Copyright © 2013 Weidmüller Interface GmbH & Co. KG
58 / 103
All rights reserved. Reproduction without permission is prohibited.
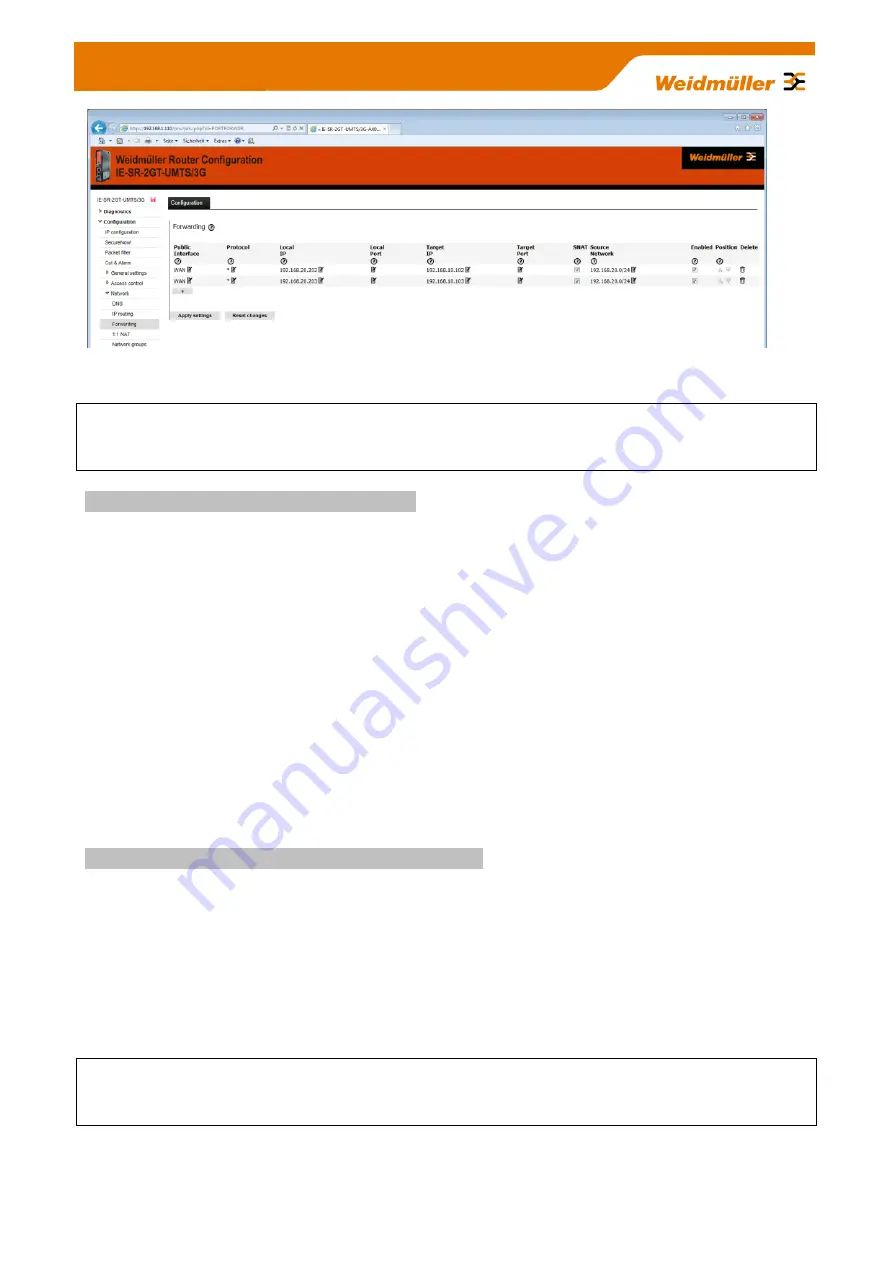
Figure A2-6
:: Forwarding table with activated IP address forwardings
Now the configuration of the Router is finished!
Note: Don’t forget to save the configuration after testing.
Testing the NAT masquerading feature
To test the NAT masquerading function you must use the tool Wireshark on the PC which receives the ping
request.
1. Run Wireshark on PC (connected to WAN port) with e.g. IP address 192.168.20.100
2. Start an new live capture session to display sent and received Ethernet packets
3.
Run a “ping” request from a device of Ethernet network
1
(e.g. 192.168.10.100) with destination address
192.168.20.100
4. Stop the Wireshark live capture session when the packets have been received and displayed.
Results showing in the Wireshark window:
The original sender of the ping request with IP address 192.168.10.100 is displayed as IP address
192.168.20.254 which is translated (masqueraded) by the Router.
If you disable NAT masquerading at WAN port and repeat the test then the original sender address
192.168.10.100 will be shown.
Testing the configured IP address forwardings
1.
Run a “ping” request from a device of Ethernet network
2
(e.g. 192.168.20.100) with destination address
192.168.20.202 (Note: Real IP address is 192.168.
10
.102)
Result:
The sent “ping” request should be answered correctly (displayed return address: 192.168.20.202)
2.
Run a “ping” request from a device of Ethernet network
2
(e.g. 192.168.20.100) with destination address
192.168.20.203 (Note: Real IP address is 192.168.
10
.103)
Result:
The sent “ping” request should be answered correctly (displayed return address: 192.168.20.203)
Note:
1. If you perform the ping test using PC’s please check your firewall configuration to ensure that ping re-
quests and echoes are allowed.






























