3. CONFIGURATION
3.8
Firewall Configuration
The first security element which incoming packets pass is a check of the enabled source
IP addresses and destination ports. You can specify the IP addresses as an IP address from
which you can remotely access the router and the internal network connected behind a router.
To enable this function, marking the
Enable filtering of incoming packets
check box located
at the top of the
Firewall Configuration
page. Accessibility is checked against the IP address
table. This means that access is permitted only to addresses specified in the table. It is pos-
sible to specify up to eight remote IP addresses for access. You can specify the following
parameters:
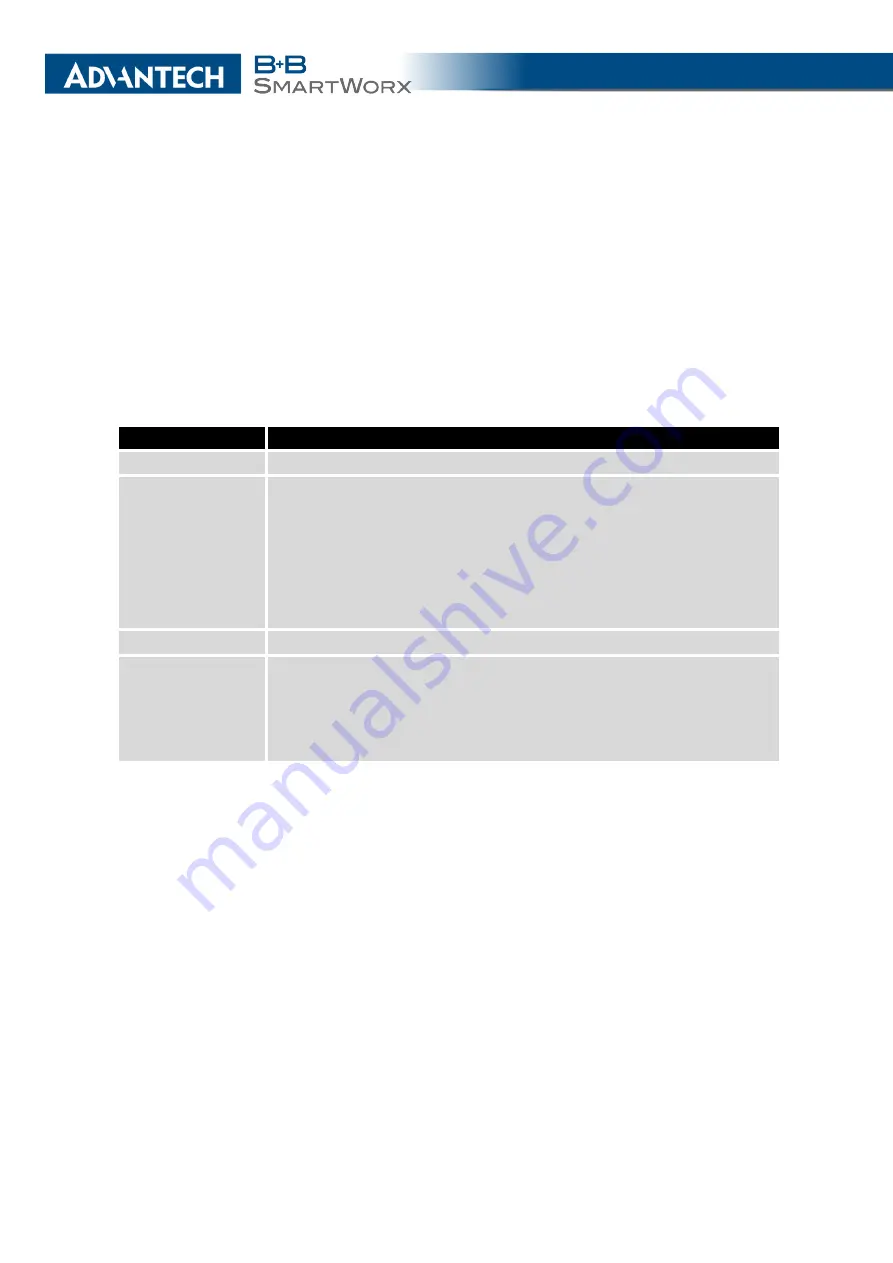
Item
Description
Source
IP address from which access to the router is allowed.
Protocol
Specifies the protocol used for remote access:
•
all
– Access for all protocols is active.
•
TCP
– Access for the TCP protocol is active.
•
UDP
– Access for the UDP protocol is active.
•
ICMP
– Access for the ICMP protocol is active.
Target Port
The port number on which access to the router is allowed.
Action
Specifies the type of action the router performs:
•
allow
– The router allows the packets to enter the network.
•
deny
– The router denies the packets from entering the network
Table 31: Filtering of Incoming Packets
The next section of the configuration form specifies the forwarding policy. If you unmark
the
Enabled filtering of forwarded packets
check box, then packets are automatically accepted.
If you activate this function, and a packet is addressed to another network interface, then the
router sends the packet to the FORWARD chain. When the FORWARD chain accepts the
packet and there is a rule for forwarding it, the router sends the packet. If a forwarding rule is
unavailable, then the router drops the packet.
This configuration form also contains a table for specifying the filter rules. It is possible
to create a rule to allow data with the selected protocol by specifying only the protocol, or to
create stricter rules by specifying values for source IP addresses, destination IP addresses,
and ports.
49
Содержание B+B SmartWorx LR77 v2
Страница 1: ...Configuration Manual for v2 Routers ...
Страница 18: ...2 STATUS WiFi Scan output may look like this Figure 4 WiFi Scan 11 ...
Страница 29: ...3 CONFIGURATION Figure 12 Example 1 LAN Configuration Page 22 ...
Страница 34: ...3 CONFIGURATION Figure 19 Example of VRRP configuration backup router 27 ...
Страница 42: ...3 CONFIGURATION Figure 20 Mobile WAN Configuration 35 ...
Страница 50: ...3 CONFIGURATION Figure 24 WiFi Configuration 43 ...
Страница 75: ...3 CONFIGURATION Figure 36 IPsec Tunnels Configuration 68 ...
Страница 105: ...3 CONFIGURATION Figure 54 Expansion Port Configuration 98 ...
Страница 110: ...3 CONFIGURATION Figure 59 Example 2 USB port configuration 103 ...
















































