GTalarm3 User manual V-2022-05-24
48 |
E N
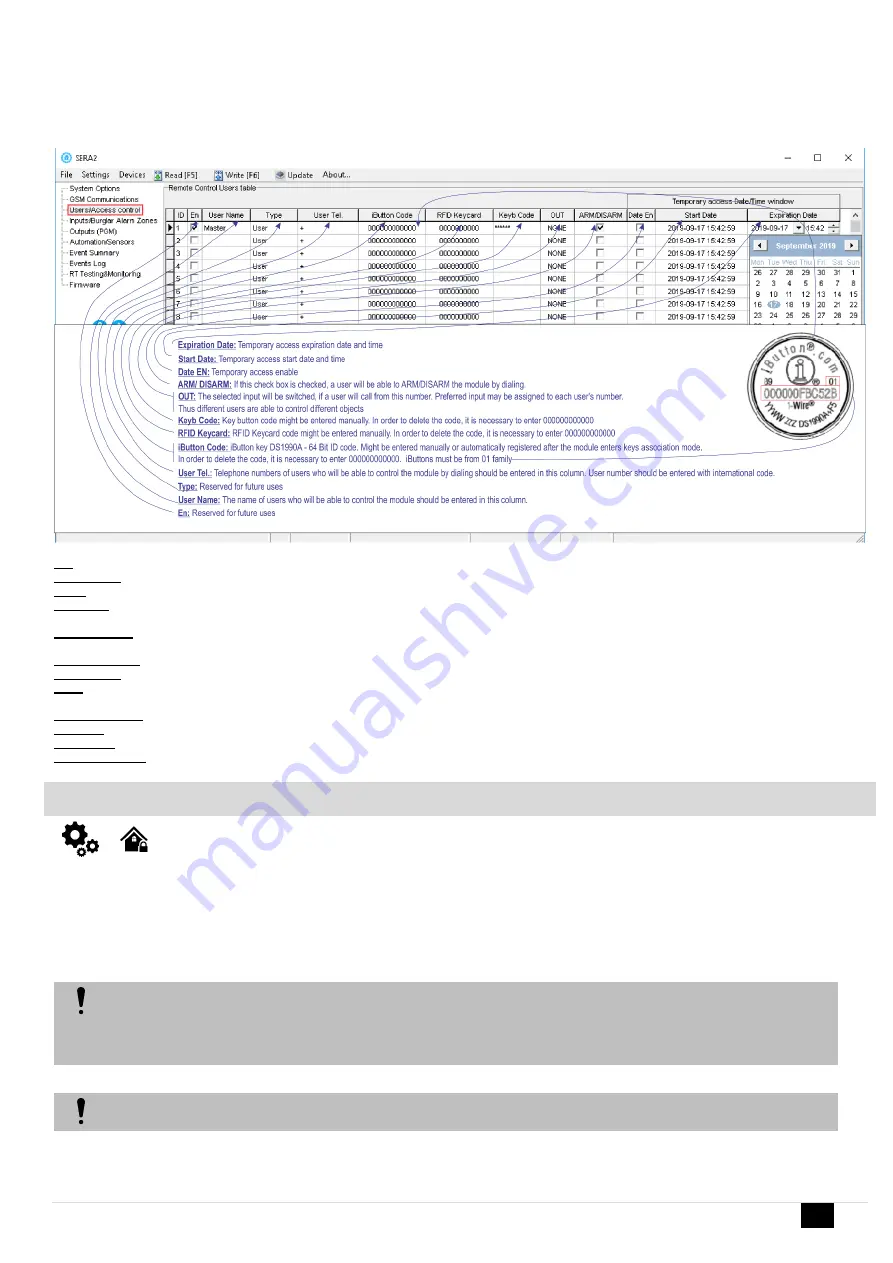
En:
Reserved for future uses
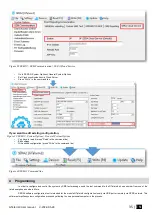
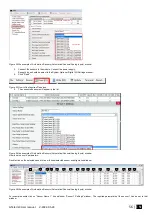
User Name:
The name of users who will be able to control the module should be entered in this column.
Type:
Reserved for future uses
User Tel.:
Telephone numbers of users who will be able to control the module by dialing should be entered in this column. User number should be
entered with international code.
iButton Code:
iButton key DS1990A - 64 Bit ID code. Might be entered manually or automatically registered after the module enters keys association
mode. In order to delete the code, it is necessary to enter 000000000000. iButtons must be from 01 family
RFID Keycard:
RFID Keycard code might be entered manually. In order to delete the code, it is necessary to enter 000000000000
Keyb Code:
Key button code might be entered manually. In order to delete the code, it is necessary to enter 000000000000
OUT:
The selected input will be switched, if a user will call from this number. Preferred input may be assigned to each user's number.
Thus different users are able to control different objects
ARM/ DISARM:
If this check box is checked, a user will be able to ARM/DISARM the module by dialing.
Date EN:
Temporary access enable
Start Date:
Temporary access start date and time
Expiration Date:
Temporary access expiration date and time
4.9
Reporting SMS&Dial in Case of Alarm Events
The system supports up to 8 user phone numbers identified as User 1 through 8 for monitoring purpose: receive alarm phone calls via GSM
connection and SMS text messages from the system. When the system is armed or disarmed by free of charge phone call or SMS text message, the
system sends a confirmation by SMS text message to user phone number that the system arming/disarming.
By default, once a user phone number is listed, the system ignores any incoming calls and SMS text messages from a non-listed phone number
as well as it rejects the SMS text messages containing wrong SMS password even from a listed user phone number. To permit/deny system
arming/disarming by phone call and SMS text message that contain a valid SMS password, configuration by SMS text message that contain a valid SMS
password from any phone number, please refer to the following configuration methods.
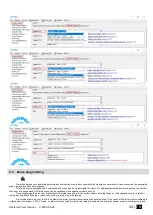
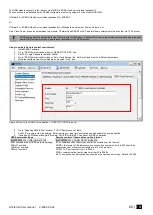
The system will NOT transmit any data to monitoring station while configuring the system remotely via GPRS network. However, during
the remote connection session, the data messages are queued up and transmitted to the monitoring station after the configuration
session is over. SERA2 software provides remote system configuration ability via Internet using TCP/IP server on SERA2 software. The
connection can be established on the system via GPRS network. After the remote system configuration is complete the session will
automatically expire in 20 minutes. Alternatively, the connection with the server can be terminated at any time by sending an SMS text
message. Terminate the connection with server SMS SMS text message content: ….
NEVER add a phone number of the device’s SIM card as a user phone number!