FortiGate-5001A Security System Guide
26
01-30000-0438-200800801
Planning the configuration
Quick Configuration Guide
Planning the configuration
Before beginning to configure your FortiGate-5001A security system, you need to
plan how to integrate the system into your network. Your configuration plan
depends on the operating mode that you select: NAT/Route mode (the default) or
Transparent mode.
NAT/Route mode
In NAT/Route mode, the FortiGate-5001A security system is visible to the
networks that it is connected to. Each interface connected to a network must be
configured with an IP address that is valid for that network. In many
configurations, in NAT/Route mode all of the FortiGate interfaces are on different
networks, and each network is on a separate subnet.
You would typically use NAT/Route mode when the FortiGate-5001A security
system is deployed as a gateway between private and public networks. In the
default NAT/Route mode configuration, the FortiGate-5001A security system
functions as a firewall. Firewall policies control communications through the
FortiGate-5001A security system. No traffic can pass through the
FortiGate-5001A security system until you add firewall policies.
In NAT/Route mode, firewall policies can operate in NAT mode or in Route mode.
In NAT mode, the FortiGate firewall performs network address translation before
IP packets are sent to the destination network. In Route mode, no translation
takes place.
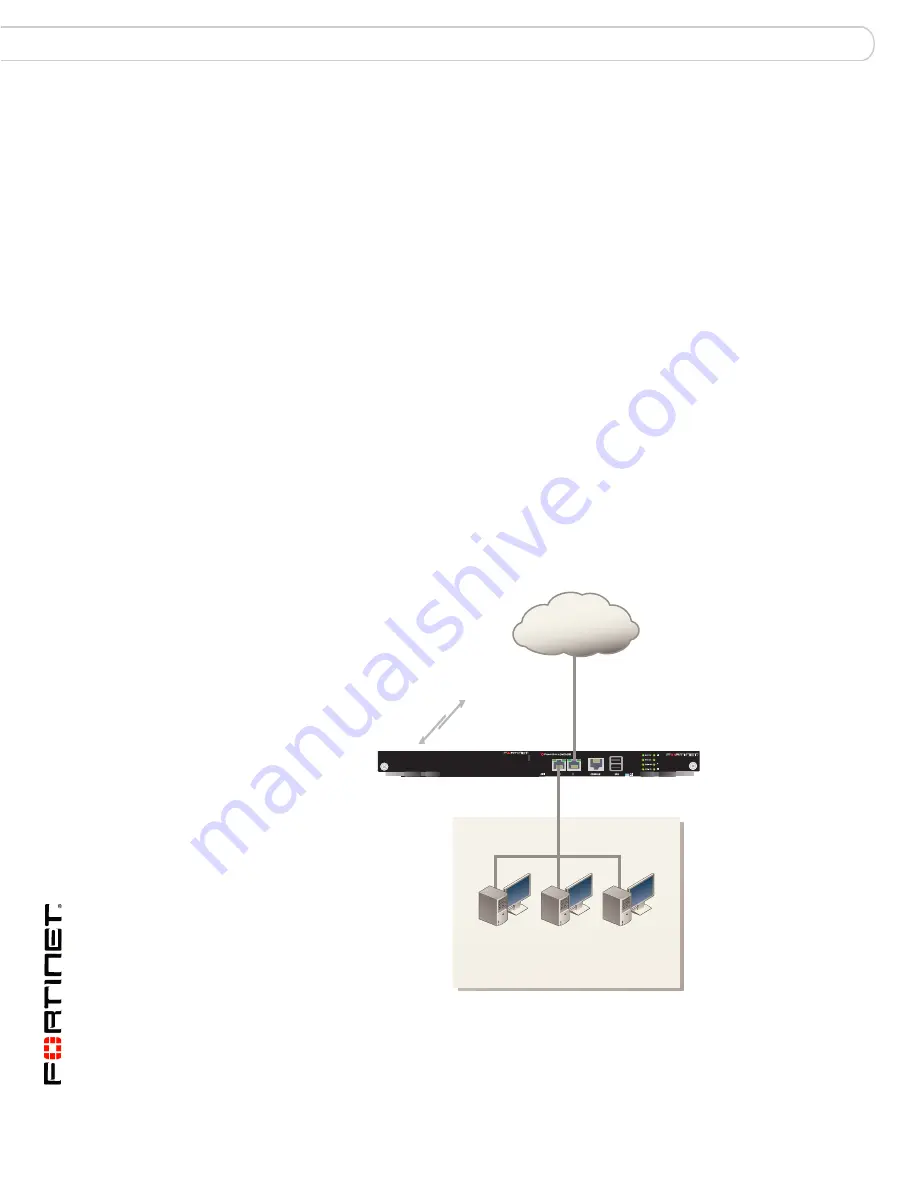
Figure 8: Example FortiGate-5001A board operating in NAT/Route mode
FortiGate-5001A board
in NAT/Route mode
port1
192.168.1.99
NAT mode policies
controlling traffic between
internal and external
networks.
port2
204.23.1.2
Internet
Internal Network































