Report Wizard
Issue 4 May 2005
271
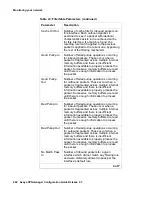
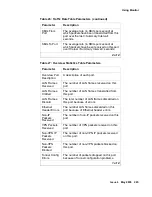
The first Report wizard screen allows you to specify the objects you wish to include in the report.
The available objects include:
●
IP Group
●
User
●
User Group
●
Device (security gateway)
●
VPN
To create a report using the report wizard:
1. Move to the Main Console.
2. Click Report to start the Report Wizard.
3. In the Report Contents portion of the screen, select the object types to be included in the
report.
4. The Select All and Deselect All buttons are provided for convenience.
5. Click Next.
6. In the Show Report Title text box, type the report title.
7. Report format details including date and time, report title, author, page numbering, and the
type font and font size.
8. The available font types are: Arial, Times Roman, and Helvetica. The available font sizes
range from 8 points to 72 points.
9. Click Next.
10. Depending on the objects selected in the initial screen, each object is displayed as part of
the report wizard.
11. Select the desired object groups to be included in the report.
Note:
Note:
The Summary button presents a single-screen overview of all the currently set
report selections and options. Advanced users may wish to jump to this screen
immediately.
12. Click Next.
13. Select additional information for the object group to be included in the report.
14. Click Next.
15. Click Finished when all report information has been selected.
16. You then have a choice of the output file type, HTML or PDF. The output file may be viewed
on the screen, then sent to a printer if hardcopy is desired. Be sure you have an Adobe
Acrobat reader to view the PDF file, or a web browser to view the HTML file.
Содержание 3.7
Страница 1: ...VPNmanager Configuration Guide Release 3 7 670 100 600 Issue 4 May 2005...
Страница 4: ......
Страница 20: ...Preface 20 Avaya VPNmanager Configuration Guide Release 3 7...
Страница 32: ...Overview of implementation 32 Avaya VPNmanager Configuration Guide Release 3 7...
Страница 53: ...Preferences Issue 4 May 2005 53 Figure 16 Tunnel End Point Policy...
Страница 54: ...Using VPNmanager 54 Avaya VPNmanager Configuration Guide Release 3 7...
Страница 244: ...Using advanced features 244 Avaya VPNmanager Configuration Guide Release 3 7...
Страница 292: ...Upgrading firmware and licenses 292 Avaya VPNmanager Configuration Guide Release 3 7...