AES (128, 192 and 256). 3DES and AES are more powerful but increase latency.
DES:
Stands for Data Encryption Standard, it uses 56 bits as an encryption method.
3DES:
Stands for Triple Data Encryption Standard, it uses 168 (56*3) bits as an encryption
method.
AES:
Stands for Advanced Encryption Standards, you can use 128, 192 or 256 bits as
encryption method.
Authentication Algorithm:
Authentication establishes the integrity of the datagram and ensures it is
not tampered with in transmission. There are 3 options: Message Digest 5 (MD5) and Secure Hash
Algorithm (SHA1, SHA256). SHA1 is more resistant to brute-force attacks than MD5. However, it is
slower.
MD5:
A one-way hashing algorithm
that produces a 128−bit hash.
SHA1:
A one-
way hashing algorithm that produces a 160−bit hash.
Perfect Forward Secrecy:
It is a public-key cryptography protocol that allows two parties to establish
a shared secret over an unsecured communication channel (i.e. over the Internet). MODP stands for
Modular Exponentiation Groups.
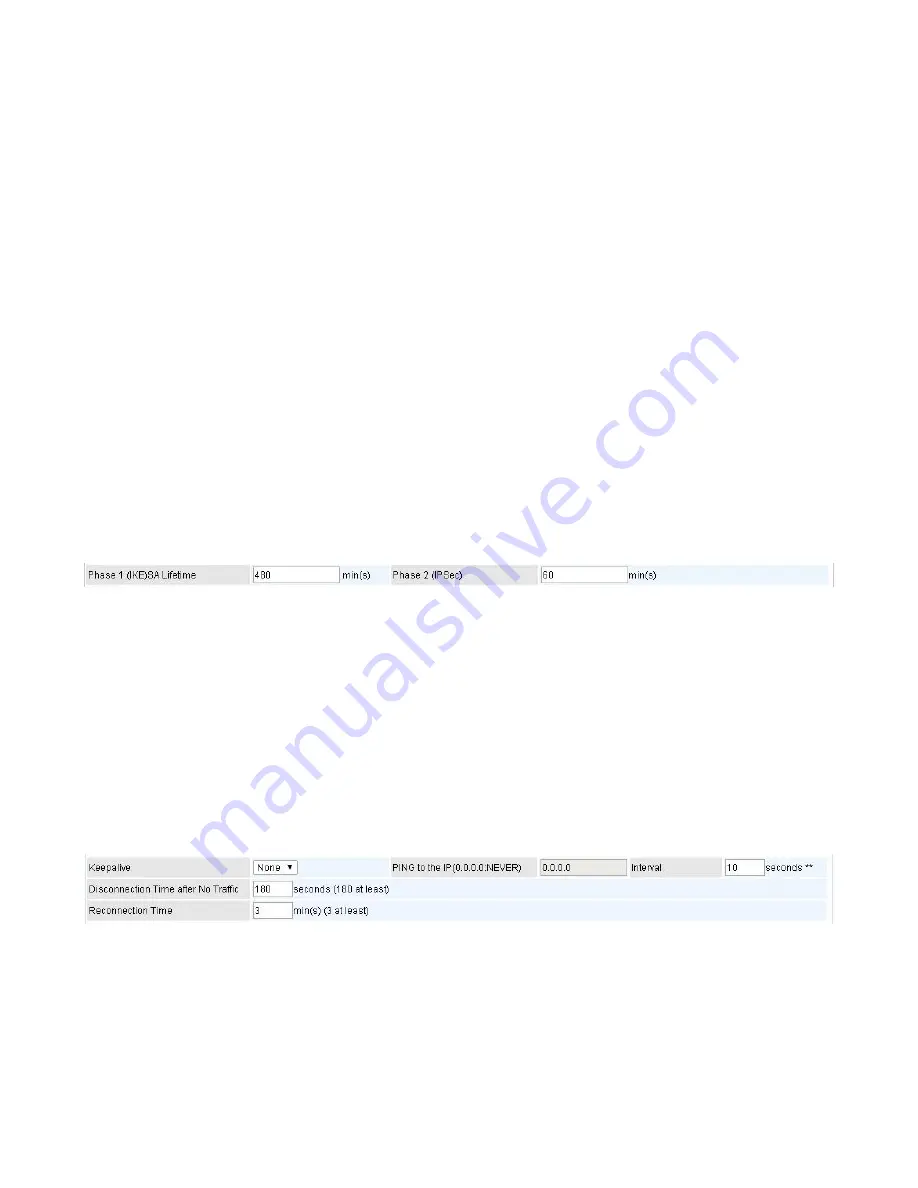
IPSec SA Lifetime
SA Lifetime:
Specify the number of minutes that a Security Association (SA) will stay active before
new encryption and authentication key will be exchanged. There are two kinds of SAs, IKE and IPSec.
IKE negotiates and establishes SA on behalf of IPSec, an IKE SA is used by IKE.
Phase 1 (IKE):
To issue an initial connection request for a new VPN tunnel. The range can be
from 5 to 15,000 minutes, and the default is 480 minutes.
Phase 2 (IPSec):
To negotiate and establish secure authentication. The range can be from 5 to
15,000 minutes, and the default is 60 minutes. A short SA time increases security by forcing the
two parties to update the keys. However, every time the VPN tunnel re-negotiates, access
through the tunnel will be temporarily disconnected.
IPSec Conneciton Keep Alvie
Keep Alive:
None:
The default setting is None. To this mode, it will not detect the remote IPSec peer has
been lost or not. It only follows the policy of Disconnection time after no traffic, which the remote
IPSec will be disconnected after the time you set in this function.
PING:
This mode will detect the remote IPSec peer has lost or not by pinging specify IP
address.
DPD:
Dead peer detection (DPD) is a keeping alive mechanism that enables the router to be
detected lively when the connection between the router and a remote IPSec peer has lost.
Содержание M500
Страница 4: ...3 Problem with LAN Interface 174 Recovery Procedures 174 Appendix Product Support Contact 176 ...
Страница 20: ...16 The wire colors shown are for the power GPIO cable that comes with the Industrial LTE Router optional ...
Страница 31: ...27 GPS Status In GPS status you can check the UTC time position of the router ...
Страница 32: ...28 Hardware Monitor In hardware monitor you can check the voltage current and temperature of system ...
Страница 50: ...46 Interface Setup Here are the features under Interface Setup Internet LAN Wireless and Wireless MAC Filter ...
Страница 53: ...49 EWAN ...
Страница 58: ...54 Use Scan button to scan the available SSIDs in the air find your desired on type the encypytion key ...
Страница 69: ...65 ...
Страница 90: ...86 ...















































