Chapter 8 WAN Screens
ZyWALL 5/35/70 Series User’s Guide
181
Figure 97
NETWORK > WAN > WAN (Ethernet Encapsulation)
The following table describes the labels in this screen.
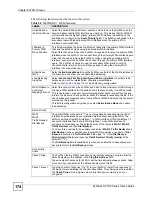
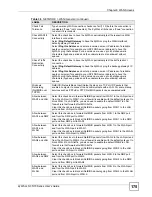
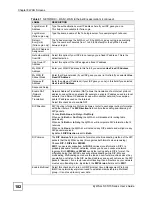
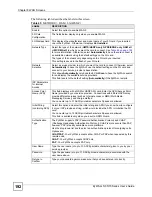
Table 41
NETWORK > WAN > WAN (Ethernet Encapsulation)
LABEL
DESCRIPTION
ISP Parameters
for Internet
Access
Encapsulation
You must choose the
Ethernet
option when the WAN port is used as a regular
Ethernet.
Service Type
Choose from
Standard
,
Telstra
(RoadRunner Telstra authentication method),
RR-
Manager
(Roadrunner Manager authentication method),
RR-Toshiba
(Roadrunner Toshiba authentication method) or
Telia Login
.
The following fields do not appear with the
Standard
service type.
User Name
Type the user name given to you by your ISP.
Password
Type the password associated with the user name above.
Retype to
Confirm
Type your password again to make sure that you have entered is correctly.
Summary of Contents for ZyWALL 35 Series
Page 2: ......
Page 8: ...Safety Warnings ZyWALL 5 35 70 Series User s Guide 8 ...
Page 52: ...List of Tables ZyWALL 5 35 70 Series User s Guide 52 ...
Page 54: ...54 ...
Page 60: ...Chapter 1 Getting to Know Your ZyWALL ZyWALL 5 35 70 Series User s Guide 60 ...
Page 86: ...Chapter 2 Introducing the Web Configurator ZyWALL 5 35 70 Series User s Guide 86 ...
Page 140: ...Chapter 4 Tutorials ZyWALL 5 35 70 Series User s Guide 140 ...
Page 146: ...Chapter 5 Registration ZyWALL 5 35 70 Series User s Guide 146 ...
Page 148: ...148 ...
Page 160: ...Chapter 6 LAN Screens ZyWALL 5 35 70 Series User s Guide 160 ...
Page 173: ...Chapter 8 WAN Screens ZyWALL 5 35 70 Series User s Guide 173 Figure 93 NETWORK WAN General ...
Page 202: ...Chapter 8 WAN Screens ZyWALL 5 35 70 Series User s Guide 202 ...
Page 212: ...Chapter 9 DMZ Screens ZyWALL 5 35 70 Series User s Guide 212 ...
Page 242: ...242 ...
Page 274: ...Chapter 11 Firewall ZyWALL 5 35 70 Series User s Guide 274 ...
Page 294: ...Chapter 13 Configuring IDP ZyWALL 5 35 70 Series User s Guide 294 ...
Page 320: ...Chapter 15 Anti Spam ZyWALL 5 35 70 Series User s Guide 320 ...
Page 342: ...Chapter 16 Content Filtering Screens ZyWALL 5 35 70 Series User s Guide 342 ...
Page 350: ...Chapter 17 Content Filtering Reports ZyWALL 5 35 70 Series User s Guide 350 ...
Page 424: ...Chapter 19 Certificates ZyWALL 5 35 70 Series User s Guide 424 ...
Page 430: ...430 ...
Page 448: ...Chapter 21 Network Address Translation NAT ZyWALL 5 35 70 Series User s Guide 448 ...
Page 474: ...Chapter 24 Bandwidth Management ZyWALL 5 35 70 Series User s Guide 474 ...
Page 514: ...Chapter 26 Remote Management ZyWALL 5 35 70 Series User s Guide 514 ...
Page 533: ...533 PART V Reports Logs and Maintenance Reports 535 Logs Screens 547 Maintenance 575 ...
Page 534: ...534 ...
Page 551: ...Chapter 31 Logs Screens ZyWALL 5 35 70 Series User s Guide 551 Figure 334 LOGS Log Settings ...
Page 592: ...Chapter 32 Maintenance ZyWALL 5 35 70 Series User s Guide 592 ...
Page 594: ...594 Troubleshooting 751 Product Specifications 757 ...
Page 602: ...Chapter 33 Introducing the SMT ZyWALL 5 35 70 Series User s Guide 602 ...
Page 622: ...Chapter 35 WAN and Dial Backup Setup ZyWALL 5 35 70 Series User s Guide 622 ...
Page 628: ...Chapter 36 LAN Setup ZyWALL 5 35 70 Series User s Guide 628 ...
Page 634: ...Chapter 37 Internet Access ZyWALL 5 35 70 Series User s Guide 634 ...
Page 638: ...Chapter 38 DMZ Setup ZyWALL 5 35 70 Series User s Guide 638 ...
Page 642: ...Chapter 39 Route Setup ZyWALL 5 35 70 Series User s Guide 642 ...
Page 658: ...Chapter 41 Remote Node Setup ZyWALL 5 35 70 Series User s Guide 658 ...
Page 662: ...Chapter 42 IP Static Route Setup ZyWALL 5 35 70 Series User s Guide 662 ...
Page 700: ...Chapter 45 Filter Configuration ZyWALL 5 35 70 Series User s Guide 700 ...
Page 738: ...Chapter 50 Remote Management ZyWALL 5 35 70 Series User s Guide 738 ...
Page 746: ...Chapter 51 IP Policy Routing ZyWALL 5 35 70 Series User s Guide 746 ...
Page 766: ...766 ...
Page 770: ...Appendix A Hardware Installation ZyWALL 5 35 70 Series User s Guide 770 ...
Page 780: ...Appendix C Removing and Installing a Fuse ZyWALL 5 35 70 Series User s Guide 780 ...
Page 802: ...Appendix D Setting up Your Computer s IP Address ZyWALL 5 35 70 Series User s Guide 802 ...
Page 816: ...Appendix F Common Services ZyWALL 5 35 70 Series User s Guide 816 ...
Page 852: ...Appendix J Importing Certificates ZyWALL 5 35 70 Series User s Guide 852 ...
Page 856: ...Appendix K Legal Information ZyWALL 5 35 70 Series User s Guide 856 ...
Page 862: ...Appendix L Customer Support ZyWALL 5 35 70 Series User s Guide 862 ...