ProSecure Unified Threat Management UTM10 or UTM25 Reference Manual
11-4
Monitoring System Access and Performance
v1.0, September 2009
3.
Click
Apply
to save your settings.
4.
For the UTM25 only, click the
WAN2 Traffic Meter
submenu tab.
The WAN2 Traffic Meter
screen displays. This screen is identical to the WAN1 Traffic Meter screen (see
Figure 11-1 on
page 11-2
).
5.
For the UTM25 only, repeat
step 2
and
step 3
for the WAN2 interface.
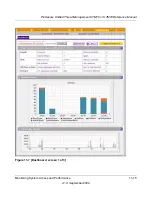
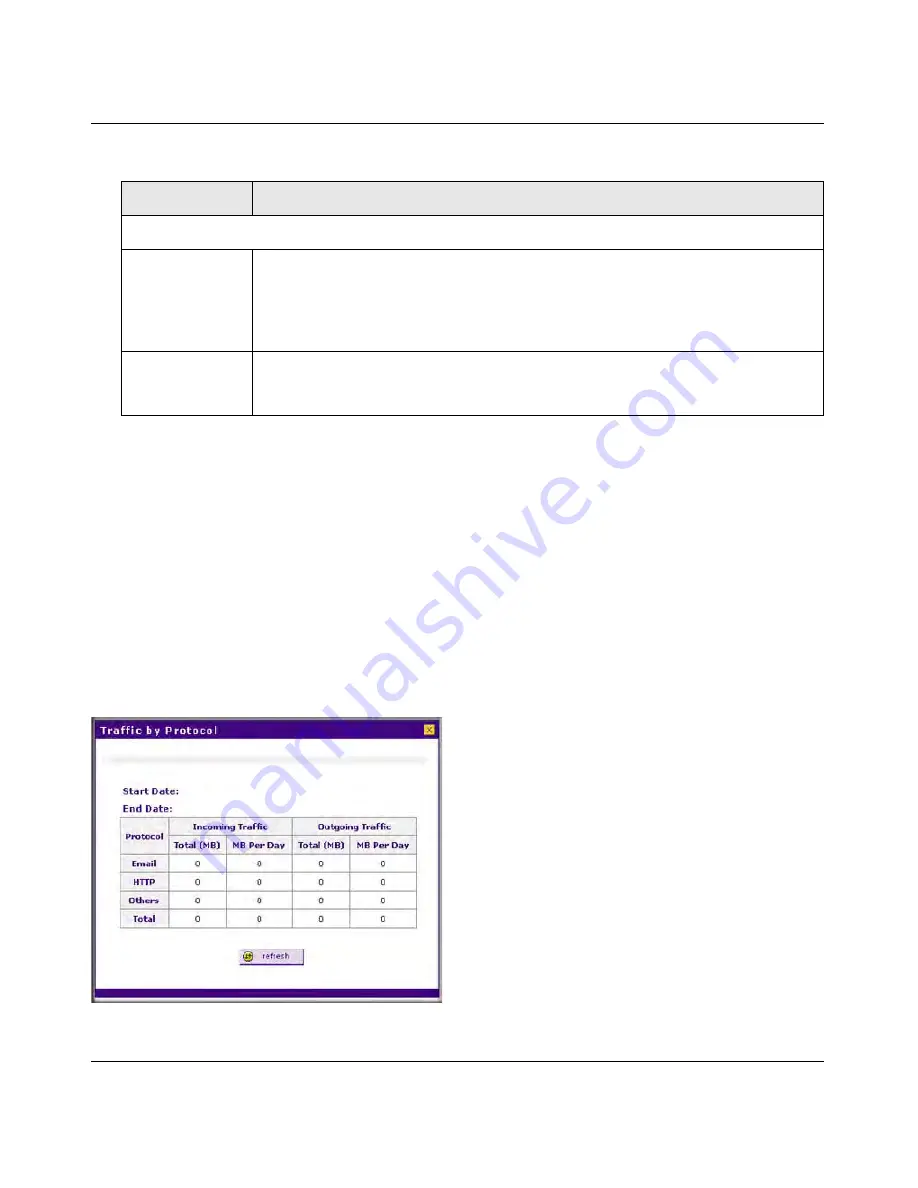
To display a report of the Internet traffic by type, click the
Traffic by Protocol
option arrow
at the
top right of the WAN1 Traffic Meter or WAN2 Traffic Meter screen (UTM25), or at the top right
of the WAN Traffic Meter screen (UTM10). The Traffic by Protocol screen appears in a popup
window. The incoming and outgoing volume of traffic for each protocol and the total volume of
traffic is displayed. Traffic counters are updated in MBs; the counter starts only when traffic
passed is at least 1 MB. In addition, the popup screen displays the traffic meter’s start end dates.
When Limit is reached
Block traffic
Select one of the following radio buttons to specify what action the UTM performs
when the traffic limit has been reached:
•
Block All Traffic
. All incoming and outgoing Internet and e-mail traffic is blocked.
•
Block All Traffic Except E-Mail
. All incoming and outgoing Internet traffic is
blocked but incoming and outgoing e-mail traffic is still allowed.
Send e-mail alert
An e-mail alert is sent when traffic is blocked. Ensure that e-mailing of logs is
enabled on the Email and Syslog screen (see
“Configuring and Activating System,
E-mail, and Syslog Logs” on page 11-6
).
Figure 11-2
Table 11-1. WAN Traffic Meter Settings (continued)
Setting
Description (or Subfield and Description)