Chapter 12: Command Line Interface (CLI)
231
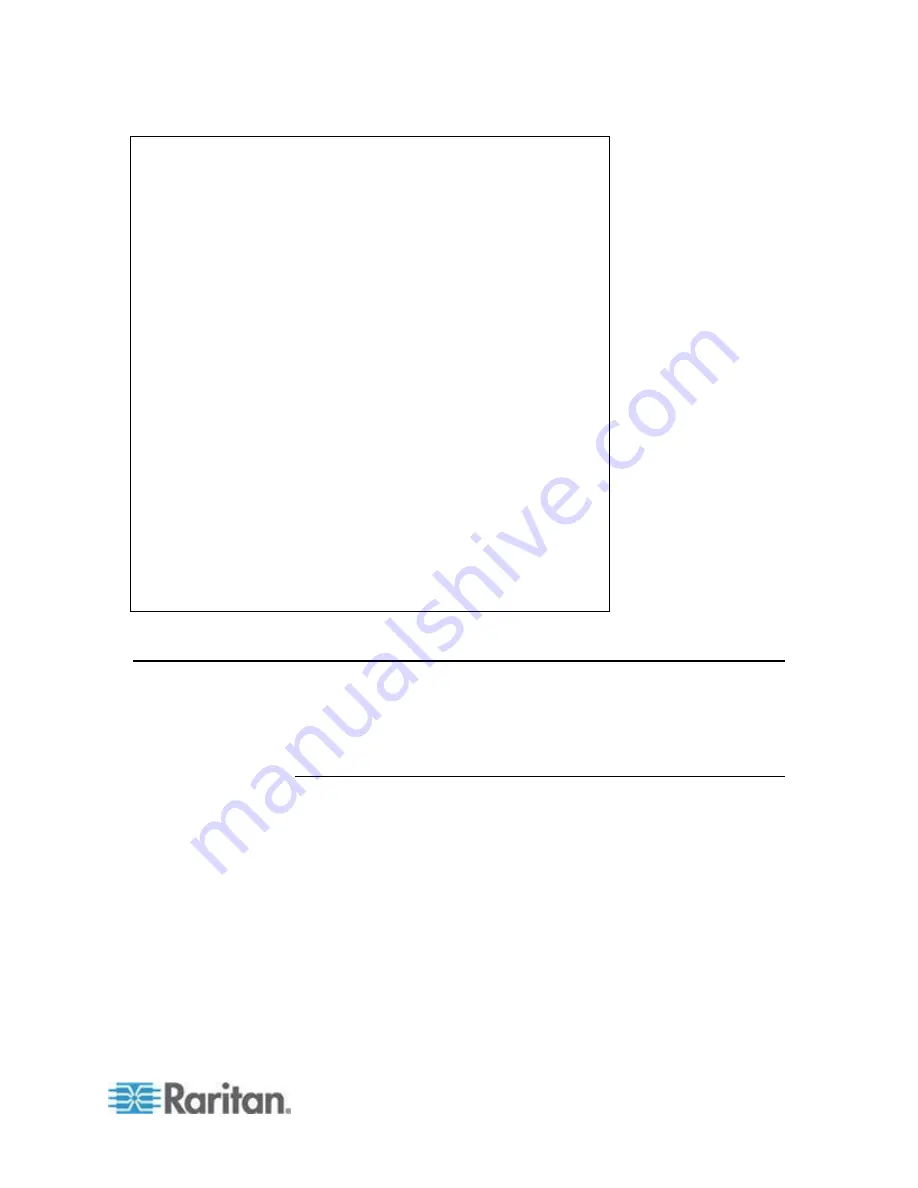
login as: Janet
Password:
Authentication successful.
----------------------------------------------------
------------
Welcome to the KSX II [Model: KSX2]
UnitName:KSX II FirmwareVersion:3.0.0.5.1
Serial:WACEA00008
IP Address:192.168.51.194 UserIdletimeout:99min
----------------------------------------------------
-------------
Port Port Port Port
No. Name No. Name
1 - Port1 [U] 2 - Port2 [U]
3 - Port3 [U] 4 - Port4 [U]
Current Time: Wed Sep 20 16:05:50 2006
Janet >
Navigation of the CLI
Before using the CLI, it is important to understand CLI navigation and
syntax. There are also some keystroke combinations that simplify CLI
use.
Completion of Commands
The CLI supports the completion of partially-entered commands. After
entering the first few characters of an entry, press the Tab key. If the
characters form a unique match, the CLI will complete the entry.
If no match is found, the CLI displays the valid entries for that level.
If multiple matches are found, the CLI displays all valid entries.
Enter additional text to make the entry unique and press the Tab key to
complete the entry.