V
V
P
P
N
N
Q
Q
o
o
S
S
W
W
i
i
r
r
e
e
l
l
e
e
s
s
s
s
R
R
o
o
u
u
t
t
e
e
r
r
153
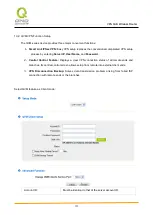
IPSec Setup
If there is any encryption mechanism, the encryption mechanism of these two VPN tunnels must be
identical in order to create connection. And the transmission data must be encrypted with IPSec key,
which is known as the encryption "key". The device provides the IKE automatic encryption mode- IKE
with Preshared Key (automatic). By using the drop down menu, select the desired encryption mode as
illustrated below.
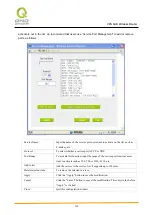
Encryption Management Protocol
:
When users set this VPN tunnel to use any encryption and authentication mode, users must set the
parameter of this exchange password with that of the remote.
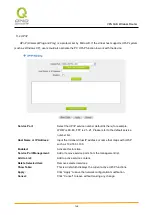
IKE Protocol
:
Click the shared key generated by IKE to encrypt and authenticate the remote user. If PFS (Perfect
Forward Secrecy) is enabled, the Phase 2 shared key generated during the IKE coordination will
conduct further encryption and authentication. When PFS is enabled, hackers using brute force to
capture the key will not be able to get the Phase 2 key in such a short period of time.
Summary of Contents for VPN QoS
Page 53: ...V VP PN N Q Qo oS S W Wi ir re el le es ss s R Ro ou ut te er r 52...
Page 57: ...V VP PN N Q Qo oS S W Wi ir re el le es ss s R Ro ou ut te er r 56...
Page 78: ...V VP PN N Q Qo oS S W Wi ir re el le es ss s R Ro ou ut te er r 77 8 2 Security Setting...
Page 88: ...V VP PN N Q Qo oS S W Wi ir re el le es ss s R Ro ou ut te er r 87 9 1 Bandwidth Management...
Page 115: ...V VP PN N Q Qo oS S W Wi ir re el le es ss s R Ro ou ut te er r 114 2 Add new rule click...
Page 123: ...V VP PN N Q Qo oS S W Wi ir re el le es ss s R Ro ou ut te er r 122 11 3 L7 QoS 1 Rule List...
Page 125: ...V VP PN N Q Qo oS S W Wi ir re el le es ss s R Ro ou ut te er r 124 2 Add New Rule Click...
Page 175: ...V VP PN N Q Qo oS S W Wi ir re el le es ss s R Ro ou ut te er r 174...
Page 195: ...V VP PN N Q Qo oS S W Wi ir re el le es ss s R Ro ou ut te er r 194...