152
Login Script on Windows Platforms
There are three ways of doing this: by using a customized remote
installation JAR package, by using a customized MSI package, or by
using the non-JAR approach.
Using the Customized Remote Installation JAR Package
1.
Run F-Secure Policy Manager Console.
2.
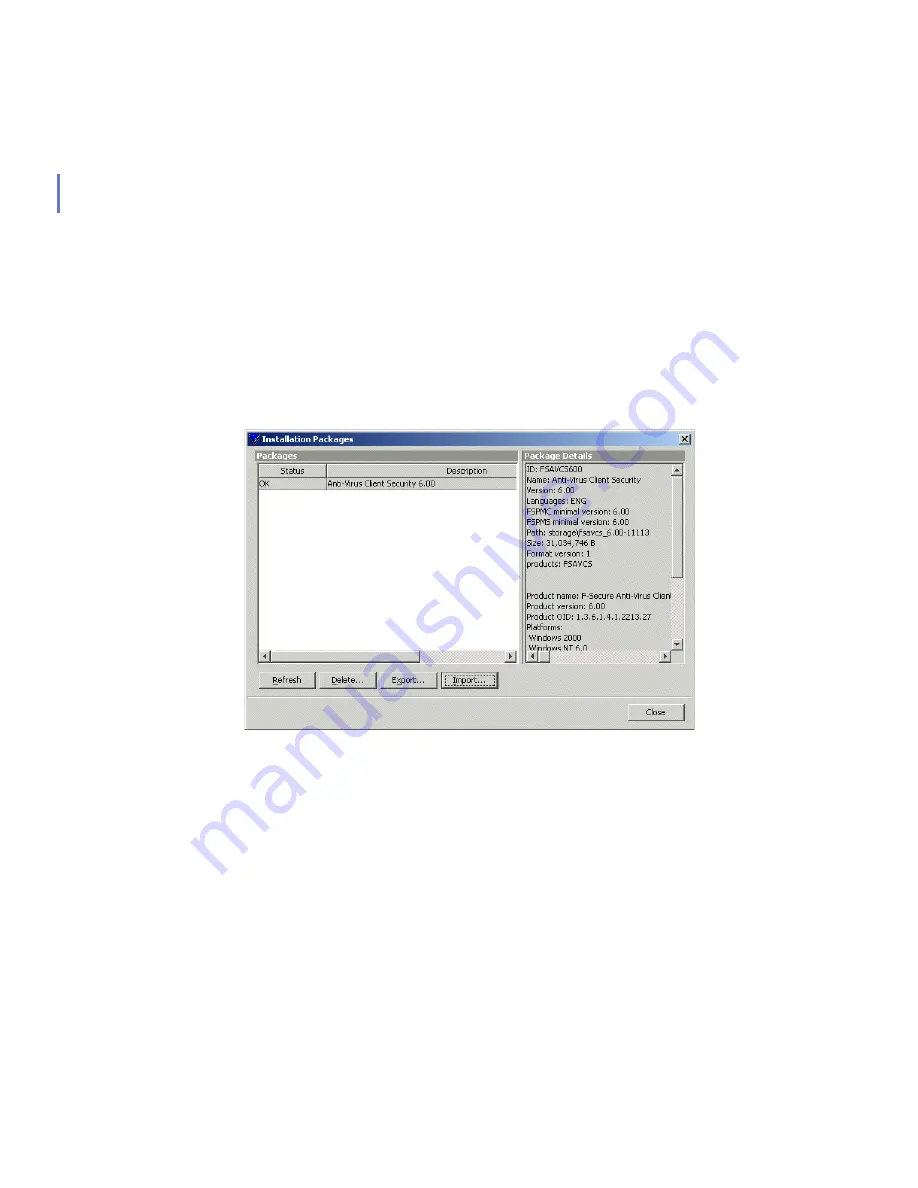
Choose
Installation Packages
from the
Tools
menu. This will open the
Installation Packages
dialog box.
3.
Select the installation package that contains the products you want to
install, and click
Export
.
4.
Specify the file format,
JAR
or
MSI
, and the location where you want
to save the customized installation package. Click
Export
.
5.
Select the products you want to install (F-Secure Management Agent
will be installed by default). Click
Next
to continue.
6.
Choose to accept the default policy, or specify which host or domain
policy should be used as an anonymous policy. Click
Next
to
continue.
Summary of Contents for CLIENT SECURITY 7.00
Page 1: ...F Secure Client Security Administrator s Guide...
Page 10: ...10 ABOUT THIS GUIDE Overview 11 Additional Documentation 13...
Page 41: ...CHAPTER2 41 Click Next to continue...
Page 75: ...CHAPTER3 75 Real Time Scanning Figure 3 10 Settings Real Time Scanning page...
Page 78: ...78 Manual Scanning Figure 3 11 Settings Manual Scanning...
Page 82: ...82 Spyware Control Figure 3 12 Settings Spyware Control...
Page 88: ...88 Firewall Security Levels Figure 3 15 Settings Firewall Security Levels...
Page 91: ...CHAPTER3 91 Firewall Rules Figure 3 16 Settings Firewall Rules...
Page 229: ...229 8 UPGRADING SOFTWARE Overview Upgrading Software 230...
Page 278: ...278 A APPENDIX Modifying PRODSETT INI Overview 279 Configurable Prodsett ini Settings 279...
Page 292: ...292 B APPENDIX E mail Scanning Alert and Error Messages Overview 293...
Page 297: ...297 GLOSSARY...






























