Chapter 3 – RouteFinder Software Operation
Multi-Tech RouteFinder RF650VPN User Guide
101
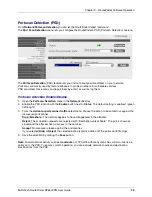
Set Packet Filter Rules
1.
Open the Rules menu in the Packet Filter directory.
2.
From the From (Client) select menu, select the network from which the information packet must be
sent for the rule to match. At From (Client): you can also select network groups.
The selection Any matches all IP addresses, regardless of whether they are officially assigned
addresses, or so-called private addresses according to RFC1918. The initial From (Client):
select options are {Private Network - RFC1918}, Any, and PPTP-Pool.
3.
From the Service select menu, select the service that is to be matched with the rule. The Service
menu lists the predefined services as well as those you have defined. With the help of these services,
the information traffic to be filtered can be precisely defined. The default entry Any selects all
combinations of protocols and parameters (e.g., ports). The Service selections include {netbios},
{ping}, {traceroute}, Any, DNS, FTP, FTP-CONTROL, HBCI, HTTP, HTTPS, IDENT, NEWS,
POP3, SMTP, SNMP, Telnet, netbios-dgm, netbios-ns, and netbios-ssn.
4.
Select the network which the information packet must be sent to for the rule to match from the To
(Server) select menu. At the To (Server) menu you can also select network groups.
The selection Any, applies to all IP addresses, regardless of whether they are officially assigned
addresses or so-called private addresses according to RFC1918. The initial To (Server):
select options are {Private Network - RFC1918}, Any, and PPTP-Pool.
5.
In Action, select the action (Allow, Drop, or Deny) that the packet filter executes if the rule matches:
Allow: all packets that match this rule are let through.
Drop: all packets that meet this condition are blocked, but do not appear in the log. To the host
sending the packet, it will appear as if the target address is not responding.
The action Drop is recommended for filter violations that constantly take place, are not security
relevant and only flood the LiveLog with meaningless messages (e.g., NETBIOS-Broadcasts from
Windows computers).
Deny: all packets that match this rule are blocked and visibly recorded as violations in the Filter
LiveLog. The host sending the packet will be informed that the packet has been rejected.
6.
Confirm your entry by clicking the Add button. After a successful definition, the rule is always added
to the end of the rule set table. Rules are added in the deactivated state, indicated by the red traffic
lights. You are then offered further functions for editing the packet filter rules.
Note: By default, new rules are created at the end of the table in the inactive state.
The rule only becomes effective if you assign the active state. Refer to the section on
Rule active/inactive in this chapter.