ProSecure Unified Threat Management UTM10 or UTM25 Reference Manual
Monitoring System Access and Performance
11-39
v1.0, September 2009
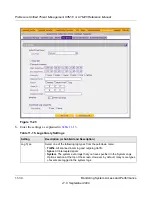
Scheduling and Generating Reports
The UTM lets you schedule and generate three types of reports:
•
Email Reports
. For each protocol (SMTP, POP3, and IMAP), the report shows, the following
information per day, both in tables and graphics:
–
Number of connections
–
Traffic amount in MB
–
Number of malware incidents
–
Number of files blocked
–
Number of blacklist violations (not applicable to POP3 and IMAP)
–
Number of e-mails captured by Distributed Spam Analysis (not applicable to IMAP).
•
Web Reports
. For each protocol (HTTP HTTPS, and FTP), the report shows the following
information per day, both in tables and graphics:
–
Number of connections
–
Traffic amount in MB
–
Number of malware incidents
–
Number of files blocked
–
Number of URLs blocked (not applicable to FTP)
•
System Reports
. The report shows IPS, application, and malware incidents:
–
The following IPS incident are shown per day, both in tables and graphics:
•
Number of detected port scans and top 10 scanned destination IP addresses by count
•
Number of Web attacks
•
Number of mail attacks
•
Number of database attacks
•
Number of application attacks
•
Number of network protocol attacks
•
Number of malware attacks
•
Number of miscellaneous attacks
•
Top 10 attacking IPS rule names by count, top 10 attacking source IP addresses by
count, and top 10 attacked destination IP addresses by count.