36
Chapter 3. Installing Red Hat Enterprise Linux WS
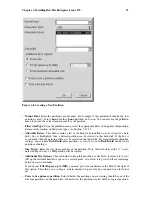
If you choose
Medium
, your firewall will not allow remote machines to have access to certain
resources on your system. By default, access to the following resources are not allowed:
•
Ports lower than 1023 — the standard reserved ports, used by most system services, such as
FTP
,
SSH
,
telnet
, and
HTTP
•
The NFS server port (2049)
•
The local X Window System display for remote X clients
•
The X Font server port (by default,
xfs
does not listen on the network; it is disabled in the font
server)
If you want to allow resources such as
RealAudio™
while still blocking access to normal system
services, choose
Medium
. Select
Customize
to allow specific services through the firewall.
No firewall
No firewall provides complete access to your system and does no security checking. Security
checking is the disabling of access to certain services. This should only be selected if you are
running on a trusted network (not the Internet) or plan to do more firewall configuration later.
Choose
Customize
to add trusted devices or to allow additional incoming services.
Trusted Devices
Selecting any of the
Trusted Devices
allows access to your system for all traffic from that device;
it is excluded from the firewall rules. For example, if you are running a local network, but are
connected to the Internet via a PPP dialup, you can check
eth0
and any traffic coming from your
local network will be allowed. Selecting
eth0
as trusted means all traffic over the Ethernet is
allowed, put the ppp0 interface is still firewalled. If you want to restrict traffic on an interface,
leave it unchecked.
It is not recommended that you make any device that is connected to public networks, such as
the Internet, a
Trusted Device
.
Allow Incoming
Enabling these options allow the specified services to pass through the firewall. Note, during a
workstation installation, the majority of these services are
not
installed on the system.
DHCP
If you allow incoming DHCP queries and replies, you allow any network interface that uses
DHCP to determine its IP address. DHCP is normally enabled. If DHCP is not enabled,
your computer can no longer get an IP address.
SSH
S
ecure
SH
ell (SSH) is a suite of tools for logging into and executing commands on a remote
machine. If you plan to use SSH tools to access your machine through a firewall, enable this
option. You need to have the
openssh-server
package installed in order to access your
machine remotely, using SSH tools.
Telnet
Telnet is a protocol for logging into remote machines. Telnet communications are unen-
crypted and provide no security from network snooping. Allowing incoming Telnet access
is not recommended. If you do want to allow inbound Telnet access, you will need to install
the
telnet-server
package.
Summary of Contents for ENTERPRISE LINUX WS 2.1 -
Page 1: ...Red Hat Enterprise Linux WS 2 1 Red Hat Enterprise Linux WS Installation Guide...
Page 10: ......
Page 18: ...8 Chapter 1 Steps to Get You Started...
Page 72: ......
Page 74: ...64 Appendix A Removing Red Hat Enterprise Linux WS...
Page 86: ...76 Appendix C Troubleshooting Your Installation of Red Hat Enterprise Linux WS...
Page 102: ...92 Appendix D An Introduction to Disk Partitions...
Page 110: ......